
Monitoring with Aircrack-ng
In this lab, we will explore the tools of the aircrack-ng suite and will look at some sample capture files.
Aircrack-ng Suite
The Aircrack-ng suite of tools is built for assessing the network security of wireless networks. It has tools for monitoring, attacking, testing, and cracking wifi communications. All of the tools in the suite are command line tools, which allows for their use in scripts. Many other programs that use the suite take advantage of this fact. The suite primarily runs on Linux, but technically can run on most operating systems, though running on Windows has very little support.
The tools in the aircrack-ng suite are stored in a couple different directories on Kali. Tools stored in */usr/sbin generally require you to be root user in order to run. Let's take a look at what we have available.
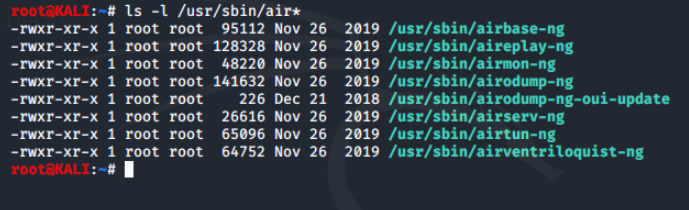
The following three tools are most commonly used to capture and manipulate Wi-Fi traffic:
- airmon-ng - enables and disables monitor mode on a wireless interface.
- airodump-ng - provides the ability to capture 802.11 frames.
- aireplay-ng - injects frames to perform an attack to obtain the authentication credentials for an access point.
Now, let's take a look at what's in usr/bin/air and compare.
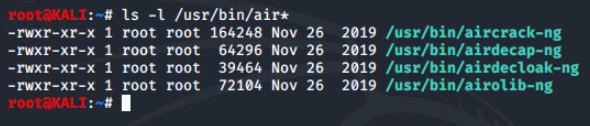
The aircrack-ng tools found in the /usr/bin can generally be run by any user. They are used to decode frames recovered via airmon-ng and airdump-ng:
- aircrack-ng - attempts to recover the passphrase from a packet capture via an offline dictionary attack.
- airdecap-ng - decrypt captured frames once the passphrase has been recovered.
To find out more about the options and usage of an individual tool within the suite, simply add either --help or -h to the end of the tool name for help.
Some commands only take --help and others only -h, but it should be noted that usually just typing the name of the command by itself will also show the help and usage information.
Let's try using --help.
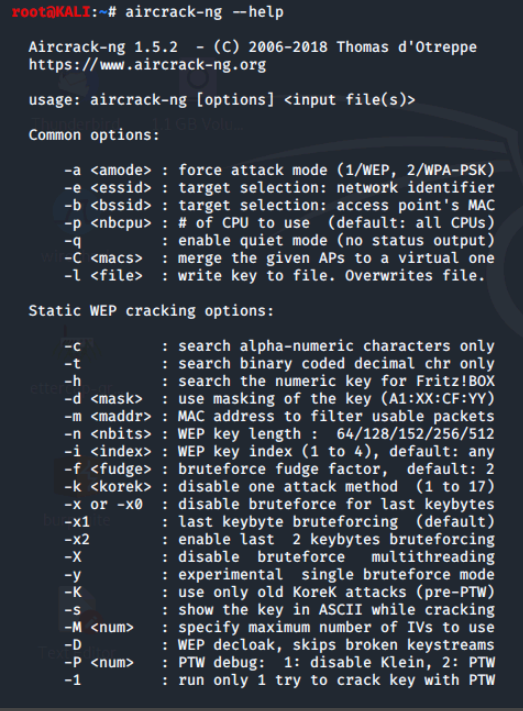
You'd have to scroll up and down to view all of the output of these help commands. Also, the various tools have man or manual pages as well. Let's try using man.
Setting up Aircrack-ng
In the next section, we will look at how to set up aircrack-ng for real use and in the last section we will show some of the functionality of the suite using test files provided by aircrack-ng.
Before using aircrack-ng in the real world:
- Ensure the wireless adapter is supported and compatible.
- Identify the manufacturer of the wireless card and the chipset manufacturer.
Determining the correct chipset of our wireless card can be a challenge. We have a number of options:
- Search the Internet for the card model to find the chipset.
- Search the forums at the official aircrack-ng website at: https://forum.aircrack-ng.org/
- If the card is working on your Windows system, we may be able to determine the chipset by looking at the Windows driver filenames.
- Check the card manufacturer's website.
- If the card is working on a Linux system, we may be able to use either of the lsusb -vv or lspci -vv commands.
- Locate the FCC ID of our device and search https://www.fcc.gov/oet/ea/fccid for our card.
Next, we'd identify the driver needed for the card. There are different drivers available.
To work with the aircrack-ng suite you must be able to put the wireless card in what is called monitor mode.
You can find more information and an example of the monitor mode process at: https://www.aircrack-ng.org/doku.php?id=compatibility_drivers
If you are planning to purchase a card to work with the aircrack-ng suite, see: https://www.aircrack-ng.org/doku.php?id=faq#what_is_the_best_wireless_card_to_buy
To ensure that the card chipset can operate in monitor mode and set up the appropriate driver, use the airmon-ng tool and its options. We'll run airmon-ng and view the results.
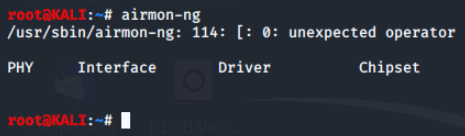
Airmon-ng returns an error and does not display any info as we do not have a virtual wireless card in the environment. However, there are certain processes which can also interfere with airmon-ng, so there is an option to test for this. The command is airmon-ng check.
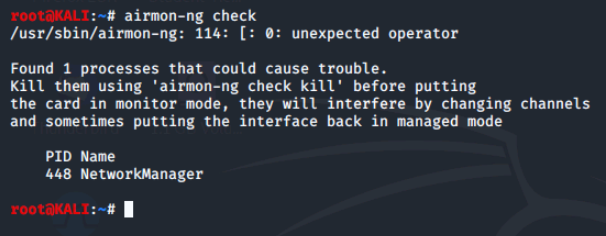
We can see that NetworkManager is the name of the process that airmon-ng indicates could cause problems.
Airmon-ng notes one process which could cause problems and indicates that to kill this process you would type airmon-ng check kill, but we will NOT do this now.
The output of airmon-ng with a wireless card would look something like this:
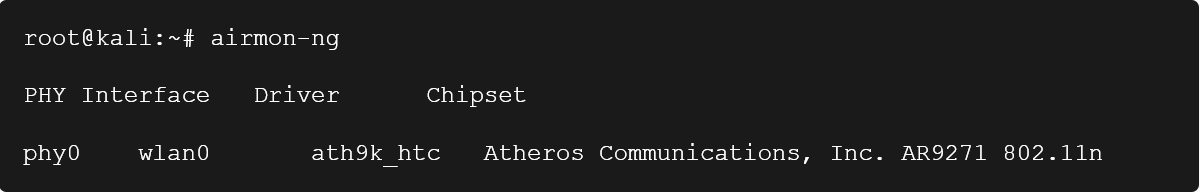
Using this output as an example, we'll use the following command to put the wireless card in monitor mode to work with other parts of the suite.
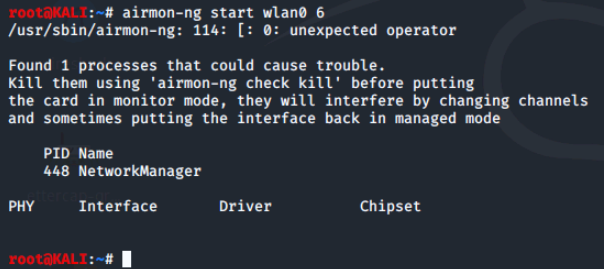
To later disable monitor mode and return the card to managed mode, use the following command:
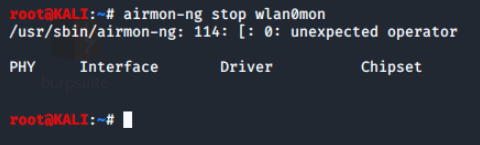
Note the name of the monitoring interface is the default interface name with mon appended to the end, the name used to stop monitoring mode.
Once we have a compatible card and driver, you can place your card in monitor mode and work with other tools in the aircrack-ng suite. In the next section, we will use sample files to show some of the other tools in the suite.
Using Aircrack-ng Tools
Let's take a look at other aircrack-ng suite tools. We will use the wireless traffic sample capture files from aircrack-ng and the suite of tools to analyze and crack the capture files.
On our desktop we have a Student-Resources CD. This CD contains wireless traffic sample capture files that will be accessed at the command line.
These sample files were captured with airodump-ng on a WPA and WPA2 wireless network. A password file is also included. We will use these to attempt to crack the wifi password.
On our terminal, we'll cd into the Lab16 folder and display it's contents.
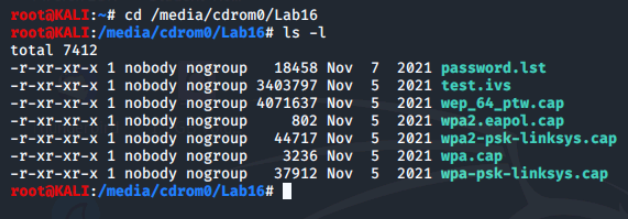
As we can see, there is a password file and a number of capture files. These captures files can be opened by programs such as tcpdump and Wireshark, but we will use air-crack-ng to see if we can crack the wifi password by running the command aircrack-ng -w password.lst wpa.cap
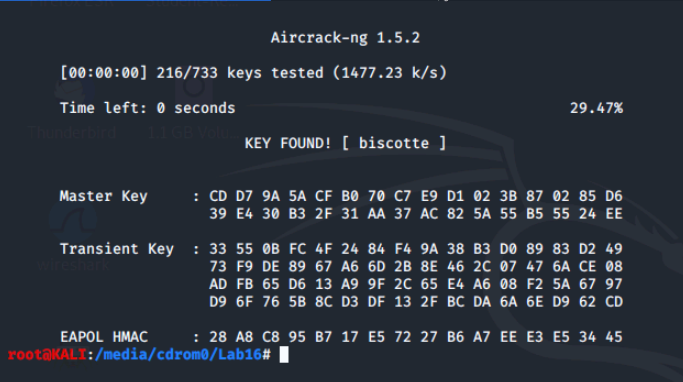
We can see that the key found is biscotte. This was a capture from a WPA Wi-Fi network. Let's try this again on a capture from a WPA2 network by running the command aircrack-ng -w password.lst wpa2.eapol.cap.
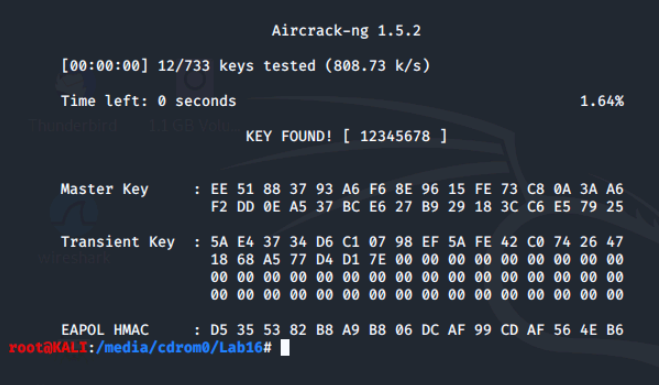
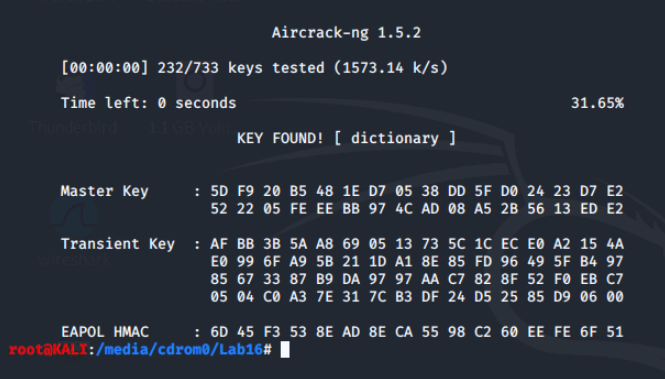
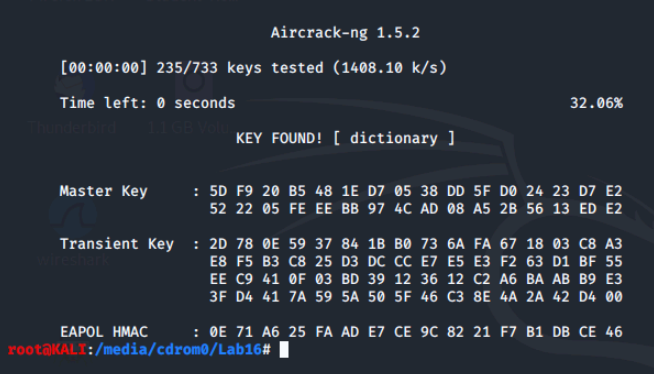
Now, let's rerun aircrack-ng for the following files and see what keys we find.
- wpa-psk-linksys.cap
- wpa2.psk-linksys.cap
Conclusion
This lab focused on the Aircrack-ng suite of tools and how to use them to monitor and manipulate Wi-Fi traffic. The suite is primarily used for assessing the network security of wireless networks and has tools for monitoring, attacking, testing, and cracking Wi-Fi communications.
The lab covered the different directories where the tools are stored and the main tools used for capturing and manipulating Wi-Fi traffic, including airmon-ng, airodump-ng, and aireplay-ng. It also provided steps for setting up Aircrack-ng for real-world use, including ensuring wireless adapter compatibility, identifying the chipset and driver, and putting the wireless card in monitor mode using the airmon-ng tool.
Finally, the lab showed how to use sample files to analyze and crack Wi-Fi traffic using the different tools in the Aircrack-ng suite.
0 Comments Add a Comment?