
Understanding Nmap Common Usage
In this lab, we'll learn about one of the most widely used network scanning tools, Nmap.
Nmap
Nmap is an open source network scanner and security auditing tool and is short for Network Mapper.
- Nmap uses raw network packets to determine what hosts are on a network and the operating system and services running on each host.
- Nmap runs on most operating systems including Windows, Mac, Linux, and various flavors of Unix.
- More information can be found at https://nmap.org/.
If we type in and run nmap in our Kali VM terminal, we see all of the options that nmap supports in this quick reference guide . We can also review the full documentation on the man page by using man nmap at the prompt.
There are many ways to specify a target for an nmap scan including hostname, IP address, or network range. Nmap can be used to scan a network for active hosts using what is called a ping sweep.
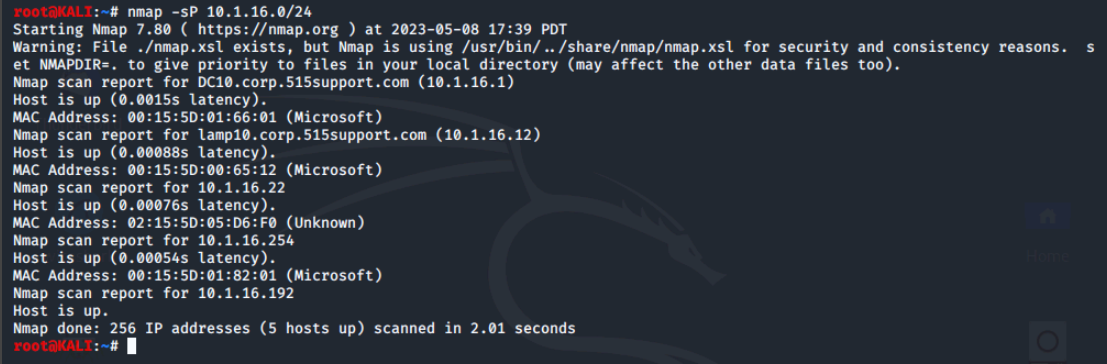
We'll try this out by running nmap -sP 10.1.16.0/24.
Let's look a little further at the LAMP server in the environment. We'll run the command nmap 10.1.16.12 to scan the LAMP server.
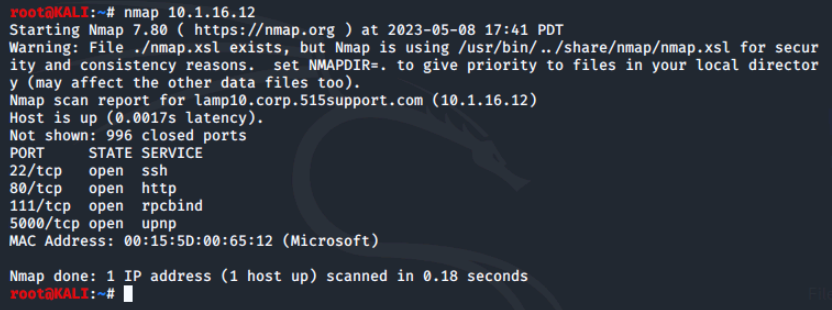
We can see that the LAMP server has 4 open ports.
By default, nmap only scans the top 1000 commonly used ports. If we want to scan all possible ports or only a particular port or range, we can use the -p option. For example to scan all 65535 possible ports we could use -p 1-65535 or a short cut of -p-.
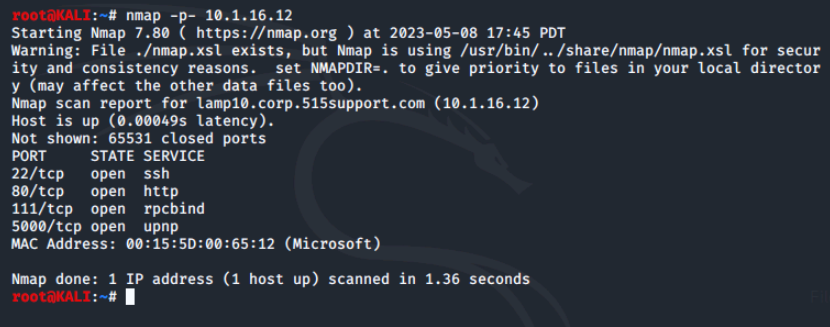
This returned the same results because this server does not use any uncommon ports. We can combine options on the command line to find additional information:
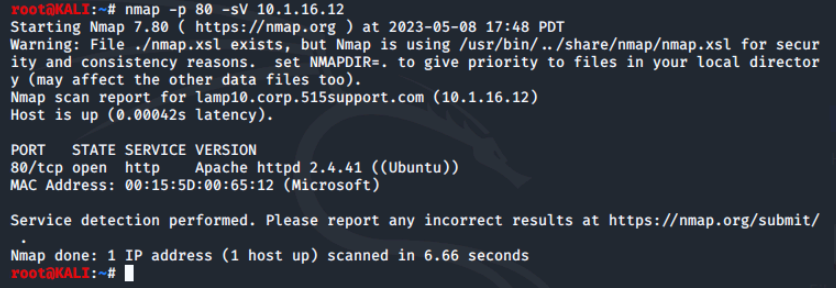
For example, we can determine the operating system of a target by using the -O option and can check the version of a particular service with the -sV option.
Let's see if we can find out more about the web server running on port 80.
Nmap Scan Types
Nmap supports multiple scan types:
- By default, nmap will perform a full TCP handshake as part of its scanning.
- Nmap also supports stealth modes such as the SYN scan. Nmap will only send a SYN packet to determine if a port is open.
If a SYN ACK response is received, nmap will assume the port is open and send an RST to tear down the connection before it is fully established in the hopes that the transaction will not be logged. However, note that modern firewalls and IDS systems may flag such activity.
The scan type will vary based on the privileges of the user. If the user has root level permissions, then the default scan type is SYN. If not, then the default is a full TCP connection. These can be changed at the command line and there are additional scan options as well.
On the terminal, we'll perform a TCP connect scan by running nmap -sT 10.1.16.0/24.
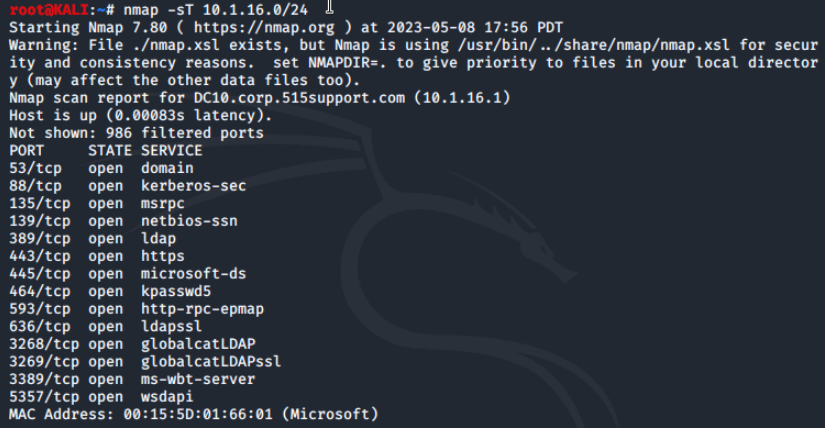
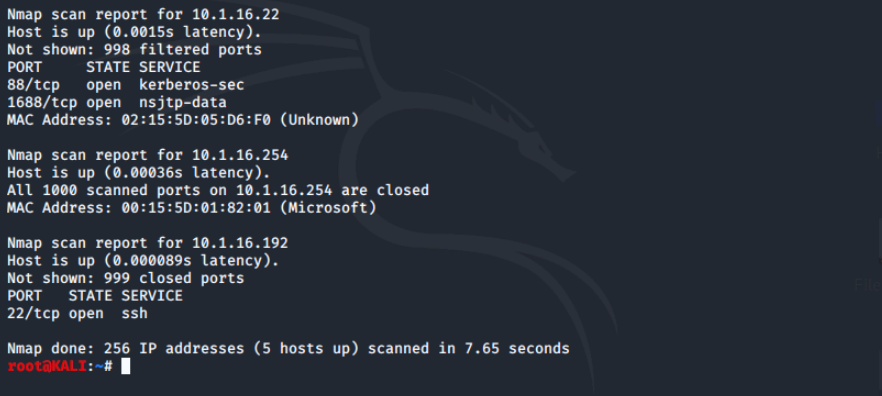
Now we'll perform a SYN stealth scan with nmap -sS 10.1.16.0/24.
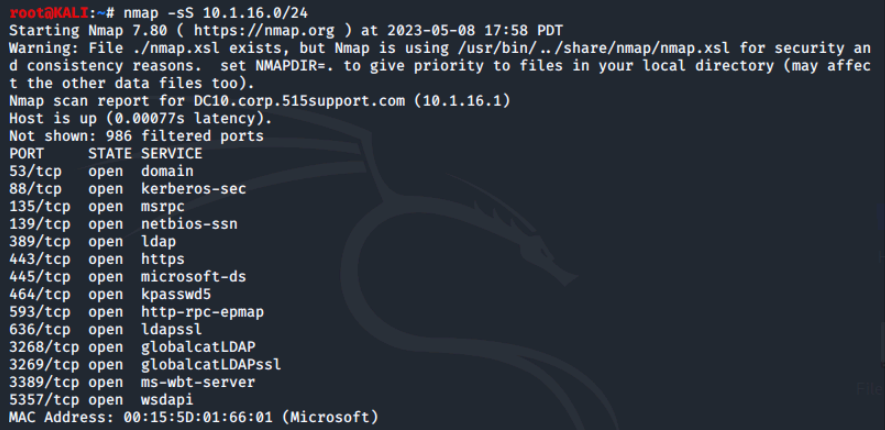
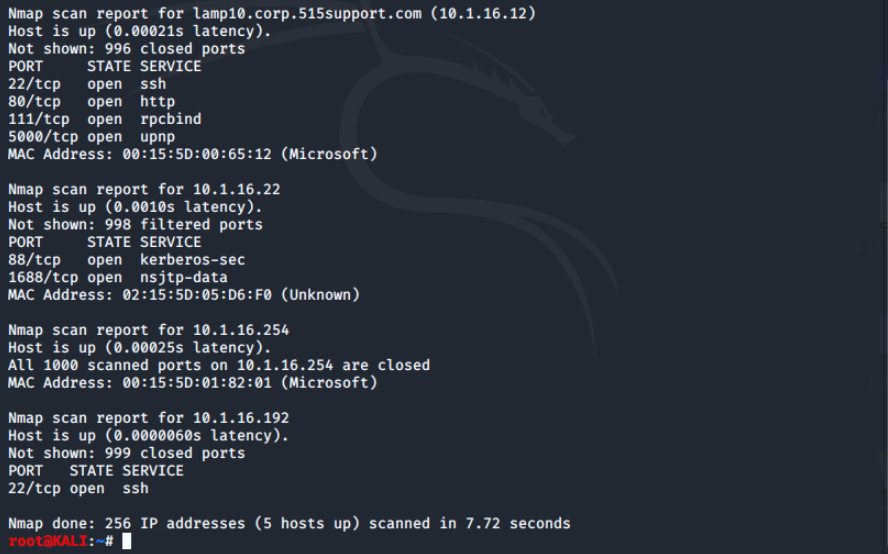
In this case, these two scans returned the same results; the difference would have been on the target side as the SYN scan may have gone unlogged.
Nmap also supports additional scan types including ARP and UDP. Let's try a UDP scan against the Windows server.
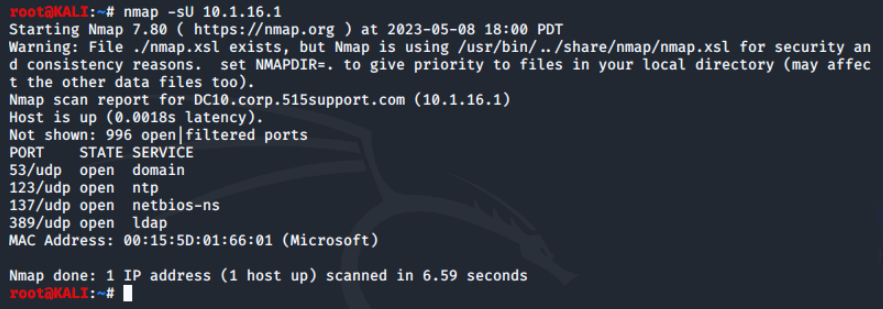
One issue with a UDP scan is that they can take a long time to run.
By default, Nmap uses ping to determine whether a host is "up" before attempting to scan its ports. Using the -Pn option skips this host discovery check. This might be useful in environments where ping activity is closely monitored or for scanning a host that does not respond to ICMP probes, but is operating one or more ports.
Next, we'll perform a port scan without host discovery against the Windows server.
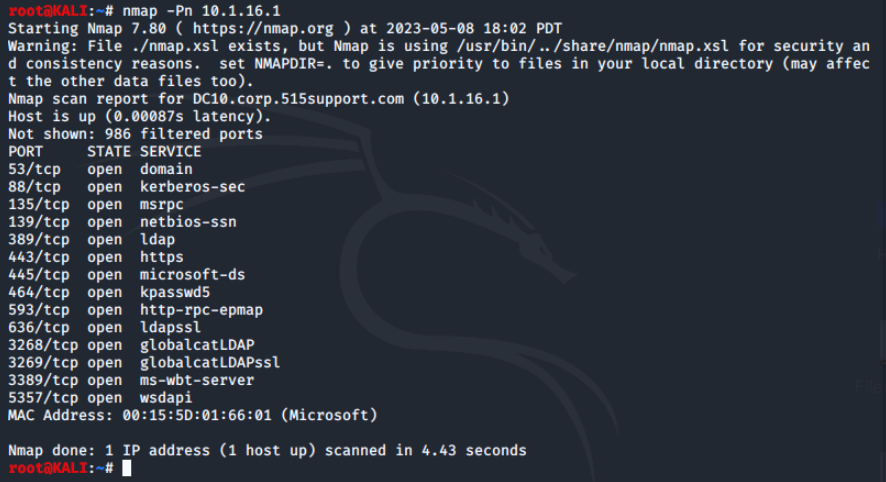
Advanced Nmap Features
Nmap comes with a ton of features and includes options to help avoid detection by firewalls and IDS systems. One commonly used option is -A which performs OS detection, version detection of services, script scanning for vulnerabilities and traceroute all in one option.
The -A can be very slow to run due to all the test it uses, especially when run against a network as opposed to a single target. Let's try it out against the Windows server.
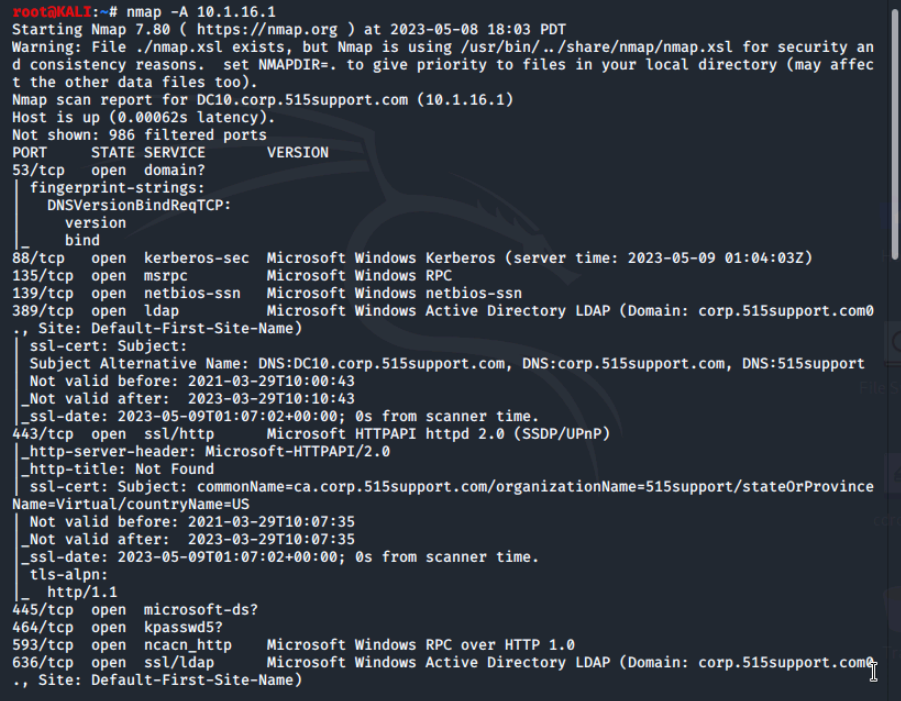
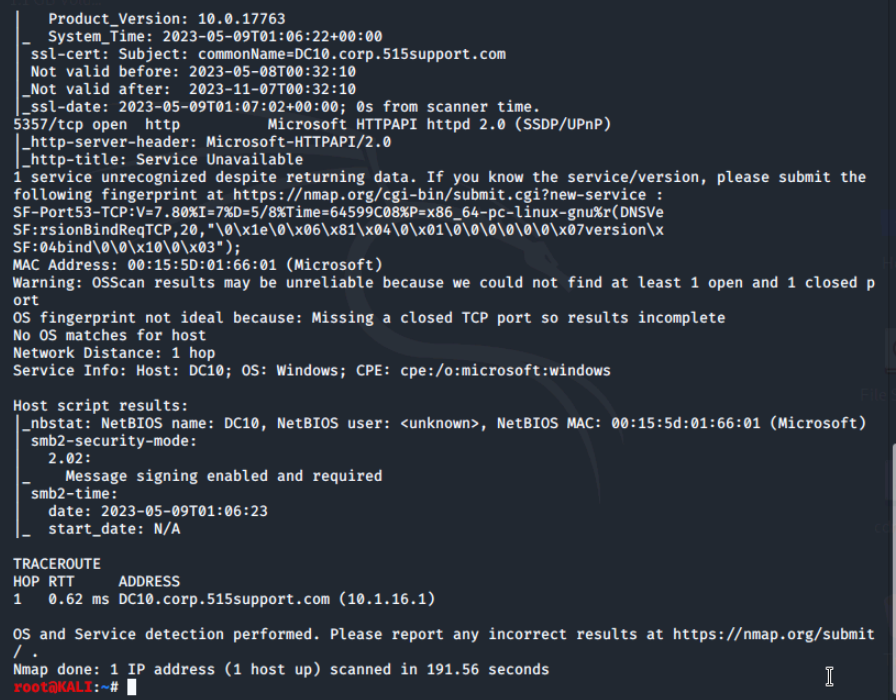
Due to the fact that most modern firewalls and IDS systems are familiar with the pattern of ping sweeps and SYN scans used by a port mapper, these type of scanning activities can be noticed and logged. To help avoid this, nmap supports a timing option using the -TX option where X is a number between 0 and five, with 5 being the fastest scan and 0 being the slowest.
See the chart below for the meaning of the numbers. Obviously, slowing down a scan can help avoid detection.
| Option | Use |
|---|---|
| -T0 | Paranoid |
| -T1 | Sneaky |
| -T2 | Polite |
| -T3 | Normal |
| -T4 | Aggressive |
| -T5 | Insane |
Nmap also supports scripts which can help detect vulnerabilities in our target systems.
- The -sC runs the default scripts, but a user can also use the --script= option to run any particular scripts they wish.
- The script database can also be updated with --script-updated option.
Let's run the command nmap --script=banner 10.1.16.1.
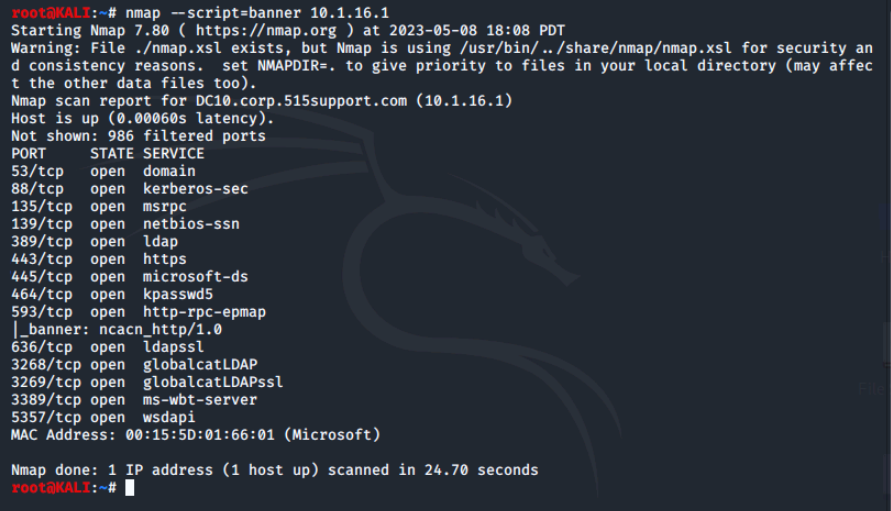
One last set of options involve nmap's ability to output its results into multiple different format using the -o option. See the table below for the formats.
| Option | Format |
|---|---|
| -oN | Normal text |
| -oX | XML text |
| -oG | Grepable text |
Conclusion
Nmap is a powerful open-source network scanner and security auditing tool that provides a variety of scanning options and features to help identify hosts, their operating systems, and services running on each host. It supports various scan types including TCP, SYN, UDP, and ARP scans. We learned how to specify a target for an nmap scan, how to use different scan types, and how to adjust the timing options to help avoid detection. Additionally, we explored the advanced features of Nmap, including the ability to output results in various formats, the use of scripts to detect vulnerabilities, and the -A option to perform OS detection, version detection of services, script scanning for vulnerabilities, and traceroute all in one option. Overall, Nmap is a versatile tool that can be useful in various network security and penetration testing scenarios.
0 Comments Add a Comment?