
Demonstrating Enumeration Techniques
In this lab, we will explore various enumeration techniques to gather system information in order to identify potential attack vectors.
Enumerating Hosts
During the information gathering phase we will move from passive reconnaissance to active reconnaissance. Here we use the information we gathered to determine our attack vector by starting at the top of the list working our way down. That means retrieving a list of open ports, vulnerable services running on those ports, web directories, or the type of information that can be exposed by the service such as a list of users.
When enumerating a host, we will determine the best possible entry point. Which means we will be going over your scans in detail line by line to find the lowest hanging fruit.
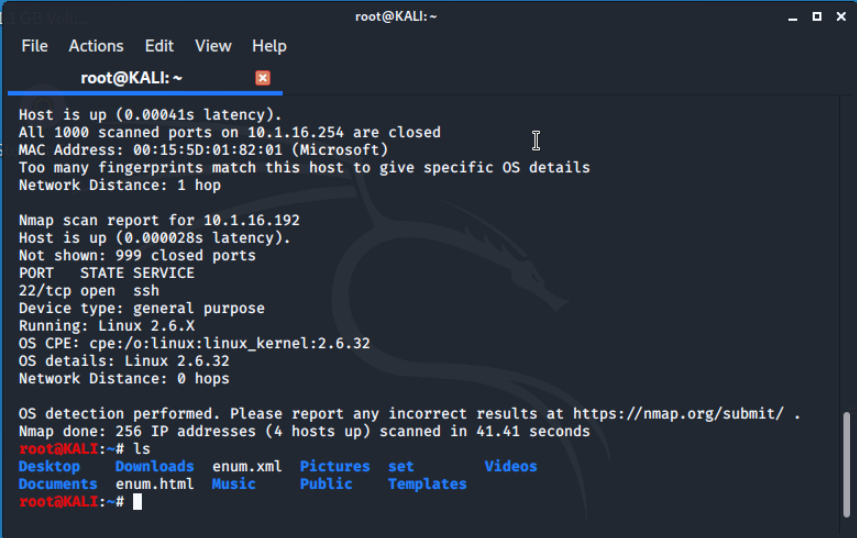
We'll start by running an nmap scan to identify hosts on our network. We are using the -O option to detect the Operating Systems of the hosts on our network.
We'll use the command: nmap -O 10.1.16.0/24 -oX enum.xml && xsltproc enum.xml -o enum.html
Then we'll run ls to write out the contents of the current working directory to confirm our output file is there. This shows us that the xsltproc converted enum.xml to enum.html
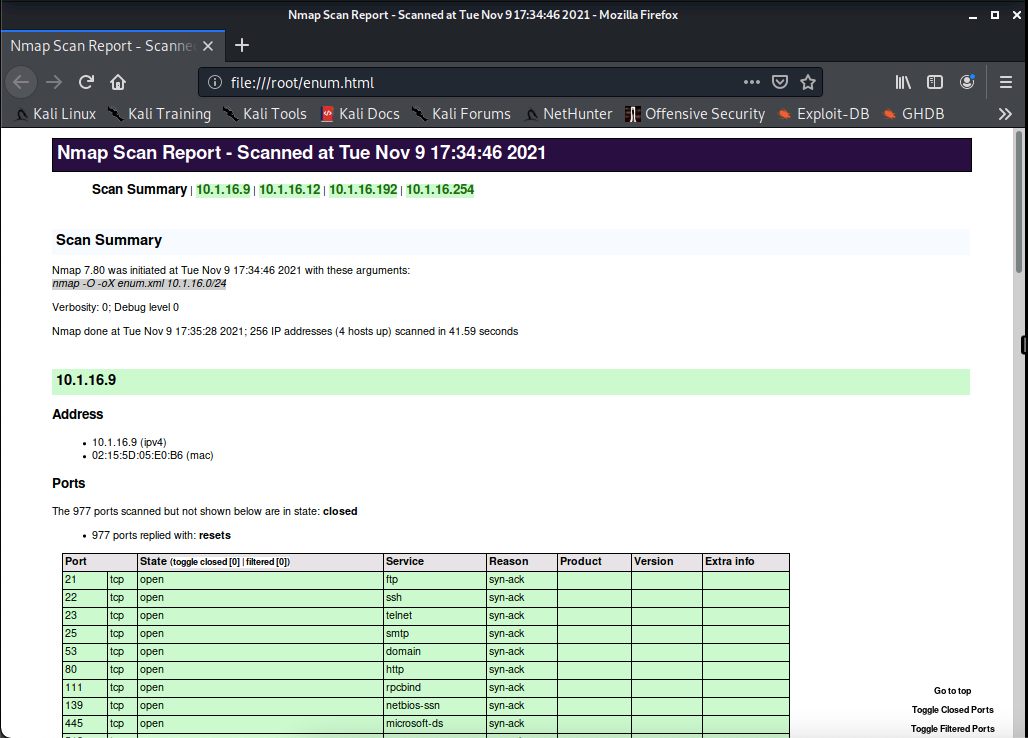
We'll type in firefox enum.html to open it in our firefox browser.
Enumerating Ports
We'll be determining what versions of the services are running on the host we previously scanned to identify potential exploits. Our result from our last scan shows us that the host 10.1.16.9 has more open ports than any other host on the network.
We'll run an nmap scan to determine the versions of the services on all 65,535 ports open on this machine. Then, we'll output the scan into an .xml file using the -oX option to create a detailed list. We'll do this by running the command nmap -sV -p- 10.1.16.9 -oX enum2.xml
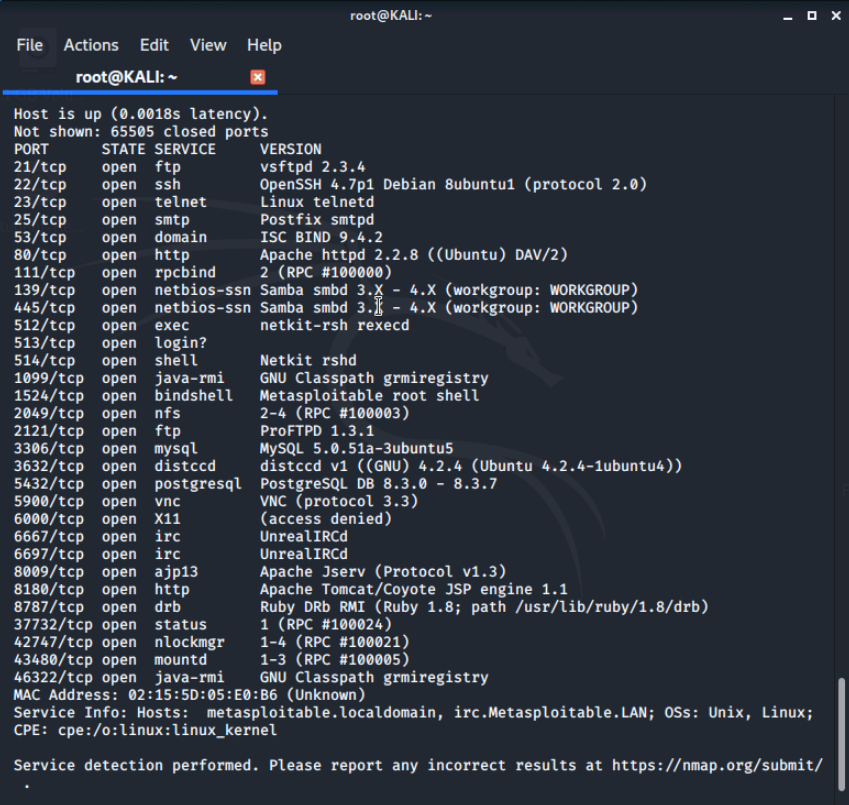
We can see some details like how MySQL is running version 5.051a-3ubuntu5 on port 3306.
Let's convert our file to an html format and list it to confirm it's been converted.
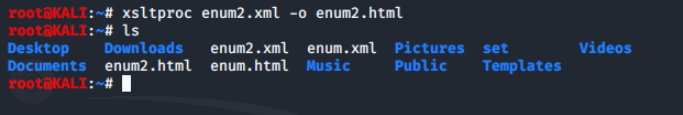
Below is what our report looks like when opened with firefox.
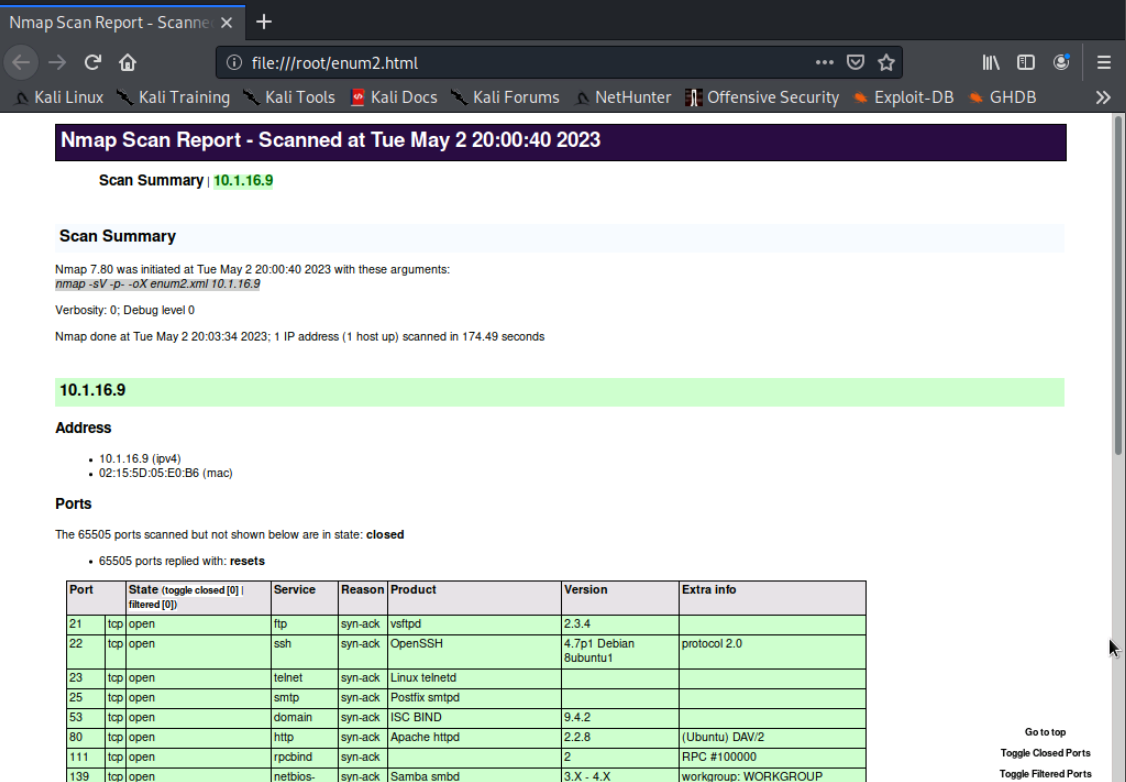
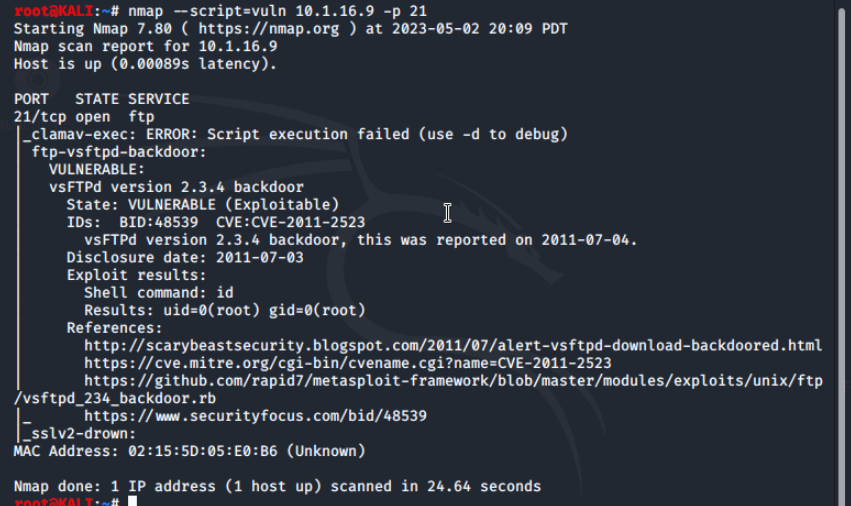
Starting with the first port lets determine what vulnerabilities exist for port 21.
There are 65,535 ports available, when enumerating hosts, you want to exhaust every possibility. You can add the -p- option to scan all 65,535 ports on a host. This type of scan can take some time when identifying vulnerabilities for all 65,535 ports.
Enumerating Web Directories
There are many tools we can use to enumerate web directories; in this section we will be using Dirb and Nikto to scan our web server.
Dirb

Dirb is a web content scanner that launches a dictionary-based attack to identify web directories using a dictionary file.
Note: We can view the web directory files that can be used by dirb by navigating to /usr/share/wordlists/dirb/.
By typing in dirb in the command line, we can see a list of options and command usage exampes.
Using dirb, we'll run a scan on the metasploitable web server. When we run the scan, we can scroll up and down in the terminal to view the entire output of our scan. When an accessible directory is found it will be noted with ==>
Let's type in dirb http://10.1.16.9/
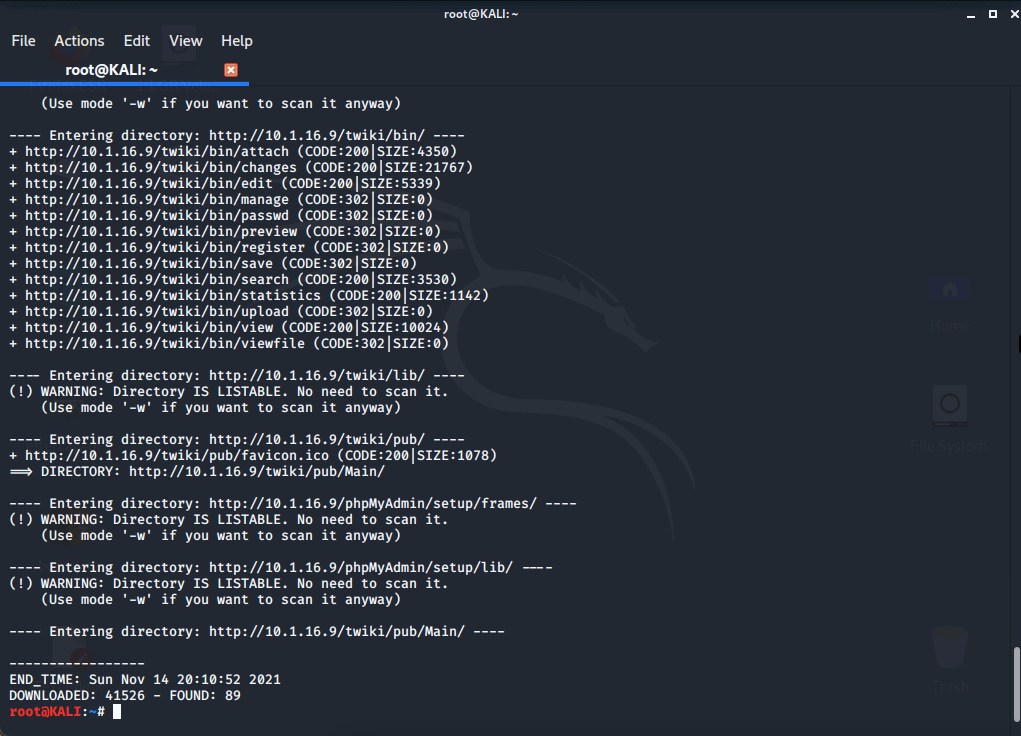
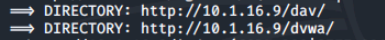
Our output dirb identified 41,526 files and 89 directories. We can view a directory by typing the webservers directory in the address bar of our browser.
We'll be opening up the following link ending in dvwa in firefox, and we come across a login in screen.

Nikto

Nikto is a web server vulnerability scanning tool. Nikto will return any cookies received from the web server while attempting to detect files, software, and directories running on the web server.
When typing nikto into our terminal and running the command,we see a list of options and command usage examples.
we'll use the -h option to scan the metasploitable2 host. nikto -h 10.1.16.9
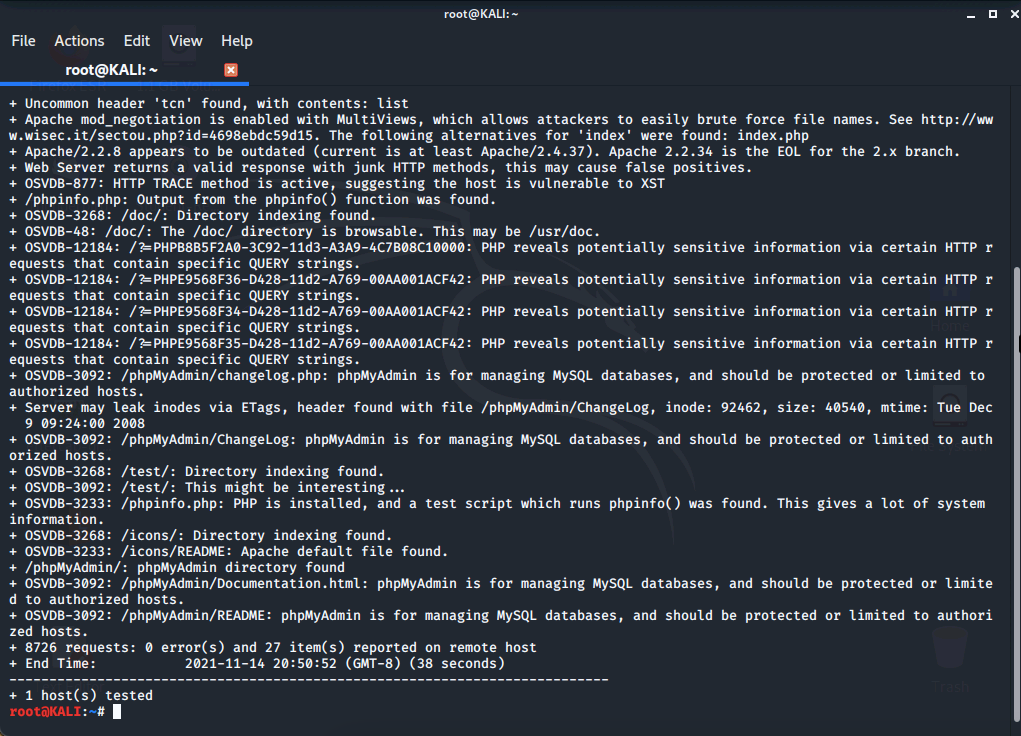
When a directory is identified our output will show Directory indexing found. or directory found to the right of the directory discovered.
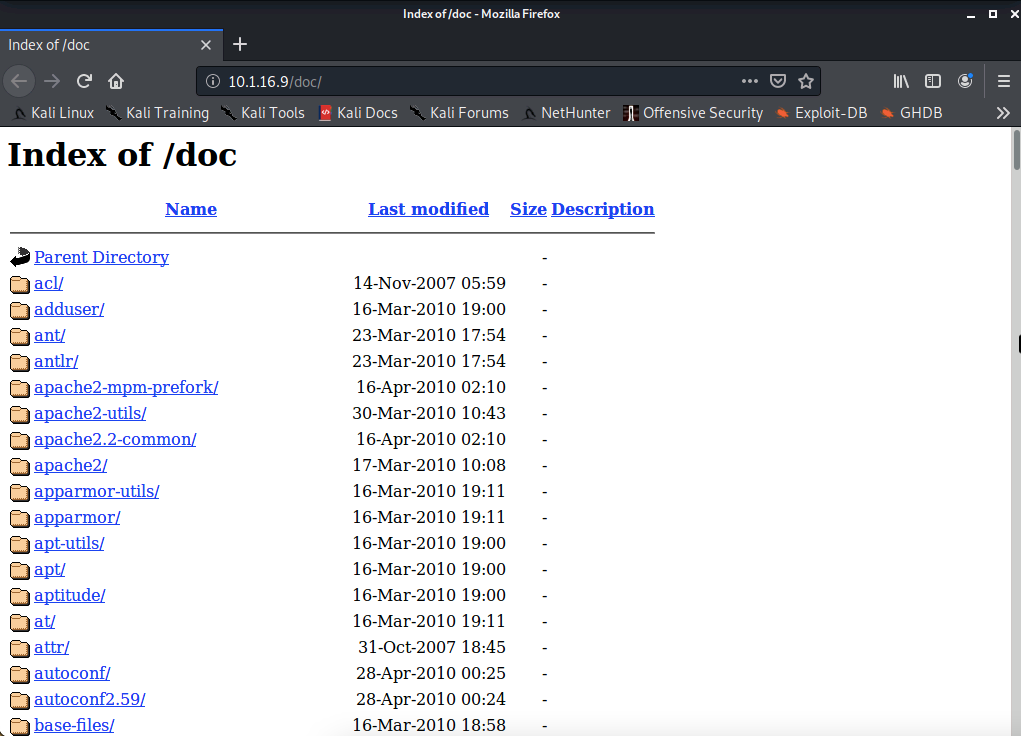
Nikto discovered numerous directories and even vulnerabilities on this web server. You can navigate to each directory using your web browser.
- /doc/
- /test/
- /icons/
- /phpMyAdmin/
Conclusion
This lab demonstrated various enumeration techniques used for information gathering to identify potential attack vectors. We started with passive reconnaissance and then moved to active reconnaissance to retrieve a list of open ports, vulnerable services running on those ports, web directories, and the type of information that can be exposed by the service.
We used nmap scans to identify hosts on our network, determine the versions of services on open ports, and output the scan results into detailed lists. We also used Dirb and Nikto tools to scan web servers for web directories and vulnerabilities.
0 Comments Add a Comment?