
Using SQL Injection
In this lab, we will learn how to recognize database vulnerabilities to help us plan and carry out SQL injection attacks.
SQL Injection Attack
SQL (Structured Query Language) is the language used to access and manipulate databases. SQL Injection attacks occur when a user injects an SQL query using the front end web app. This injection attack allows a user to send a valid SQL Statement to the database to read/modify data or execute a command.
We'll start by accessing dvwa through http://10.1.16.9/dvwa

DVWA is an intentionally vulnerable PHP/MySQL web application used to practice and learn web application security.
First we need to change the severity level on this web application.
We'll log in using the username admin and the password password.
Then we'll click on DVWA Security and switch the script security from high to low
Now we'll switch over to the SQL Injection section and at the bottom right we see two buttons called View Help and View Source. It has information that is not always available. In this case we're told that there are five users in a table.


You can breakdown this source code to get a visual of why the database vulnerability exists in the "User ID" input box. The help section states that the 'id' variable is vulnerable to SQL injection.
After the user submits their input, a GET request is sent to collect form data. This shows the GET request takes in the 'id' parameter but this parameter is not validated which allows hackers to inject code into the SQL statement.
Note: Input validation is clear and simple guidance to enforce the handling of characters executed through an input box. Only properly formatted data should be sent to the database. Input validation should not be used as a primary method to prevent SQL injection, but it will reduce the influence of SQL injections on the database.
The next line below shows how the SQL query is constructed when user input is sent to the database.
"SELECT first_name, last_name FROM users WHERE user id = '$id'“; The web application then returns First Name: and Surname: for the corresponding ID which tells us the query was sent to the database and executed using the following statement. SELECT first_name, last_name FROM users WHERE user id = '1';

Blind SQL Injection
When exploiting a normal SQL injection we'll find that sometimes the database will display a visual output or even return an error that might tell us our SQL syntax is incorrect. Blind SQL injection is when we cannot visually see a response from the query sent to the database or we get a generic error page. These two types of SQL injections are virtually the same, the distinction between the two is in the database retrieval method.
This is the default view in the address bar.
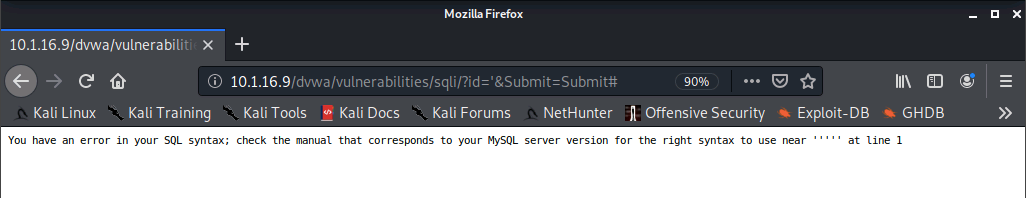
If we type in a single ' then the application returns an error with information that could assist us with crafting additional attacks.
Now, we'll switch over to SQL injection (Blind) tab in dvwa from the menu on the left and when we type in a single quotation mark the application does not display an error message or return any output.
Let's scroll down and click on View Help to see what kind of information we receive.

Blind SQL injection is a type of SQL injection using boolean logic where the query is sent using True or False questions and the answer will be based on the response from the web application.
Boolean is an algebraic logic system type with only one of two possible values of logic: "True" or "False"
- 1=1 (TRUE)
- 1=0 (FALSE)
The following boolean expression is always (TRUE). When we send the query to the database the database answers back with TRUE and returns all results.
We'll type in ' OR 1='1 into the User ID field and receive the following result.

0 Comments Add a Comment?