Navigating Open-Source Intelligence Tools
In this lab, we will be exposed to some popular OSINT (Open Source Intelligence) tools such as, Maltego, ReconNG, the Harvester and Google Dorks used in penetration testing.
Overview of OSINT Tools
Kali includes many OSINT tools which will be reviewed in this section. Another great OSINT tool, the Shodan website will be covered in a later lab.
When clicking on the Kali menu icon on the top left we can see a couple different tools available. We'll be clicking on Information Gathering first.
One of the first icons we will see on the bottom right is for Maltego. Maltego is an amazing information gathering and data analysis tool. It can discover all kinds of information on a target and visualize how it is all connected together. Maltego requires a user to create an account and full Internet access so it can not be fully utilized in this lab. We can go ahead and click on maltego to launch it.
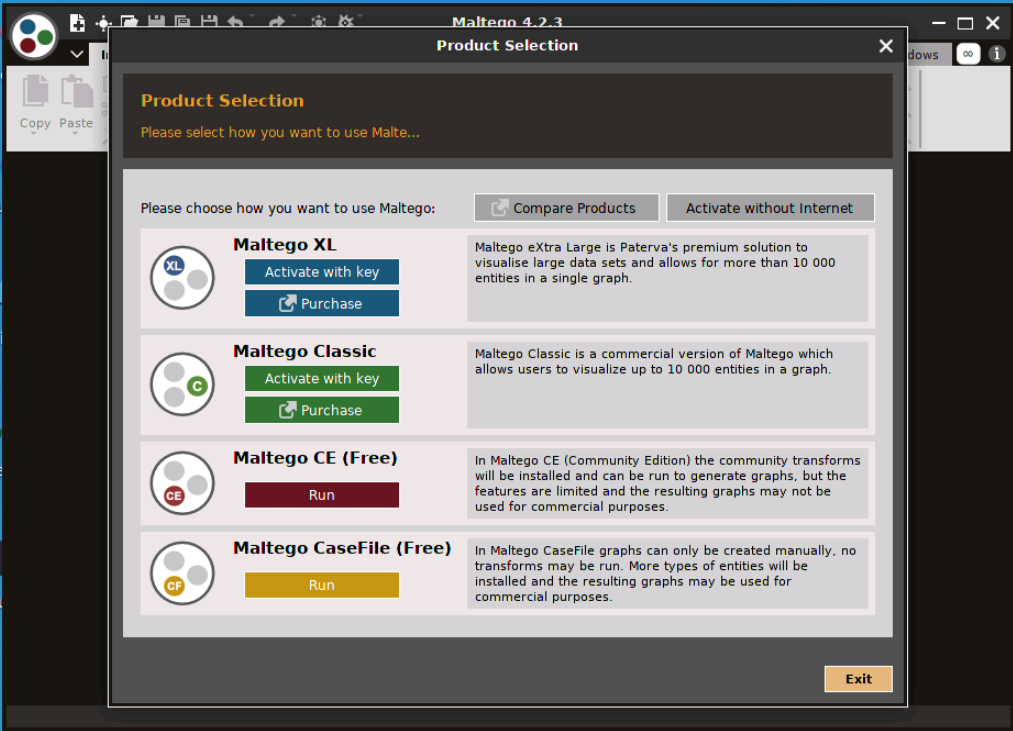
Maltego initially starts with a Product Selection screen. We can see it has two paid versions and a free CE or Community Edition and CaseFile versions.
Back on the Kali menu, we'll navigate to Information Gathering and select recon-ng.
Recon-ng is a reconnaissance framework for gathering information from web based sources. It looks and feels similar to Metasploit. It has a module based approach and initially comes with no modules loaded.
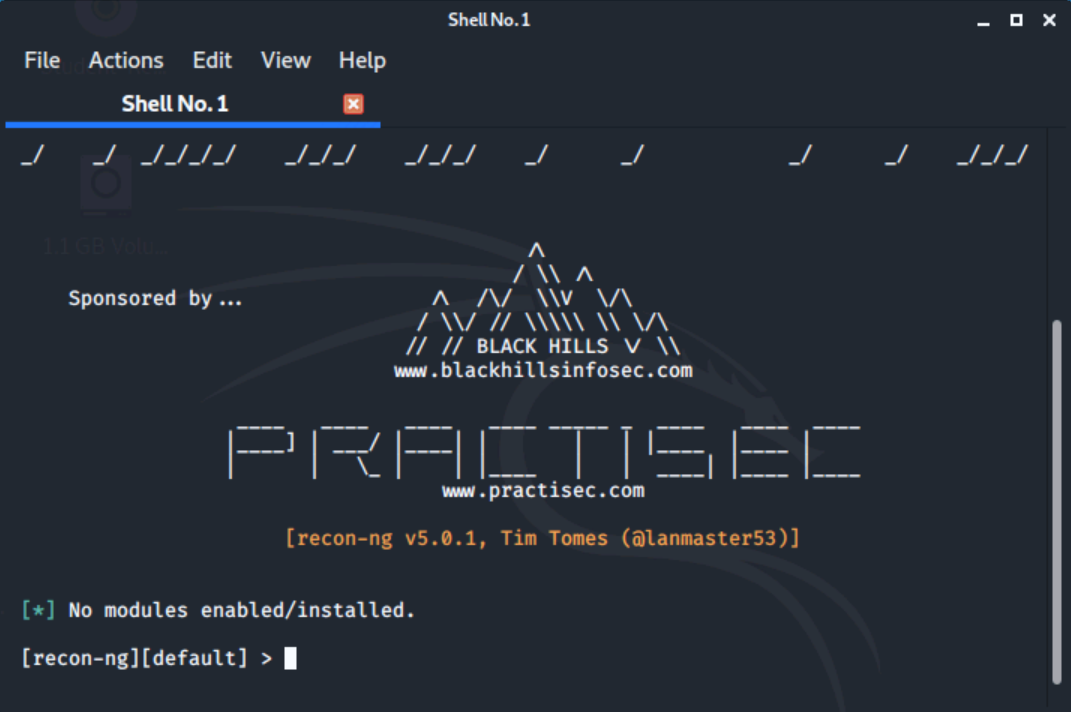
Let's type in help at the prompt.
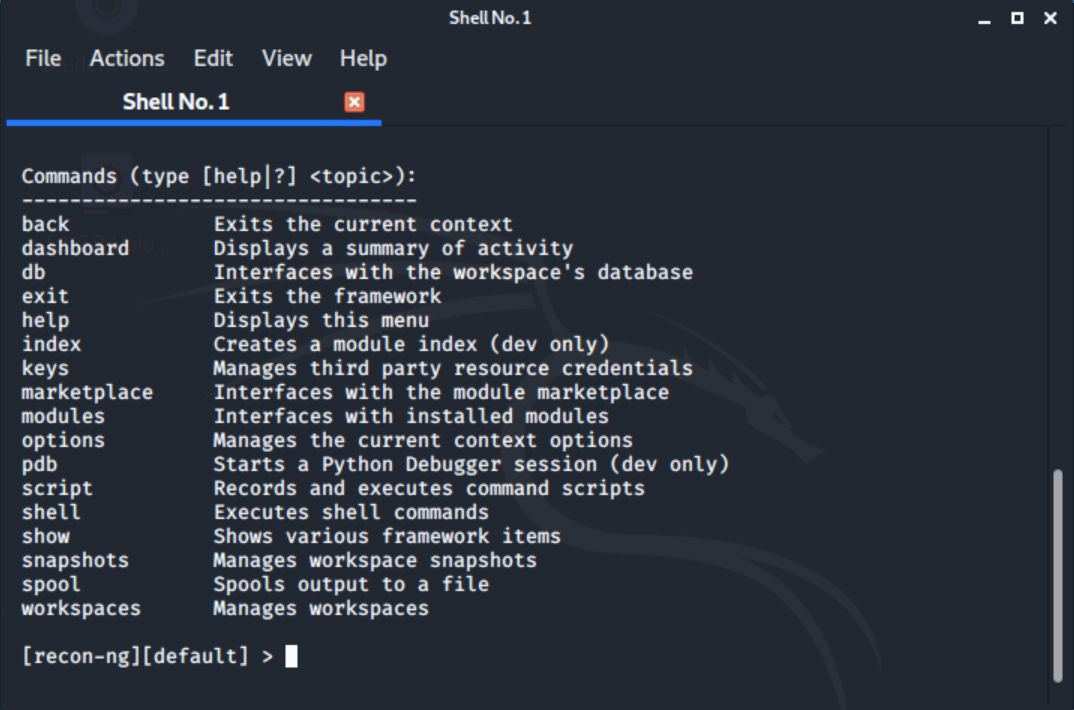
Note: the choice for the Marketplace. We could install all the modules with the command marketplace install all. Typing exit will close the recon-ng and its terminal window.
theHarvester
theHarvester is a tool used to gather information on emails, domains, subdomains, open ports, banners, and more from open sources such as search engines (Shodan.io) and other servers.
Under 01 - Information Gathering, we'll click OSINT Analysis and then theHarvester from the right side menu.
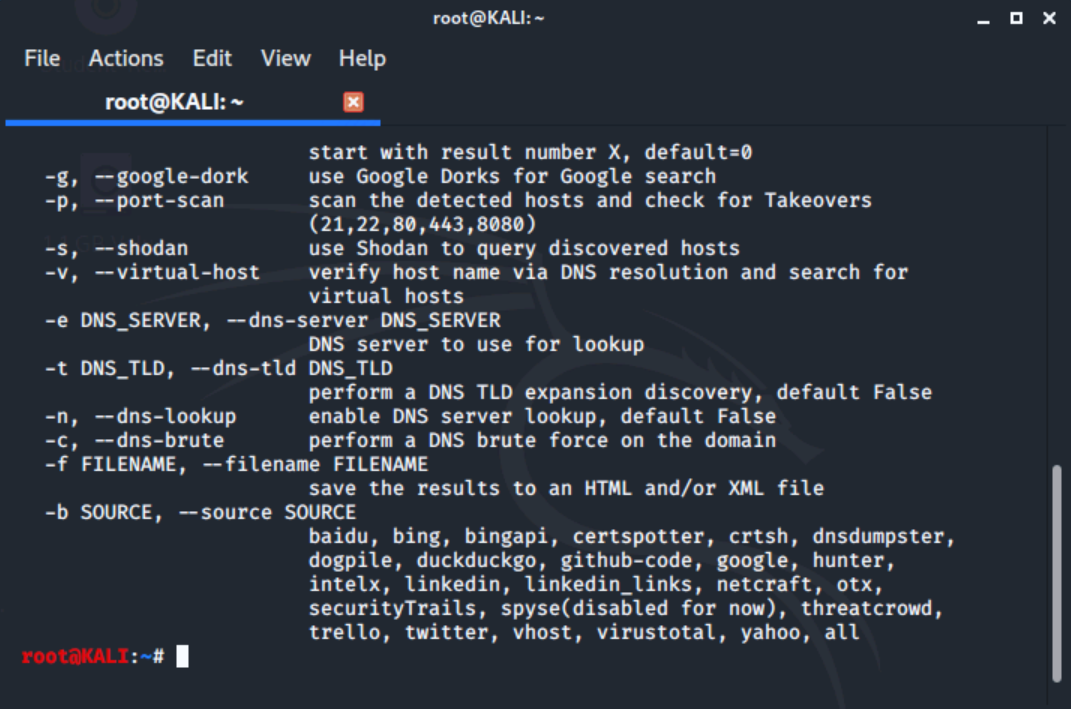
A Terminal window will launch and theHarvester -h will run. Like most tools in Kali, theHarvester is a command line tool. Notice theHarvester has many options and sources of data, including all major search engines. The simpliest use case is to provide a target and a data source.
theHarvester will show progress as it searches, then return results. For larger result sets, use the -l option to limit results or output the results to a file to save and review later using the -f option.
We can save the results of our scan. We'll run the same command as before, but we'll add a few more options at the end to save it to the desktop.
Google Dorks
Google Dorks are particular tricks that use the Advanced Search features of Google for OSINT reconnaissance. Beyond basic searching, Google provides a large number of advanced search keywords which can be used to refine and target our searching for useful information. For example, there are ways to limit Google search results to a particular site or domain.
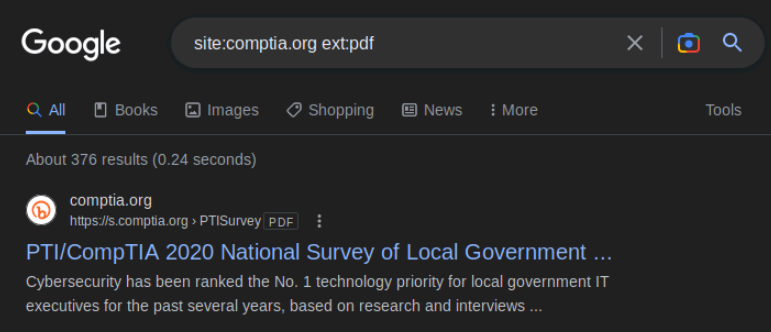
We'll perform the following search to see if Comptia has any pdf's site:comptia.org ext:pdf
Some particular useful Google dorking options include inurl: and intitle: which can look for any keyword in the URL or Title of a page on a website. Let's see if comptia.org has any login pages.
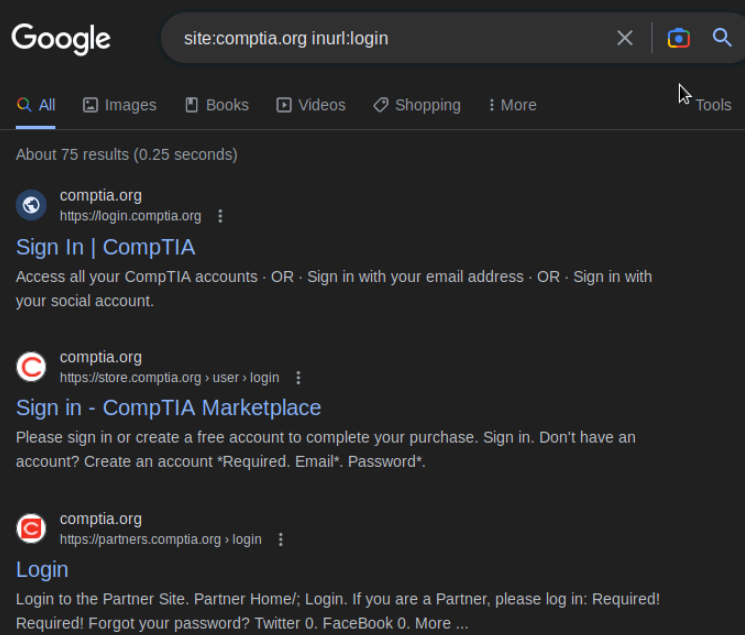
Not surprisely, we find that comptia.org has a number of login pages. We should be able to see the value of these options when preparing for a penetration test.
Conclusion
This lab provided a comprehensive introduction to various Open Source Intelligence (OSINT) tools that can be used for information gathering and analysis. We were exposed to tools like Maltego, Recon-ng, theHarvester, and Google Dorks, and learned about their unique features and functionalities. These tools can be highly useful for penetration testing and reconnaissance activities. While some tools like Maltego require an account and internet access, others like Recon-ng and theHarvester are readily available on Kali Linux.
0 Comments Add a Comment?