
Configuring a Firewall
We will configure a basic firewall rule on a Linux server to block port 80 (HTTP) traffic.
Next, we will reconfigure the server to accept HTTP connections, and then we will configure iptables logging for all traffic. Finally, you will display log file traffic.
Configure a Linux iptables firewall for HTTP connections
Using the terminal in our Kali VM, we start the Apache web service and verify it is running.
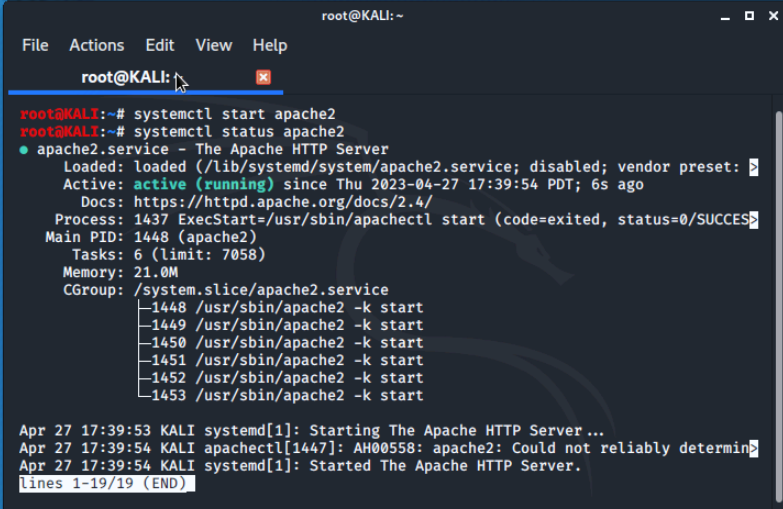
Then connect to the 515 support website using firefox in our LX1 VM.
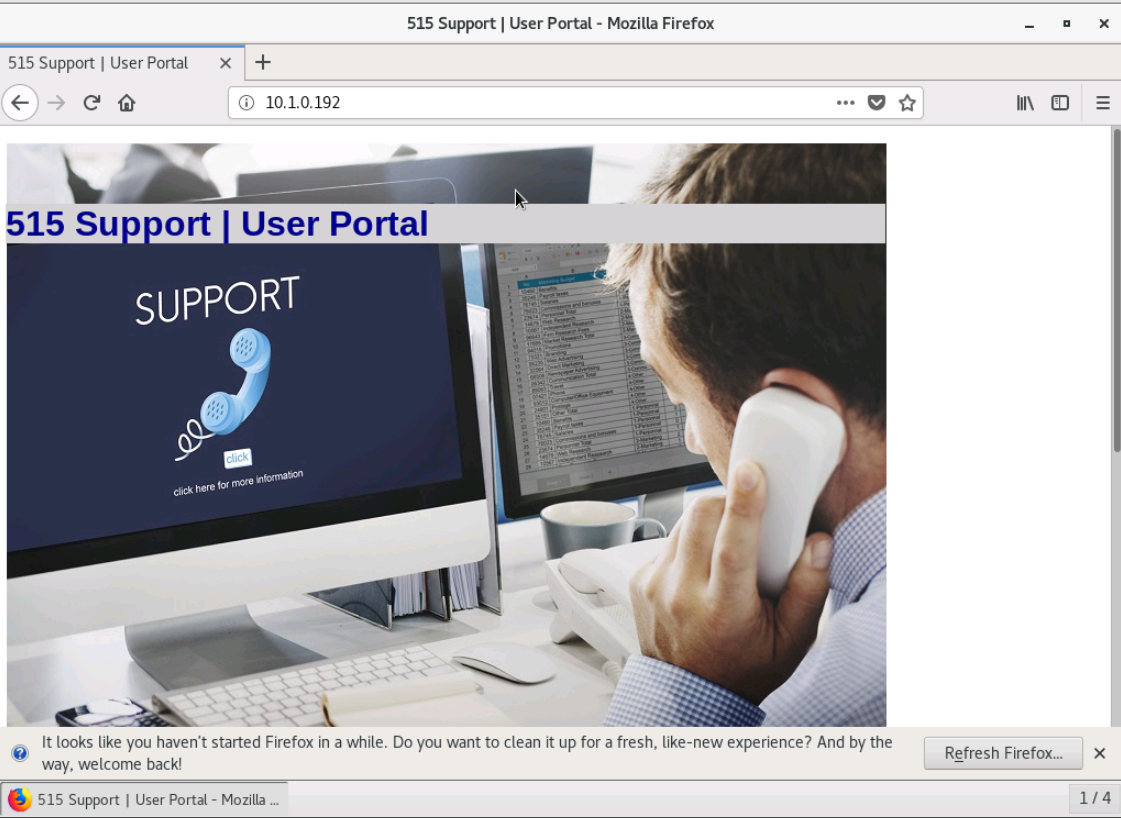
Switching back to our Kali VM, we do the following:
- Configure the iptables service to DROP inbound HTTP connections by port number 80.
- Display the iptables rules and observe that the HTTP service is specified by port number 80.
- Redirect the output of the iptables -S command to a text file
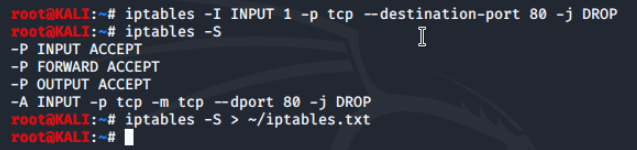
Moving back to our LX1 machine, we try to connect to the support website but the connection attempt fails because we added a rule to drop inbound packets for port 80.
Display iptables log files
We start by adding an iptable rule at line 1 so that connections to port 80 are accepted. Next, we enable iptables logging, and then display the iptables rules and we see that the destination port 80 ACCEPT and LOG rules are listed above the DROP rule. Firewall rules are processed in order. If we were to switch back to our LX1 machine and try to connect, the attempt would be successful.
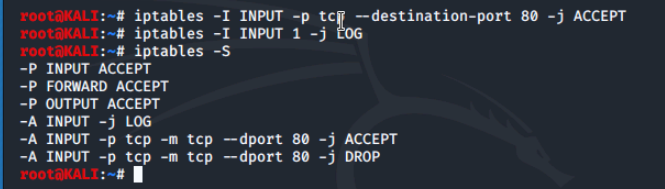
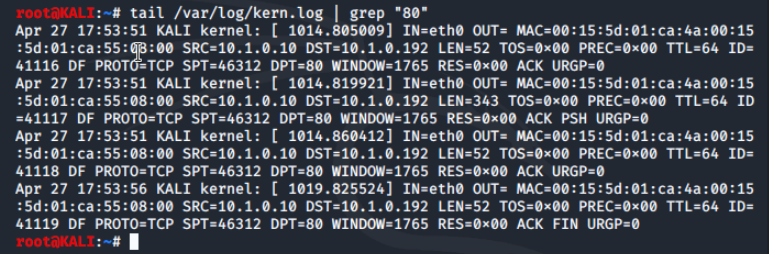
After attempting and successfully connecting to the website through our LX1 machine, we return to our kali VM and display destination port 80 traffic in the kern.log file using the tail command.
Conclusion
In conclusion, this lab was designed to test our understanding of and ability to configure a firewall on a Linux server. We were able to successfully block inbound port 80 traffic, reconfigure the server to accept HTTP connections, and then configure iptables logging for all traffic.
We observed that after adding a rule to drop inbound packets for port 80, our attempt to connect to the website failed. This demonstrated the importance of properly configuring the firewall rules to allow traffic to flow.
We also learned that iptables firewall rules are processed in the order in which they are listed, with the rules at the top being processed first. We were able to successfully log traffic processed by iptables by adding a LOG command to our rules.
Overall, this lab was a valuable learning experience that provided us with practical skills for securing web servers and understanding how firewall rules work.
Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua.
0 Comments Add a Comment?