
Analyzing Exploit Code
In this lab, we'll be exposed to some code written to exploit known vulnerabilities such as the VSFTP backdoor.
Public Exploit Sites - National Vulnerability Database
There are numerous publically available databases and sites of vulnerabilities and exploits. Most contain information about the vulnerability and often sample proof of concept code to exploit the vulnerability. It is useful to learn about these samples to improve your code reading abilities and to see how exploits are actually being used.
Two of the best sources of such information are the National Vulnerability Database hosted by the National Institute for Standards and Technology (NIST) and the Exploit Database by Offensive Security. We will use the browser in the environment to visit these sites and look at some examples.
We'll visit the NIST website at https://nvd.nist.gov/vuln and click on the search option on the left side menu.
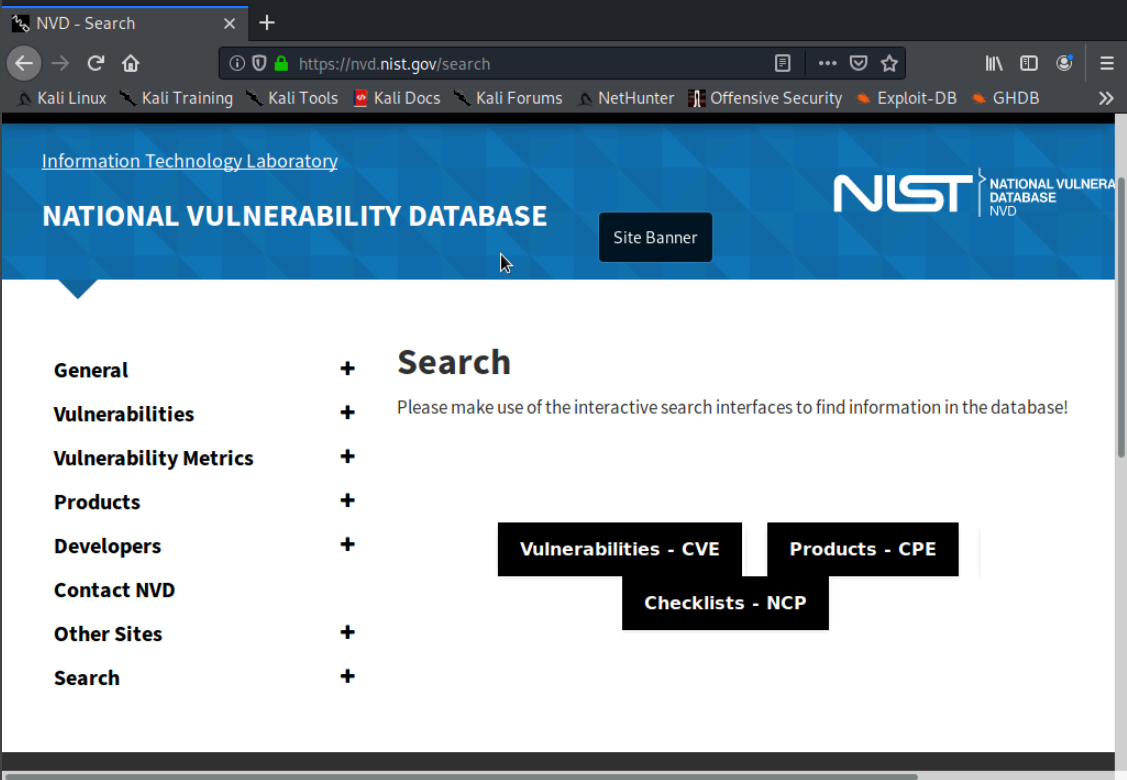
We'll click on the Vulnerabilities - CVE button and then scroll down and type vsftp in the keyword search. When we scroll down, we the first CVE is CVE-2011-2523, which we saw previously in our Exploring OpenVAS lab.
After clicking on CVE-2011-2523 we can see that this CVE was published on 11/27/19 and the severity score is 9.8.
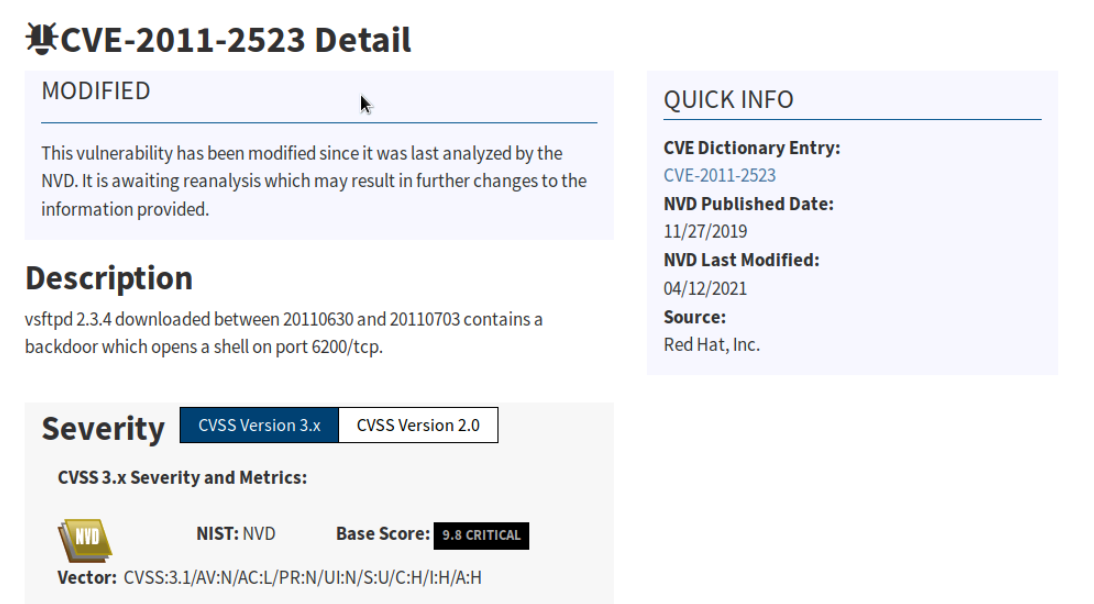
While the National Vulnerability Database doesn't provide code examples directly, many of the Hyperlinks under the "References to Advisories, Solutions, and Tools" section of the Details page do.
Public Exploit Sites - Exploit Database
The makers of Kali, Offensive Security, also provide the Exploit Database.
We'll use the broswer to navigate to https://www.exploit-db.com/ and type vsftp in the search bar.
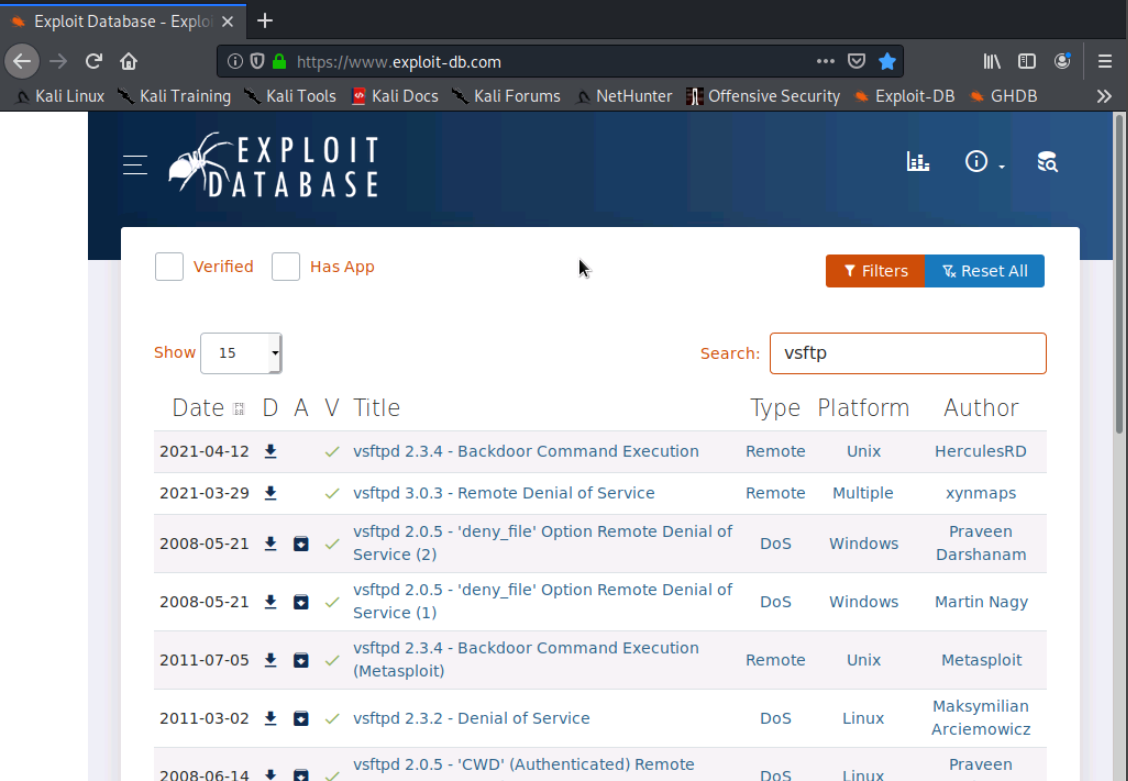
We'll click on the first link for the vsftpd 2.3.4 - Backdoor Command Execution to visit the page.
We see some similar information, including the CVE number, as we saw on the National Vulnerability Database. If we scroll down, we see a sample python script which can exploit this vulnerability.
A quick overview of the scripts follows. The initial section with all the #'s characters are comments describing the script. The next block with the from and import statements imports some libraries for use by the script. The next part defines a handler to handle the script functions. The next sections down to the defining of the user and password variables sets up functions and variables for the script to use. The second to last block actually connect to the FTP server and attempts to login. The last block connects to the newly open backdoor on port 6200.
This in effect just what we did manually with telnet or via the Metasploit Framework, this time it is just being done in a Python script.
Metasploit Exploits
The Metasploit Framework, as we previously learned, comes with hundreds of exploits and modules. We will review their location and the structure of the file system and look in detail at the exploit for the VSFTP backdoor we used in a prevous lab.
Let's list the exploit code and modules in Metasploit that are located at: /usr/share/metasploit-framework/modules/
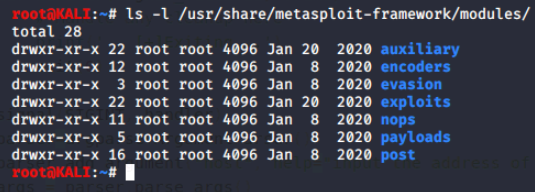
Let's dig a little deeper.
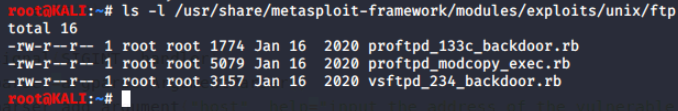
Digging even deeper still into more /usr/share/metasploit-framework/modules/exploits/unix/ftp/vsftpd_234_backdoor.rb.
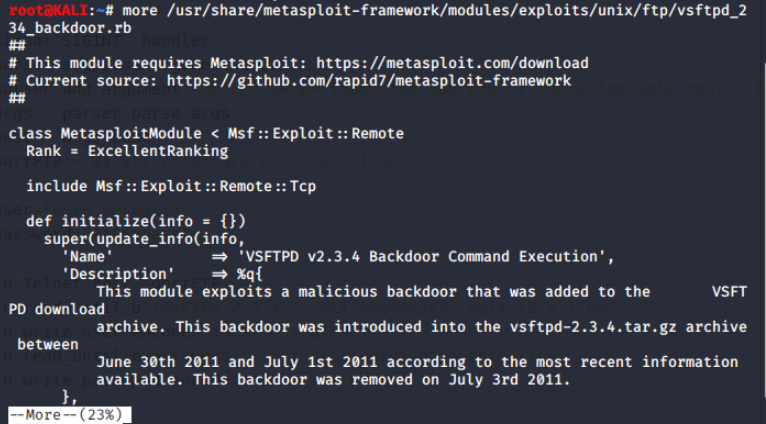
As with the previous script on the Exploit Database, let's review the sections:
- The first section is comments describing the script and noting that Metasploit is required. This makes sense as this is a Metasploit module.
- The next section running from class MetasploitModule to def exploit sets up the main functions and variable of the scripts.
- The next section sets up an error message if the backdoor port is already open. Otherwise it attempts to login into the FTP server and spawn the backdoor.
- The last section of the code connects to the newly open 6200 port.
This of course is very similar to how the Python based script from the Exploit Database works.
Conclusion
This lab was a great opportunity to analyze exploit code and understand how vulnerabilities can be exploited. We explored two important sources: the National Vulnerability Database (NVD) and the Exploit Database. By visiting these sites, we learned about real-world examples and the severity of different vulnerabilities.
Although the NVD didn't provide code examples directly, it offered useful references to advisories and solutions. On the other hand, the Exploit Database had more detailed information, including actual code samples. We focused on a specific vulnerability, CVE-2011-2523, and discovered its publication date and severity score.
We also delved into the Metasploit Framework, which is a powerful tool for exploiting vulnerabilities. By examining the VSFTP backdoor exploit, we gained a deeper understanding of how Metasploit works and how it can be used to exploit vulnerabilities.
0 Comments Add a Comment?