
Scanning and Identifying Network Nodes
In this lab, we will use common network tools, such as local commands and the Nmap network mapper, to discover other hosts on the local network. Next, we will conduct a banner grabbing exercise to identify specific services on the hosts. Finally, we will use DNS tools to gather name resolution information.
Identify local network configuration
Determine the configuration of the local host and its subnet, using tools such as ifconfig, ip, arp, netdiscover, and pathping and run the scans from the KALI Linux VM and the DC1 Windows Server.
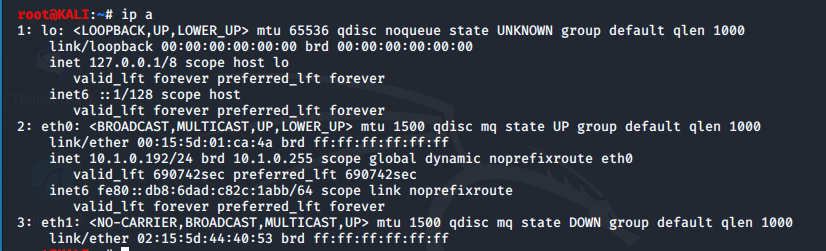
We'll display the same information using the newer ip a tool.
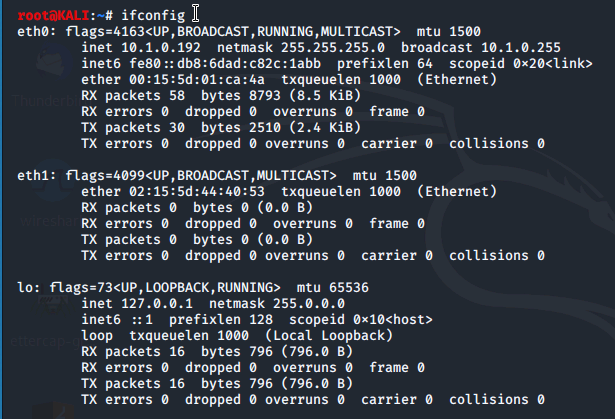
Using the terminal in a Kali Linux machine, we run ifconfig to display the interface configuration, noting the ip address assigned to the eth0 interface.
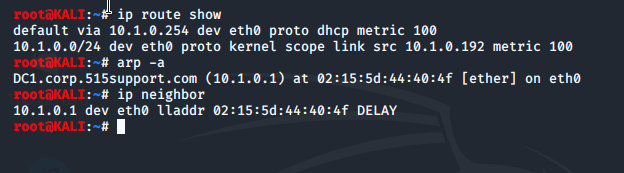
Next, we run commands to show the default gateway, the ARP cache to display other hosts local to the subnet, and similar information using the newer ip neighbor
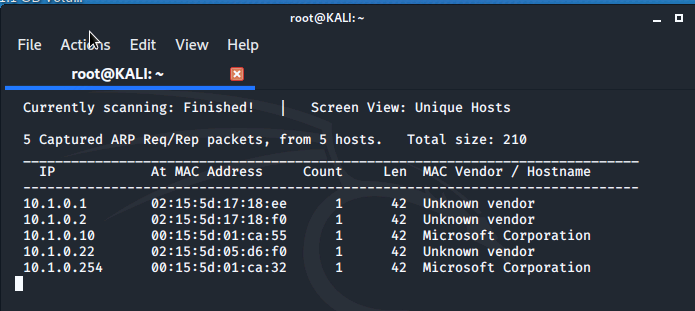
Using the netdiscover command, we scan the network and the results discover several other hosts connected to the vLOCAL
We then switch over to the DC1 machine and open up the command prompt with admin permissions and display the ip address configuration for
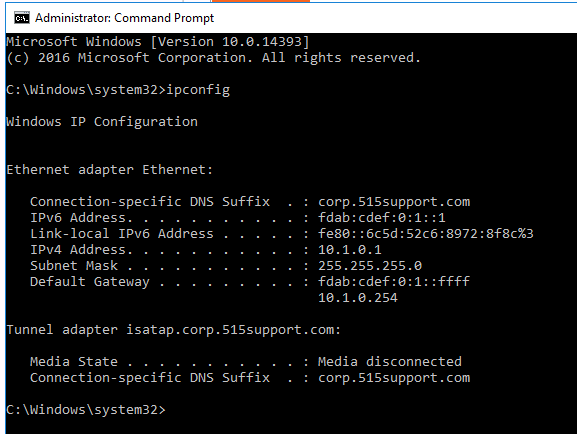
We then test the reliability (packet loss) and latency (delay) of the connection between the DC1 VM and the PT1-Kali
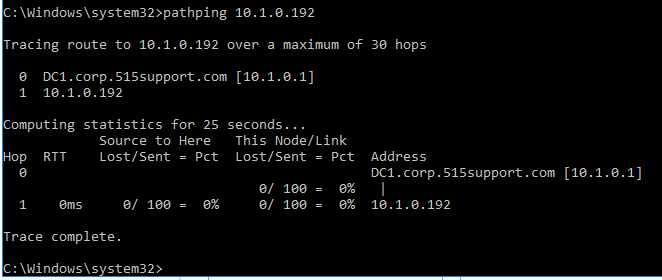
The two machines are not very far apart on the network—on the same subnet in fact. If you run pathping against network nodes that have several routers between them, the utility displays lost packets along the route, which helps to clarify where network communications might be unreliable. For example, from a Windows computer with Internet access, you could run pathping 8.8.8.8 to trace the route to the servers running Google's DNS service.
Use nmap to Discover Hosts
From a penetration tester or threat actor perspective, network reconnaissance will typically aim to discover the following:
- Default gateway (the router connecting the subnet to other networks).
- DNS server (used to resolve host names on the network).
- Whether any network directory/authentication and application servers are present.
- Whether any host/client access devices are present.
- Whether any other types of devices (embedded systems or appliances) are present.
We will use nmap from the PT1-Kali VM to report this information for this network.
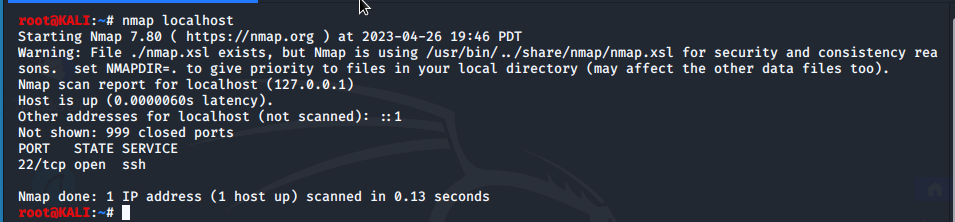
Using that command we can see that port 22 is open. We then run a basic network
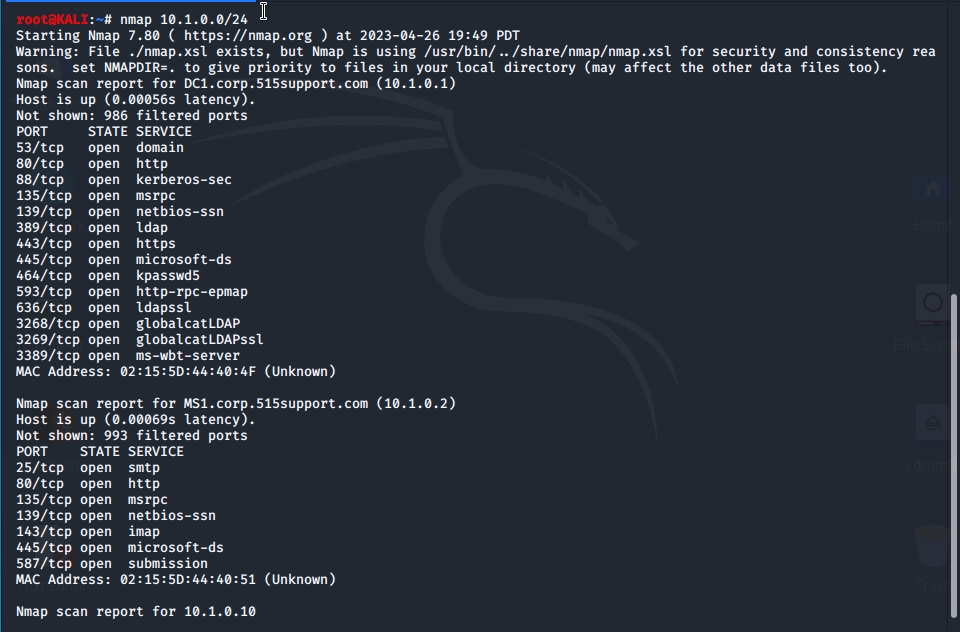
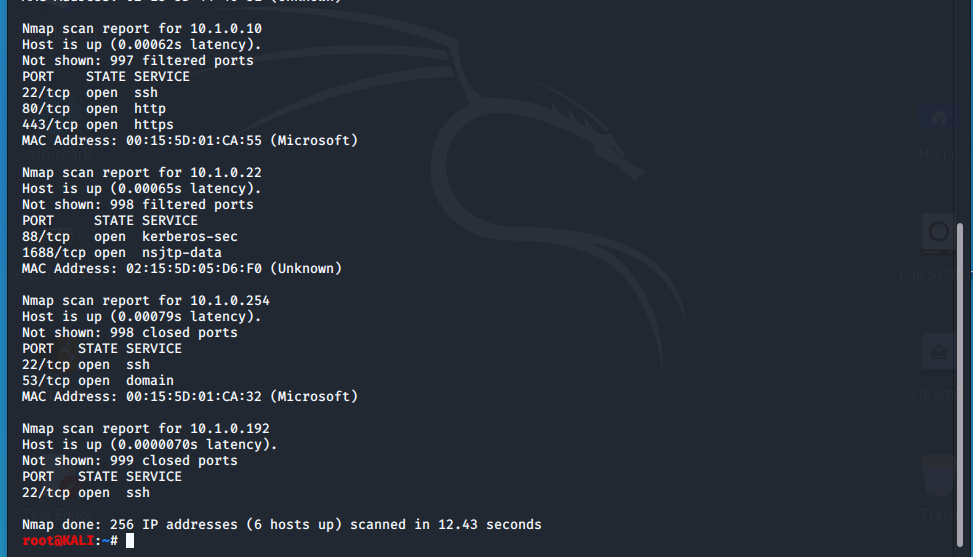
We then use the -sS syntax for a fast
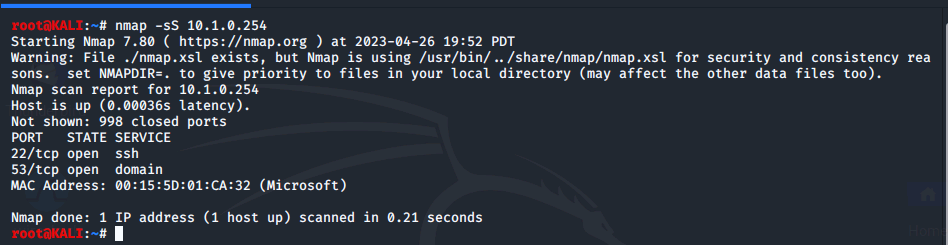
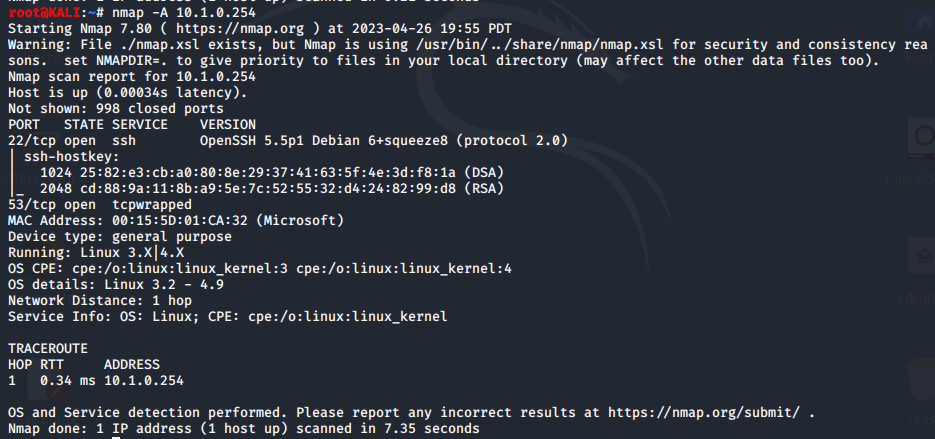
Here, we can clearly see the SSH and DNS services are running on this VM. Using the -A syntax we identify more about the host like the operating
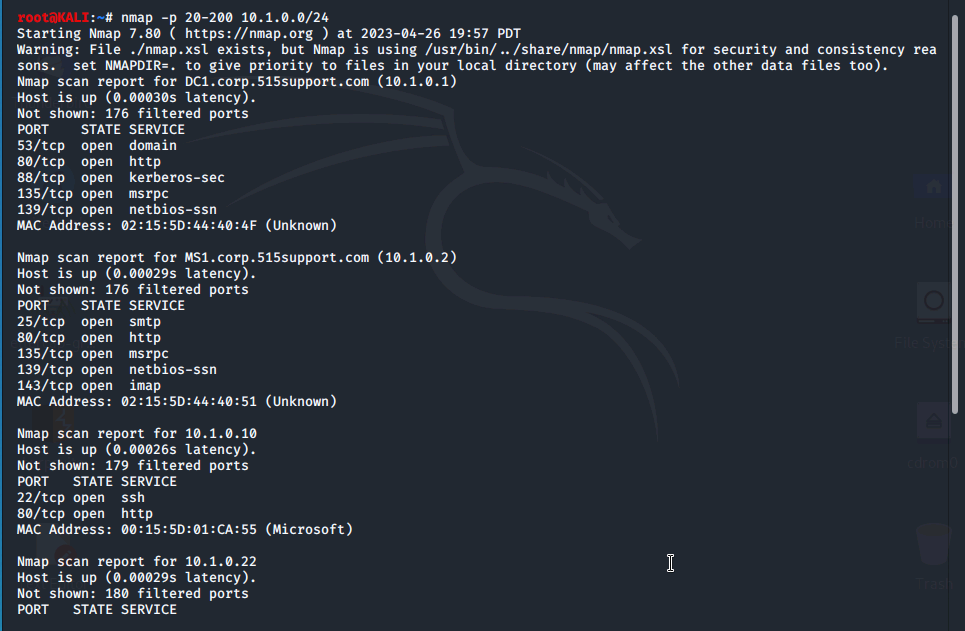
With the following command we can look for specific ports. Here we'll be looking for ports between
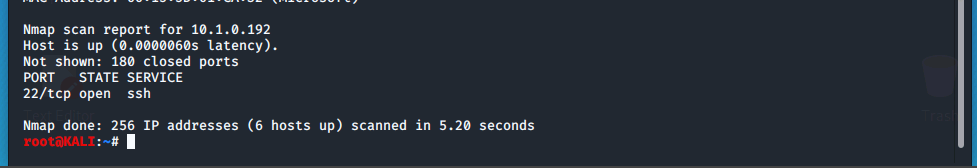
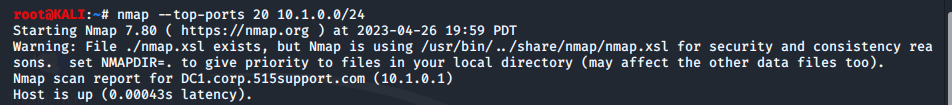
This next command shows us the top 20 most common
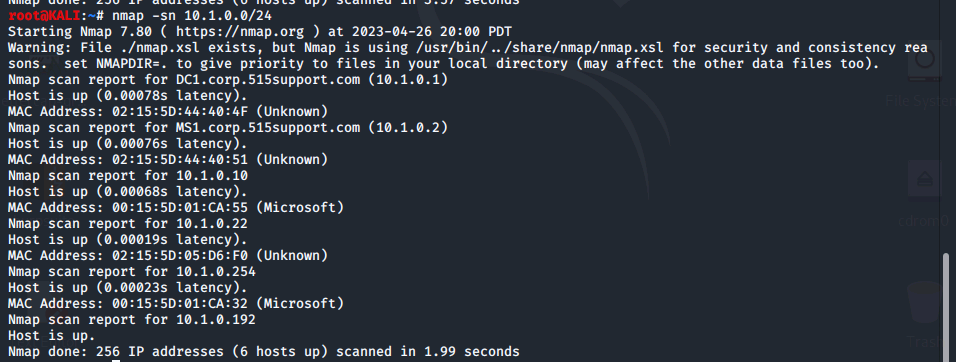
Finally, this last command quickly scans the network for hosts that are up or down on the
Banner Grab with cURL and Firefox
Banner grabbing is a way of identifying service versions. This information helps attackers select potentially vulnerable machines. The information also helps administrators confirm that all services on the network are of a certain version.
Basic tools can be used to grab banners. In this activity, we will use cURL and Firefox.
We use the following command to connect to the 10.1.0.1 HTTP server using cURL and we see that the web server service and cersion used on the target VM is IIS
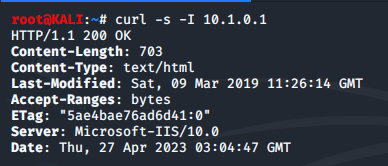
We used port scans in earlier activities to determine that the 10.1.0.1 virtual machine is running a web service. With this cURL command, we have determined the software type and version for the web server service.
In kali we type firefox plus an ip address to bring up a web site.
Query DNS
DNS provides name resolution to internal networks as well as the Internet. DNS is used any time a user or application refers to a host by name. DNS queries name records to find the IP address associated with a hostname or fully qualified domain name. These name records can also reveal information about how a network is configured. In this task, we will gather DNS information by using the dig utility.
Here, we perform a reverse lookup on the default
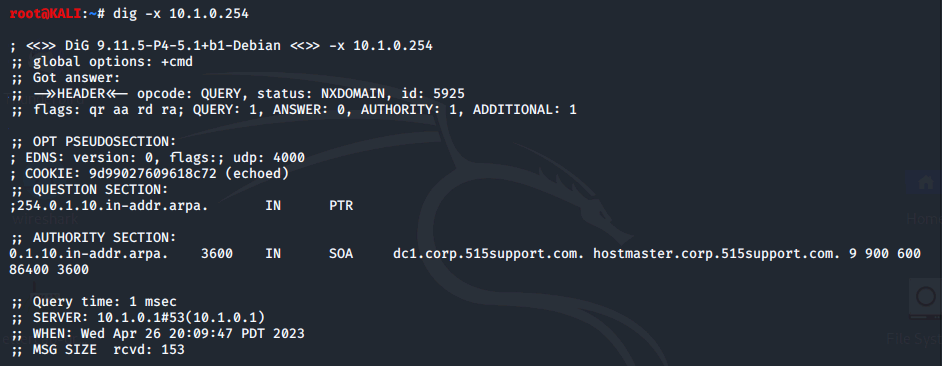
The ip address of the DNS server that answers the query is 10.1.0.1 and the fully-qualified domain name (FQDN) of the VM found at 10.1.0.2 is MS1.corp.515support.com.
Next we display the authorative DNS server for the
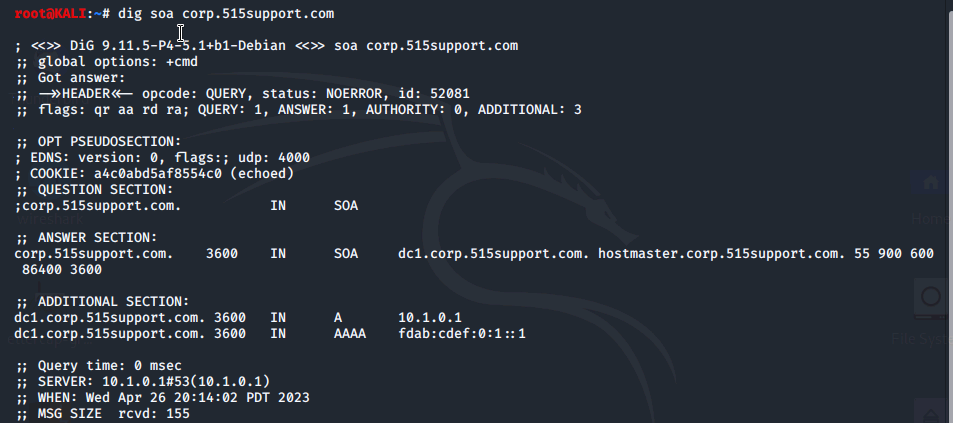
The query returns the FQDN of the DNS server responsible for the domain (DC1.corp.515support.com) and its host record (10.1.0.1). It's also worth noting some of the flags shown:
- aa indicates that the answer is authoritative. The "AUTHORITY" section of the response is empty. Contents for this section are commonly omitted by name servers to reduce the size of responses.
- ra indicates that recursion is available; that is, this router will forward queries to other servers.
Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua.
Conclusion
We identified the Kali Linux and Windows servers, performed basic scans of the network, identified hosts and services, used banner grabbing to identify services, and gathered more DNS information.
An administrator might use the information to verify expected network and server configurations.
An attacker might use the information gather to check for old services that may be unpatched, to network in preparation for an attack, and to decide what servers to
0 Comments Add a Comment?