
Discovering IoT devices with Shodan
In this lab, we'll be using the Shodan search engine to gather critical information on IoT devices connected to the internet in real time.
Shodan.io
Shodan.io is a search engine used to search for internet-connected devices including IoT devices. These devices are not always properly secured and can be riddled with vulnerabilities and default password credentials, a veritable playground for hackers.
- With a simple Shodan.io search query, you can learn more about vulnerable devices and how these could be exploited.
- In this lab, we'll use Shodan.io to identify and secure these vulnerabilities and protect our devices.
We'll start by using firefox to navigate to shodan.io.
We need to create an account to use shodan, so we'll create a quick temporary account, and then return to the homepage. Once we're at the home page, we'll type in ibm.com into the search bar at the top of the page.
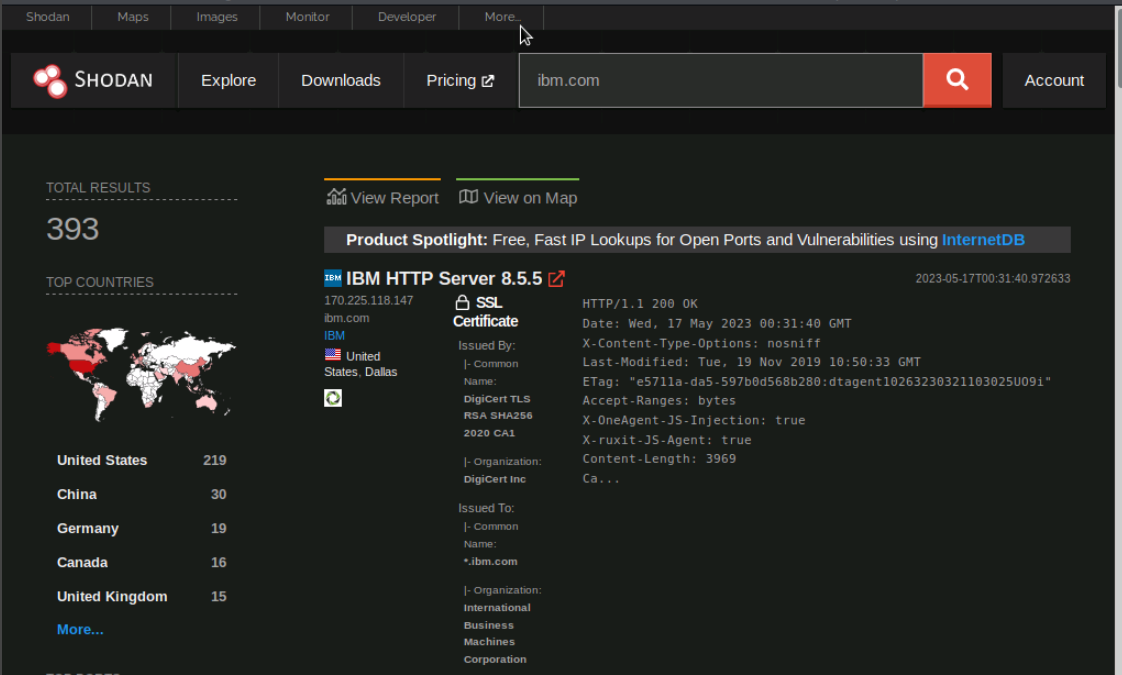
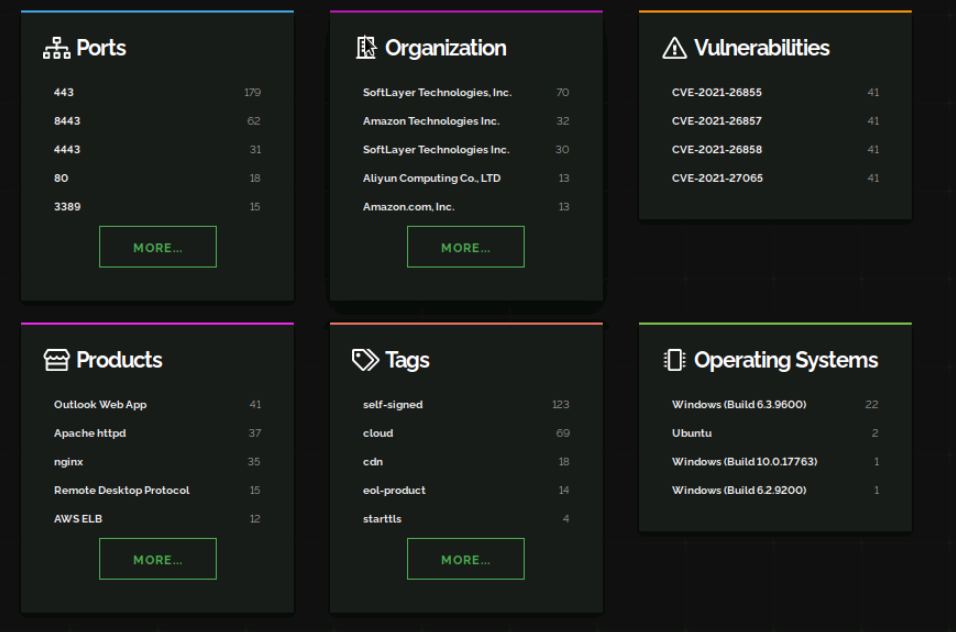
We'll click on View report and we can see that our report generated important information regarding devices discovered on ibm.com
- Map of the geographical locations of devices discovered.
- Port number the service is communicating through.
- Organization hosting the service.
- Identified vulnerabilities.
- Products which are the services running on the network.
- Tags that are used to keep track of various types of devices and services.
- Operating Systems of discovered devices.
Utilizing Search Filters on Shodan.io
When we perform a search on shodan.io our results will depend on how we format our search. This section will help us optimize our search query to discover more information.
Shodan uses these search filters that allows the search engine to return more accurate results. For more help on search query syntax and how to utilize the Shodan search functions refer to Shodan Search Query Fundamentals
Shodan.io identifies devices by collecting the information that is stored in the banner of the service. This is a simple welcome message containing:
- network host
- application type
- service version
- operating systems
This information is incredibly useful when identifying a vulnerable application.
In the search bar if we chage the search tag from ibm.com to org:ibm, we go from about 300 total results to about 17k results.
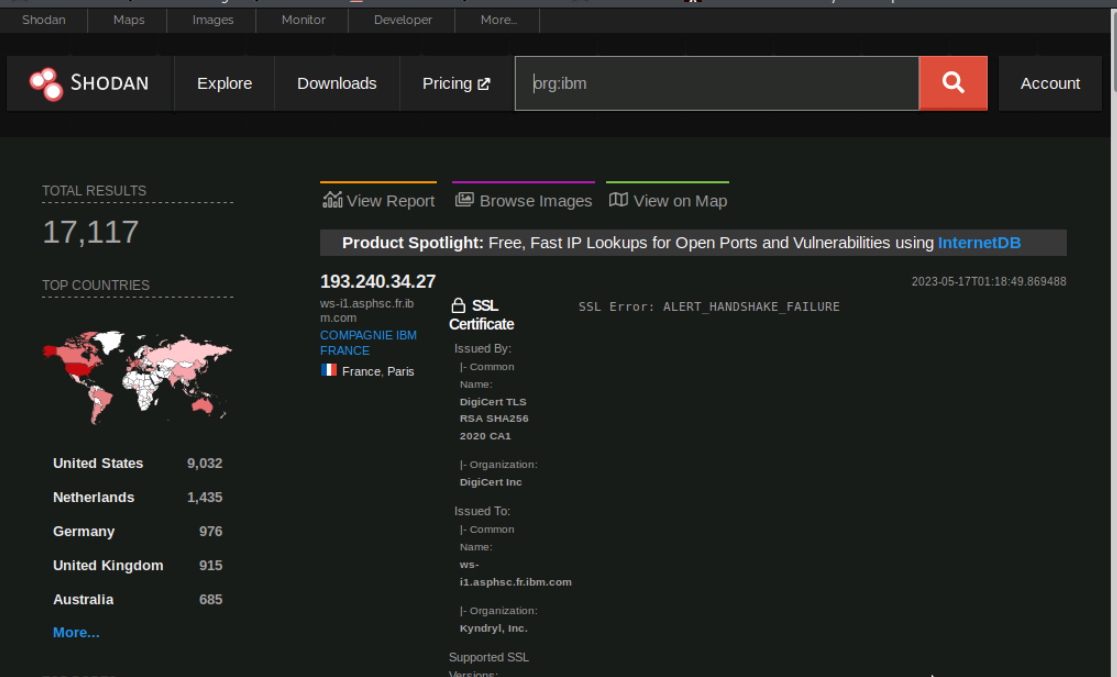
The org tag searches for IP addresses owned by the organization from our search query.
We can search for types of devices connected or even brands of devices connected to the internet. We'll surround our search query with quotation marks to search for brands of devices.
For example "linksys" and "cisco". We'll search for both network device brands in the search bar.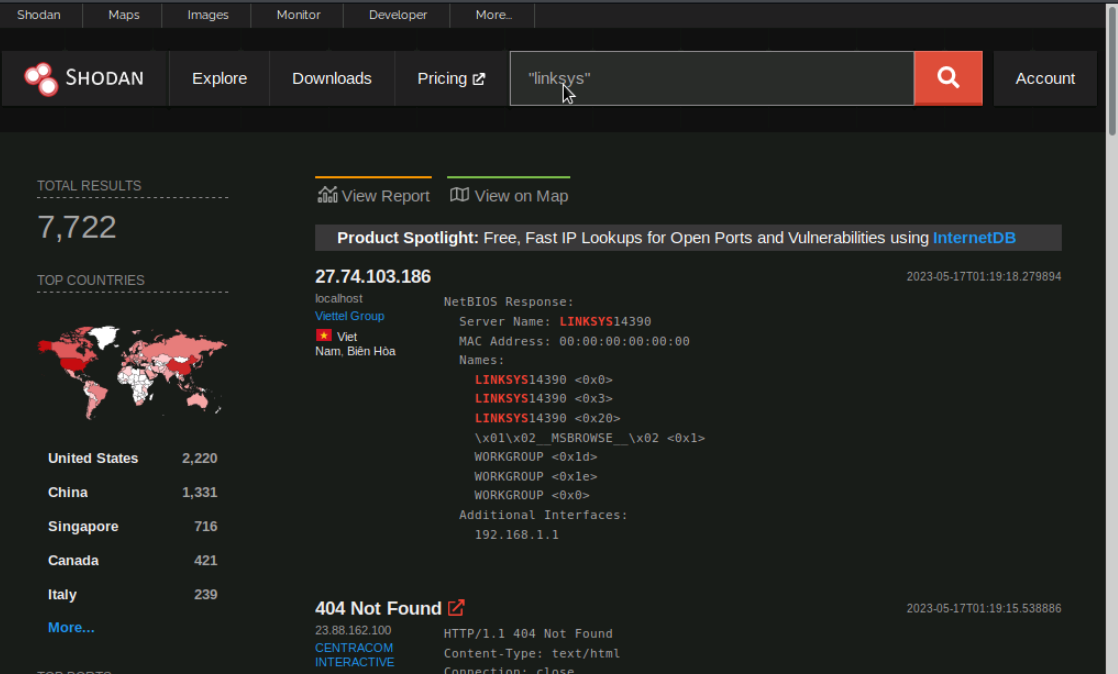
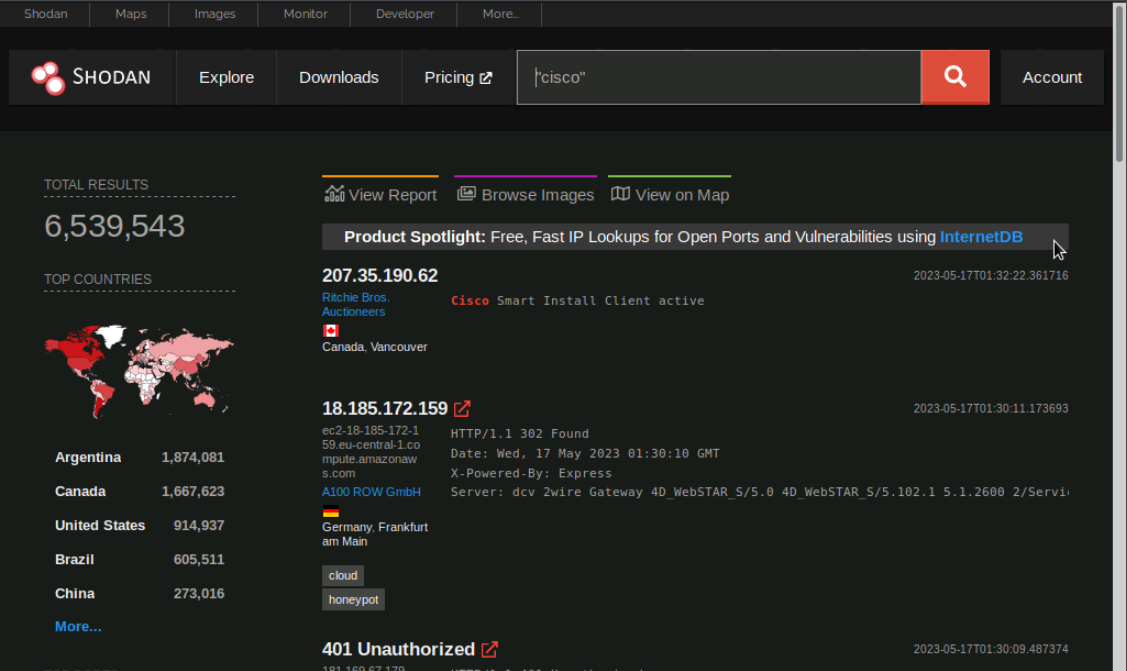
Our search query produces results for linksys and cisco show over 7,000+ linksys devices and over 6,000,000+ cisco devices connected to the internet and responding to Shodan's request.
Conclusion
Using Shodan.io as a search engine to find IoT devices connected to the internet has been eye-opening. We discovered that many of these devices are vulnerable and pose potential security risks. Shodan.io provides valuable information like device locations, vulnerabilities, and running services, enabling us to identify and address these risks.
We also learned how to refine our searches using filters, such as searching by organization or specific device brands. This helped us narrow down results and obtain more relevant information.
The sheer number of vulnerable devices we found, such as thousands of Linksys and millions of Cisco devices, highlights the urgent need for better security practices in the IoT industry. Manufacturers and users must prioritize securing these devices to prevent unauthorized access and potential exploitation.
In summary, Shodan.io is a powerful tool for discovering IoT vulnerabilities. By leveraging its capabilities and taking proactive security measures, we can contribute to a safer and more secure IoT ecosystem.
0 Comments Add a Comment?