
Auditing Passwords with a Password Cracking Utility
In this lab, we are auditing password quality to better teach fellow employees the importance of strong passwords. First, we send out an employee survey, asking seemingly harmless questions. The results are in the following table. Next, we add the results to a wordlist to be used as a source for password cracking utilities such as John the Ripper. Finally, we crack the passwords to demonstrate whether they expose the organization to authentication vulnerabilities.
Survey Results
Here is an excerpt from the email message:
Please fill out the following survey so that we can get to know you better and celebrate significant events!
- What is your birthday?
- What is your spouse's name?
- When is your anniversary?
- What is your pet's name?
We have documented the survey result in the table below:
| Name | Birthday | Spouse | Anniversary | Pet name |
|---|---|---|---|---|
| user01 | 06101988 | Mary | 05232010 | Max |
| user02 | 10141976 | Tim | 06011989 | no pet |
| user03 | 09081998 | Rick | 07032018 | Duke |
| user04 | 02081980 | George | 06142004 | Rover |
| user05 | 03121985 | Shawna | 12132010 | Spot |
| user06 | no response | no response | no response | no response |
Create the necessary accounts and passwords
Using the terminal in a Kali Linux machine we create the first user with the password
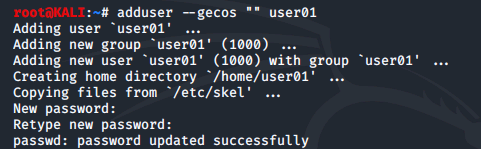
We then create additional accounts specified below using the same method:
| Username: | Password: |
|---|---|
| user02 | Password |
| user03 | Duke |
| user04 | george |
| user05 | $p0T |
| user06 | G00dPa$$w0rd |
Add probable passwords to the word list file
We then use the following command to extract the word list file

Then we use vim to open the file and enter the following passwords:
06101988
Password
Duke
george
$p0T
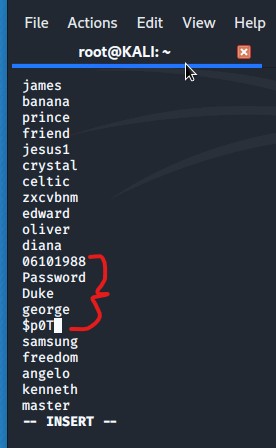
Run John to crack passwords
After saving and exiting the file, we run the following commands to create a text file of username and password hashes, then run the john command to crack
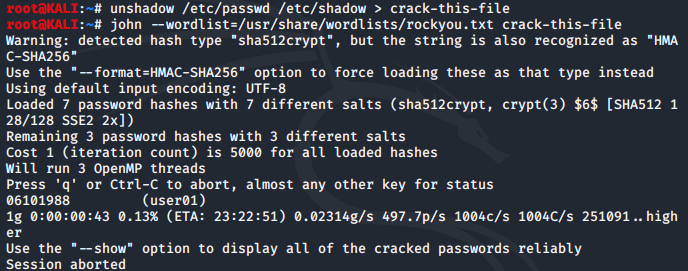
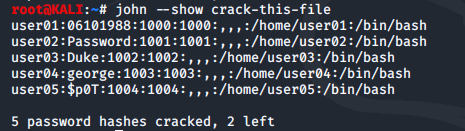
Running the john --show command shows us the usernames and passwords
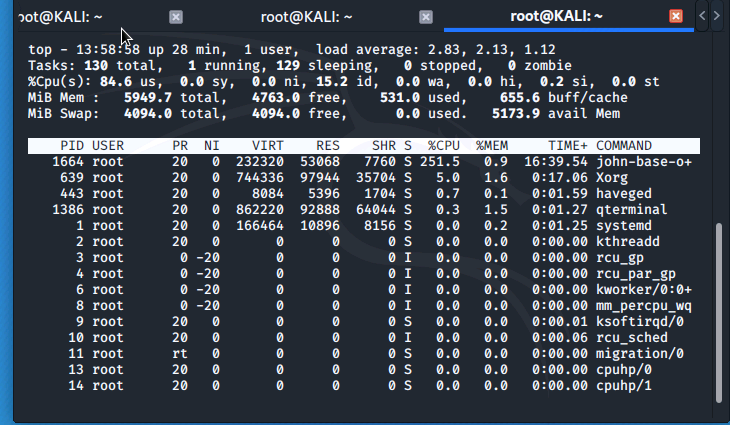
While john the ripper is still running, in a new tab we run the top command and can see that the that john is consuming most of the system's processing
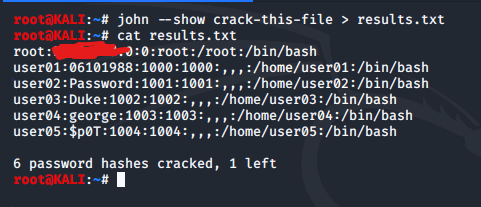
We redirect the results of john --show crack-this-file to a text file called results.txt. After running for some time, john also managed to crack the root user's
Conclusion
this lab helped me to better understand the importance of strong passwords and how easy it can be for someone to crack weak passwords. The survey results we obtained were used to create a wordlist that we added to John the Ripper, a password cracking tool. By combining the /etc/passwd and /etc/shadow files, we were able to audit the employee passwords and determine if they were vulnerable to attack.
Through this process, we discovered that several of the passwords were easily guessable, such as birthdays, pet names, and common words. It was surprising to see how quickly John the Ripper was able to crack some of the passwords, which really drove home the importance of using strong and complex passwords.
0 Comments Add a Comment?