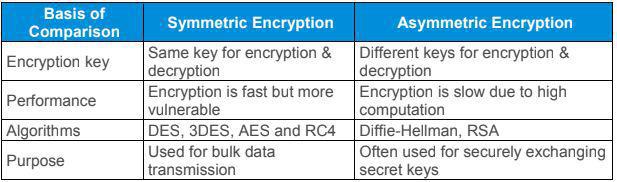
Asymmetric vs Symmetric Encryption
What is the difference between Symmetric and Asymmetric Encryption?
I'm having a bit of a tough time myself telling them apart. To begin, Professor Messer states that Symmetric encryption:
Is a single, shared key that you encrypt and decrypt with. If it gets out, you'll need another key. It is sometimes known as a shared secret because it's the secret we all need to know to decrypt the info. It doesn't scale very well and can be challenging to distribute, but it's very fast to use.
I'm having a bit of a tough time myself telling them apart. To begin, Professor Messer states that Symmetric encryption:
Is a single, shared key that you encrypt and decrypt with. If it gets out, you'll need another key. It is sometimes known as a shared secret because it's the secret we all need to know to decrypt the info. It doesn't scale very well and can be challenging to distribute, but it's very fast to use.



