
Exploring the Domain Tools: Nslookup, Dig, and Whois
In this lab, we will familiarize ourselves with commonly used Internet reconnaissance tools used in penetration testing.
Nslookup
Nslookup is a program to query the Internet Domain Name System (DNS) via submitting requests to domain name servers. Nslookup operates in one of two modes: interactive or non-interactive.
- Interactive mode allows a user to search domain name servers for IP and name information on various hosts or domains. It can also be used in this mode to display a list of hosts in a domain.
- Non-interactive mode just returns the name or IP information requested for an individual host or domain.
Windows has a Nslookup command by default which operates for the most part like the version in Linux or MacOS.
If we simply type in the name of most Linux utilities at the prompt without any options, it will return a screen of basic help and use information. But this does not work for Nslookup since just entering nslookup will start the program in interactive mode. To get help and use information for Nslookup you have to visit the man (man is short for manual) page. We'll do this now.
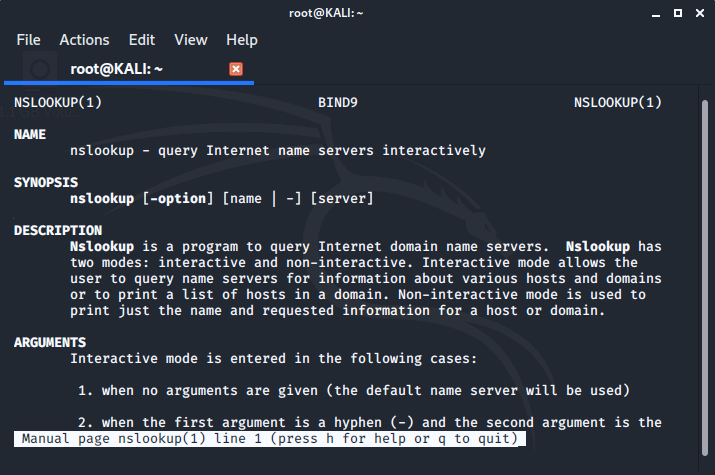
We can navigate the man page using the up and down arrow keys, the page up and page down keys, and after we've reviewed the page we'll simply type the letter q to quit.
Let's try out nslookup and see what kind of results we get by running nslookup on comptia's website.
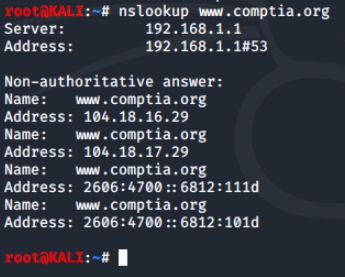
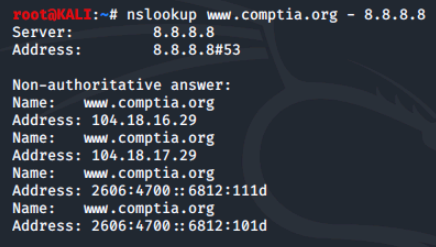
This uses the default domain name server your computer is set up to use. To use a different domain name server, simply add a hyphen (-) and the server name or IP address. We'll use Google's public domain name server at 8.8.8.8.
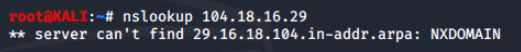
Next, we'll run nslookup on the ip address 104.18.16.29 to display the name associated with the IP address. In this instance, no reverse lookup record is configured, so the query returns NXDOMAN (non-existent domain).
Nslookup in Interactive Mode
To launch Nslookup in interactive mode, you simply need to run the nslookup command.
In interactive mode, we are presented with a greater than sign ( > ) prompt. We can run simple searches and stay in interactive mode. We'll try it out again with www.comptia.org.
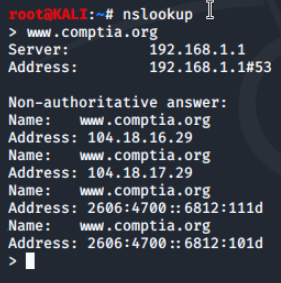
The power of interactive mode comes in via being able to provide options and search for different types of DNS records. For example, we can arrange to return only MX (mail exchange) records with the set type=mx option. We can see that the Fully Qualified Domain Name (FQDN) is comptia-org.mail.protection.outlook.com.
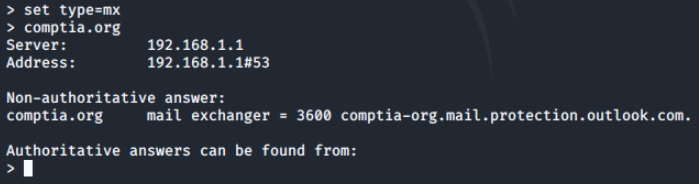
Now we'll try to return the host records by using set type=a, and we'll run a query to return the ipv4 address of the MX record.
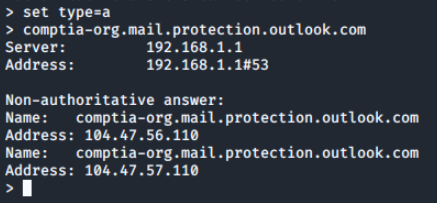
Next, we'll run a reverse lookup for the ip address of the mail host and we can see a record is configured for it. PTR records are used by other hosts to verify the sender and are very important to configure correctly for mail services.
Dig
Dig, whichs stands for Domain Information Groper, is another program used for querying the Domain Name System (DNS) via domain name servers. Dig allows a user to search for information on different domain record types, including hosts address, mail exchange records, and DNS servers associated with a domain. It is commonly used for DNS troubleshooting and for domain reconnaissance.
Dig is not installed on Windows by default, but can be added by installing the latest version of BIND (install the Tools Only) from https://www.isc.org/download/.
As with Nslookup, we can not get help and use information from just typing dig at the prompt, as this will return a list of root DNS servers in use. To get use and help information we most visit the manual page.
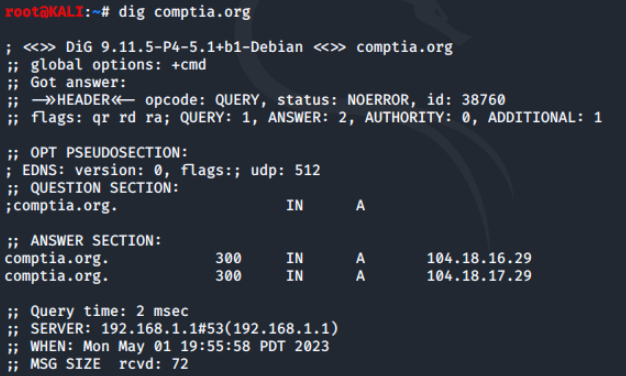
The most basic way to use Dig is to run it with the name of a host or domain we want to look up.
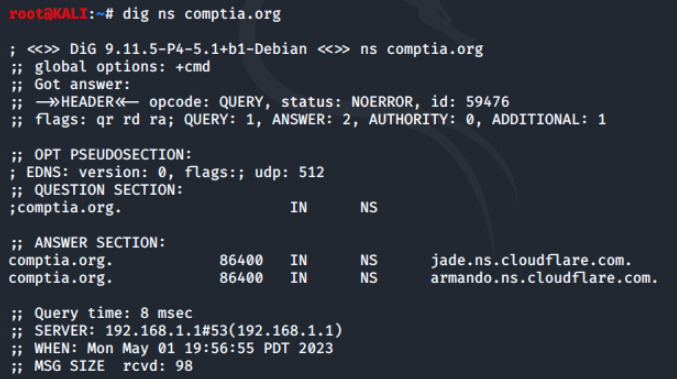
The power of Dig comes in when using its options. For example, we can find another DNS record types by using the -t option. In this example we will search for NS (name server) records. When our command is executed, we can see that cloudflare.com is hosting CompTIA's name servers.
Whois
Whois is another powerful tool for gathering information about a domain and related Internet information.
- The Whois system provides information on domain names, IP address blocks, and autonomous systems.
- It is a query and response protocol and can be accessed via command line tools and many websites including most domain registrars.
While many domain registrars sell or provide private or anonymous registration services, there is still much useful information which can be found out using Whois.
Whois is not by default installed on Windows, but can be added by downloading the latest version from Microsoft at https://docs.microsoft.com/en-us/sysinternals/downloads/whois or by downloading the entire Microsoft SystemInternals Suite.
Like with most Linux utilities (and unlike Nslookup and Dig) you can get help and use information from just typing whois at the prompt. As shown below.
we'll run the whois command on comptia.org and see what kind of results we get.
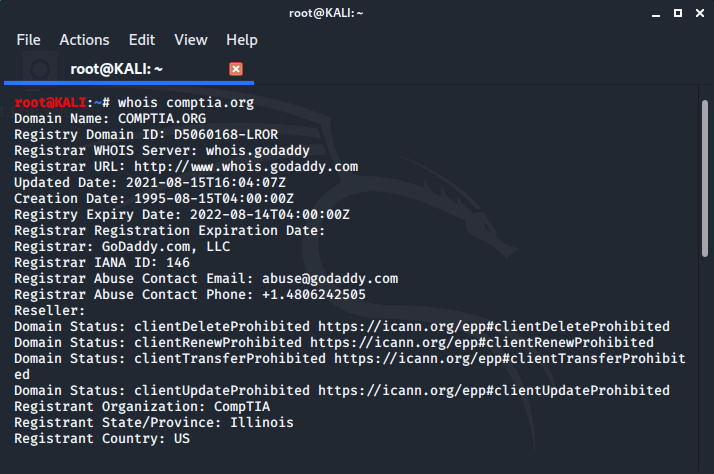
There is a lot of information returned on the domain, so we would have to scroll back up to see the top of the output.
- Whois records contain information about the creation and expiration dates of domains and sometimes the contact information of the person or entity that registered the domain.
- The contact information is less useful these days as many domain registrars sell private registration services which hides this information.
Whois records also contain information about:
- location where the domain was registered
- one of the most important data points which can't be hidden, the DNS servers used by the domain.
Whois can be a useful tool to start with when doing recon on a potential penetration target. Getting the DNS servers allows one to use the other tools from this lab, Nslookup and Dig, to find out additional information on the target such as their web and email servers, etc.
Conclusion
Through this activity, we were able to familiarize myself with the Nslookup tool and its various modes, interactive and non-interactive. Additionally, we learned how to use Nslookup to query the Internet Domain Name System (DNS) and perform basic and reverse DNS lookups.
0 Comments Add a Comment?