
Navigating Steganography Tools
In this lab, we'll be using Steganography to hide and conceal messages within another file such as a text file or photo.
Steghide
Steghide is a steganography application that can help with computer forensic investigations. We can hide bits of data in the least significant bits on top of another file, this makes the data file only accessible using a tool to extract the data in combination with the password we create.
Steghide is installed in this environment but Kali Linux does not come with steghide installed by default. You can install steghide by using the following command:
sudo apt-get install steghide
Steghide supports the following file formats to hide data:
- .jpeg - (Lossy compressed image data)
- .bmp - (Bitmap digital images)
- .wav - (Audio file)
- .au - (Audacity audio file)
We'll start by running the steghide command in the terminal.
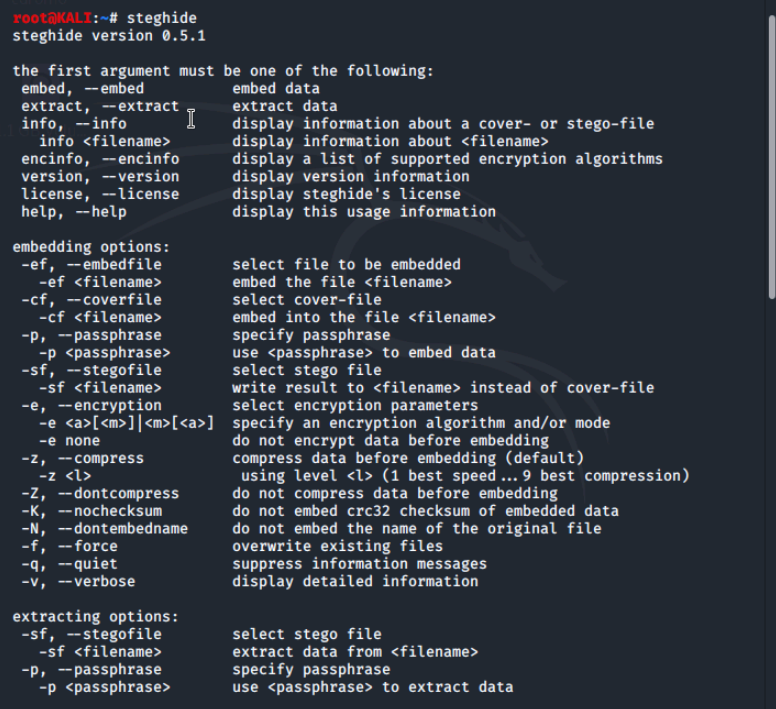
Embedding File Using Steghide
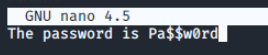
Let's create a text file containing our secret message that we will conceal within a photo. We'll create a text file called secret.txt and use nano to edit the file and add the following message.
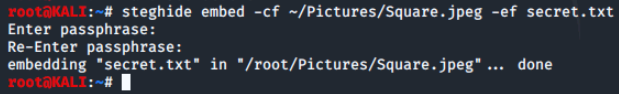
Now we will embed secret.txt into our image using the following command
- steghide embed -cf ~/Pictures/Square.jpeg -ef secret.txt
- Enter passphrase: Pass
Now, we'll navigate to the directory where our picture is located which is Pictures/
This is just a normal image from what we can see. We can view the image using Ristretto Image Viewer using the command: ristretto square.jpeg
We'll exit ristretto and return to our terminal. Using the --info option we can see that there is an embedded file in this image.
- Run steghide --info Square.jpeg
- Select y when prompted to enter the password for Square.jpeg
- Type in the password Pass
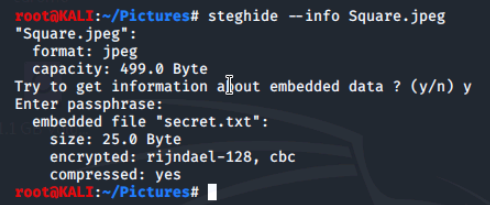
This tells us that this image has our embedded file secret.txt, encrypted using rijndael-128 (AES) block cipher (cbc), and the embedded file is compressed.
We can now extract our embed secret from our image with the following command.
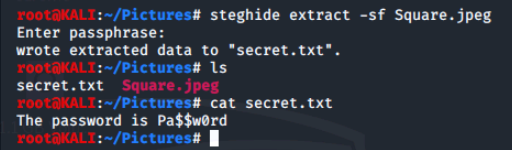
- steghide extract -sf Square.jpeg
- Enter passphrase: Pass
- Type ls to see our secret has been extracted from our file.
- Use cat to view the contents
Conclusion
In this lab, we learned about steganography and how it can be used to hide messages within files. We used a tool called Steghide to embed a secret message in an image file.
By running commands in the terminal, we successfully concealed a text file called "secret.txt" inside an image named "Square.jpeg." We made sure to set a password ("Pass") to protect the hidden data.
Even though the image looked normal, we used the "steghide --info" command to confirm the presence of the embedded file. It was encrypted and compressed for security.
We then extracted the secret message from the image using the "steghide extract" command and the password. We verified the extraction by checking the contents of the extracted file using the "cat" command.
This lab gave us hands-on experience with steganography and showed us how tools like Steghide can be useful in computer forensic investigations. It's important to be aware of steganography techniques to detect and handle hidden information effectively.
0 Comments Add a Comment?